Docker Blog Series Part 4 - Managing Secrets inside Kubernetes Cluster in Azure Container Service
One of the common tasks in application development is to manage configurations. Some of the configurations can be sensitive information. One of the features of Kubernetes is secret management. There are many approaches to retrieve secrets from the secret management store. In this blog post, I will show you how to manage a sample secret using environment variables in a Web Api. We will do this in two steps. First step is to create the Kubernetes secrets. Second step is to leverage Kubernetes secrets in a Web Api. This blog assumes a successful deployment of a Kubernetes cluster in ACS. If you have not done this already, please follow the below link to deploy one. /en-us/azure/container-service/kubernetes/container-service-kubernetes-walkthrough
Let’s get started.
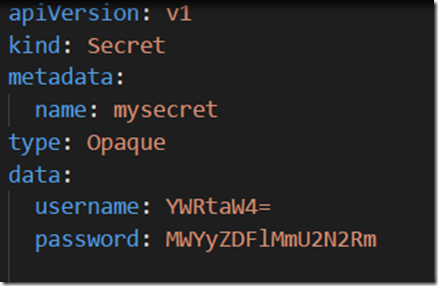
| Step 1. Create a secrets.yaml file with the below content. |
Step 2. Run the following Kubectl command to create Secret inside Kubernetes cluster.
kubectl.exe create -f "c:\secrets.yml"
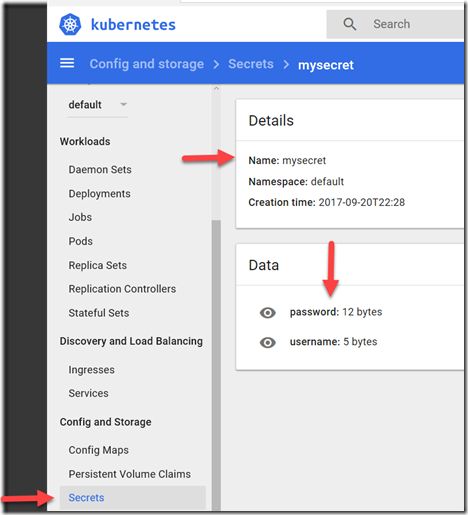
Step 3. Verify if the secret got created in the Kubernetes cluster by running the following command.
kubectl.exe get secrets
NAME TYPE DATA AGE
default-token-fp4cp kubernetes.io/service-account-token 3 9h
mysecret Opaque 2 2h
You can optionally check this in the Kubernetes UI/Dashboard as well.
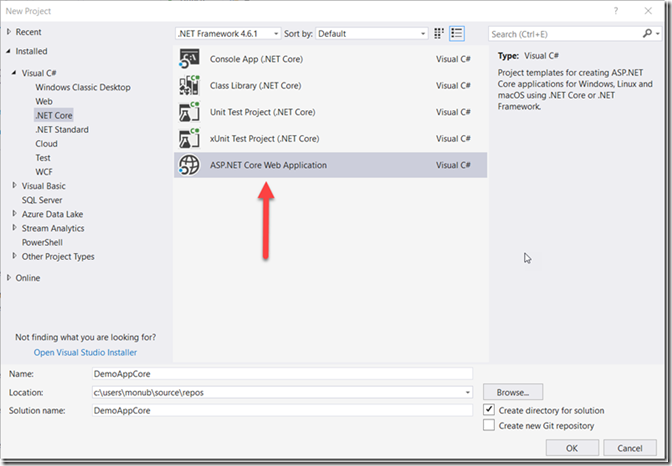
Now that we have the secret created, we will create an ASP.NET Core Web Api project to consume the secret as an environment variable.
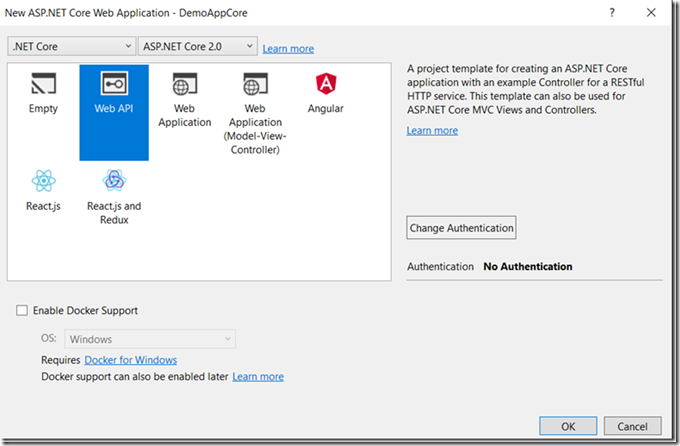
Step 4. Open Visual Studio 2017 and create ASP.NET Core Web Api project.
Step 5. Make the following change in Default Values Controller. We will be adding code to read Environment Variable called ‘Secret_Username’. This value will be coming from the Secrets inside the Kubernetes cluster.
public string Envar { get; set; }
// GET api/values
[HttpGet]
public IEnumerable<string> Get()
{
if (Environment.GetEnvironmentVariable("SECRET_USERNAME") != string.Empty)
Envar = Environment.GetEnvironmentVariable("SECRET_USERNAME");
else
Envar = "Environment Variable could not be read from Kubernetes Secrets";
return new string[] { "Here is the secret username", " " + Envar };
}
Step 6. Add a Dockerfile to the project, Build the Dockerfile and push this application to the Docker Hub or an equivalent Docker Repository. If you need help with Dockerizing the app, read my earlier blog posts.
Step 7. Now let’s push this application to Kubernetes cluster to retrieve the Secret value. We will use kubectl create command to create the deployment. Service.yaml is the yaml file which describes the Kubernetes deployment. To understand more about Kubernetes deployment, read the documentation here - https://kubernetes.io/docs/tutorials/kubernetes-basics/deploy-intro/
kubectl.exe create –f Service.yaml 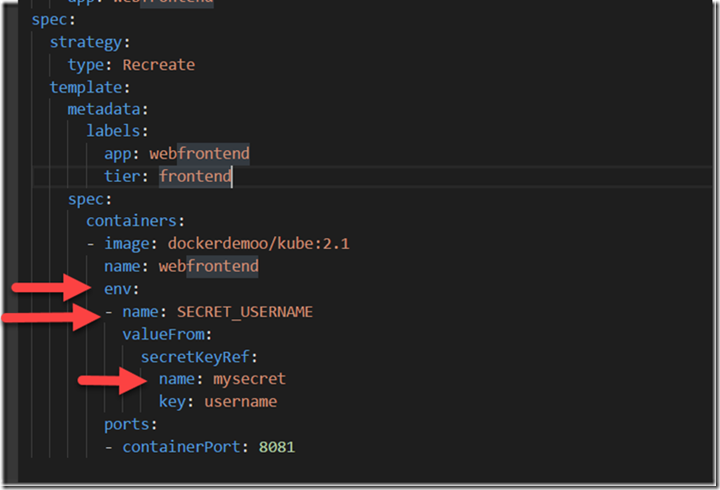
The important part to understand here is how we describe the Environment variable and map it to the valueFrom the secret store using SecretKeyRef.
Step 8. Once the application is deployed to the Kubernetes cluster, your values controller should be able to access the ‘Secret_UserName’ in the Values Controller from the secret store using the environment variable ‘Secret_UserName’.
In this blog post, we saw one of the ways to manage secrets in Kubernetes.. Stay tuned for more!!!