From the MVPs: Setting Internet Explorer Trusted Site Settings via Group Policy Object in Windows Server 2012 R2
This is the 39th in our series of guest posts by Microsoft Most Valued Professionals (MVPs). You can click the “MVPs” tag in the right column of our blog to see all the articles.
Since the early 1990s, Microsoft has recognized technology champions around the world with the MVP Award . MVPs freely share their knowledge, real-world experience, and impartial and objective feedback to help people enhance the way they use technology. Of the millions of individuals who participate in technology communities, around 4,000 are recognized as Microsoft MVPs. You can read more original MVP-authored content on the Microsoft MVP Award Program Blog .
This post is by Windows Expert – IT Pro MVP Philippe Levesque . Thanks, Philippe!
Today I will talk about setting up trusted sites via Group Policy Objects (GPOs) in Windows Server 2012 R2
Seem like an easy topic, but if you have never done this before it is important to do so the correct way to avoid problems down the road.
The first method is fairly straightforward.
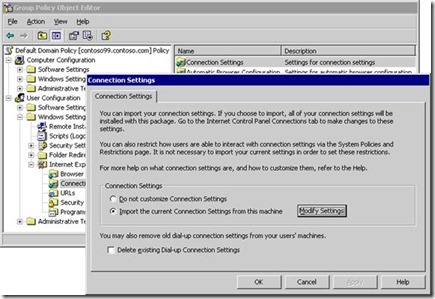
First Method: Internet Explorer Maintenance. Wait, where is it in Windows Server 2012 R2? ( Appendix B: Replacements for Internet Explorer Maintenance or see that link for further reading Missing Internet Explorer Maintenance settings for Internet Explorer 11 )
(Figure from there: How Internet Explorer Maintenance Extension Works)
So, if you are migrating a Windows Server 2008 R2's domain to Windows Server 2012 R2, be advised to replace those GPOs that use the Internet Maintenance Options.
The PRO of that Method:
- Easy to edit.
The CON of that Method:
- For adding only one trusted site, you will finish with all Internet Settings (including Zone Setting).
When deployed that way those settings get burned in the user profile, thus even if you remove the GPO, it will leave a lot of settings behind. That is the greatest drawback of these methods, as it's hard to remove any error in the settings. Be advised that method can bring problem if you edit it with a version of Internet Explorer not the same as the client computers. If you edit it when Internet Explorer is in Enhanced Security mode, then the target Internet Explorer will inherit those settings.
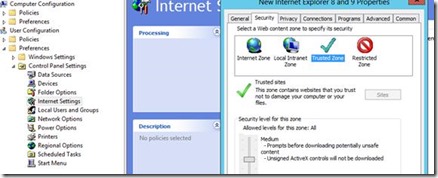
Second method: User Configuration->Preferences->Control Panel Settings->Internet Settings... Oh wait again, it's unavailable.
The correct step is this way: User Configuration > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page
“Site to Zone Assignment List” , click “Enable” and edit the list.
Add the site and the number two for Trusted Site. (1 = Intranet, 2 = trusted sites, 3 = Internet Zone and 4 = Restricted Site Zone.
To have a list like that (2 is for trusted site)
*.hotmail.com 2
*.outlook.com 2
*.bing.com 2
The PRO of that method:
- It standardizes all domain-joined computers as they will use the same list for everyone.
- It blocks users from entering new trusted sites. Though this can be a con for small offices or for Power Users wanting more autonomy.
The CON of this method:
- It block user for entering new trusted sites. This can be considered a PRO in big offices, as the list is standardized by the IT's team.
After performing these steps, if your users receive this warning “The current webpage is trying to open a site on your intranet. Do you want to allow this? ” when they navigate from the Internet Zone to the Trusted zone. You can tweak the behaviour with a simple registry key with the Windows preference.
HKEY_LOCAL_MACHINE \SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2
Value Name: 2101 Value Type: REG_DWORD Value: 0x0 (0)
Official description of the setting: This policy setting allows you to manage whether Web sites from less privileged zones, such as Restricted Sites, can navigate into this zone. If you enable this policy setting, Web sites from less privileged zones can open new windows in, or navigate into, this zone. The security zone will run without the added layer of security that is provided by the Protection from Zone Elevation security feature. If you select Prompt in the drop-down box, a warning is issued to the user that potentially risky navigation is about to occur. If you disable this policy setting, the possibly harmful navigations are prevented. The Internet Explorer security feature will be on in this zone as set by Protection from Zone Elevation feature control. If you do not configure this policy setting, a warning is issued to the user that potentially risky navigation is about to occur.
For a complete list of registry key versus the GPO list please see that link: Group Policy Settings Reference for Windows and Windows Server
Thanks everyone!
Philippe Lévesque
MVP Windows Expert-IT Pro