New book: Team Collaboration: Using Microsoft Office for More Effective Teamwork
We are happy to announce that Team Collaboration: Using Microsoft Office for More Effective Teamwork (ISBN 9780735669628) by John Pierce is now available for purchase!
Set the stage for more effective collaboration in your organization using Microsoft Office. Whether coordinating a cross-team project or leading your workgroup, you’ll discover how to combine your skills with Office programs with best practices for enabling your team’s best work.
Apply expert insights for increasing the collaboration power of teams and groups
Take advantage of the collaboration features in Microsoft Word ,Excel, PowerPoint, Outlook, and OneNote to manage shared work and communications
Learn ways to use Microsoft SharePoint to enable teamwork
Team Collaboration: Using Microsoft Office for More Effective Teamwork is intended for individuals and groups who want to know how to use Microsoft Office to facilitate the work they do as a team. In this context, “team” could mean a small business (say, 5 to 12 people), a department within a larger organization,
a project team made up of individuals from several different departments, or a group of independent contractors working together on one or more
projects.
Here is a bit of content from Chapter 3.
Chapter 3
Managing access and
preserving history
COLLABORATIVE WORK IS often facilitated through approaches
that don’t enforce rigorous structures. Brainstorming sessions serve this
purpose, of course, where some or all of a team’s members gather to generate ideas about future work, exchange ideas about what processes
can be improved, or outline solutions to particularly difficult problems that keep coming up. In Part 2 of this book, you’ll learn how Microsoft
Lync supports various types of informal (and formal) communication that let teams exchange ideas in these ways and how teams can use a
Microsoft OneNote notebook as a kind of ad hoc repository for recording all types of content and ideas.
See Also For more details, see Chapter 6, “Working together in
Lync,” and Chapter 7, “Keeping track of discussions and ideas.”
In this chapter, you’ll learn more about procedures and controls that teams can put in place to manage content they produce. Procedures
such as these ensure that the formal processes, decisions, and finalized content that are born from practices such as brainstorming
are applied and retained. Although the idea of applying “controls” can sometimes sound exclusionary (even punitive), that
isn’t the intent. The types of restrictions and controls described in this chapter help protect sensitive and potentially valuable information,
set up processes to ensure that team members work with content that’s complete, and help teams track and classify the files
they use. In addition, restricting access to files and allowing only some team members to view documents that are still in draft form helps team members
with expertise in certain areas (legal, financial, sales, engineering, and others) work without concern that the information they are preparing will be mistakenly distributed or
modified before final versions are reviewed and approved.
This chapter also builds on some of the concepts you learned about in Chapter 2, “Building a SharePoint team site.”
In the last two major sections of this chapter, I’ll expand on how you can use a document library to keep track of and manage content. To start
the chapter, I’ll describe some of the basic ways in which you can control access to and protect Office documents. You saw in Chapter 2 how to use groups and permission levels
to manage a team site in SharePoint. Those permissions go a long way toward managing which team members can work on documents and what they can do, but some of
a team’s work will inevitably take place on documents that don’t take advantage of the structure of the team site. In these cases, you can use tools like passwords and rights
management to control access to documents.
Protecting Office documents
When teams work with sensitive and confidential information, they can use rights management
to manage access to files and e-mail messages and to control what users can do with a file.
Rights management restricts permissions to a file to prevent unauthorized access and
distribution. For example, you can apply rights management to documents that you
don’t want everyone on your team to forward, copy, or print. Permissions you set up by
using rights management are stored with the file, which means that the restrictions you
apply are in effect whether the file is stored in a SharePoint document library, in an Outlook
message store, or on a network drive, for example.
A simpler approach to protecting documents—but one without the degree of control
offered by rights management—is to protect files with a password. In Microsoft Word,
Excel, and PowerPoint, you can define a password that’s required to open a file and a different
password that’s needed to modify it.
Specific applications also include capabilities for protecting the data and formatting
in files. In Chapter 8, “Working on shared documents in Word,” you’ll learn the steps
involved when you want to restrict the formatting and editing of a document. Later in
this section, I’ll describe similar steps you can take to protect workbooks and worksheets
in Excel.
First, I’ll describe the protections offered by rights management.
Using rights management
Rights management helps teams and organizations enforce policies that control the
copying and distribution of confidential or proprietary information. Rights are assigned
to content when it is published, and the content is distributed in an encrypted form that
provides protection wherever the content resides. In other words, a document that’s
protected with rights management carries that protection whether it is opened from
SharePoint, SkyDrive, a network share, or as an e-mail attachment.
Some of the restrictions you can impose by applying rights management are the
following:
■ Prevent an authorized recipient of restricted content from forwarding, copying,
modifying, printing, faxing, or pasting the content
■ Prevent restricted content from being copied by using the Print Screen key
■ Define a file expiration date so that content in documents, workbooks, or presentations
can no longer be viewed after the specified period of time
You can apply rights management by using a template or through user-defined rights.
For the Office 2013 Preview, Microsoft provided templates such as the Company Confidential
template and the Company Confidential Read Only template. With the Company
Confidential template, users of the content are allowed all rights needed to work with
and modify the content but are not permitted to copy and print the content. With the
Company Confidential Read Only template, users can only read or view the content but
are not permitted to modify the content from its original published form. If you need a
higher degree of control, you can apply permissions manually by defining user-defined
rights.
To apply rights management to a file you are working with in PowerPoint, Excel, or Word,
you work on the Info page in Backstage view. Use the Protect Presentation, Protect
Workbook, or Protect Document command, depending on which program you’re working
with. In a message item in Outlook, click Set Permissions on the Info page.
You can also enable rights management for a list or library on your SharePoint team site.
You might take this step to protect the content in a document library that’s set up to
store the specifications for new products or other valuable intellectual property. When
rights management is applied to a library, it applies to all the files in that library. For a
list, rights management applies only to files that are attached to list items, not to the list
items themselves.
When a team member downloads a file from a list or library protected with rights
management, the file is encrypted so that only authorized people can view it. Additional
restrictions can be applied to users who can view the file. For documents in lists and
libraries (as for documents you apply rights management to directly), these restrictions
include making a file read-only, disabling the copying of text, preventing people from
saving a local copy, and preventing people from printing the file.
The restrictions that are applied to a file when it is downloaded are based on the individual
user’s permissions on the site that contains the file. For example, a site owner can
generally work with a file to edit it, copy it, or modify how rights management is applied.
A team member with Edit Items permission for a library can edit, save, and copy the file,
but these users cannot print the file unless specifically granted that permission.
To apply rights management to a list or library, you must have at least the Design permission
level for that list or library. If you have that level of permission, follow these steps:
1. Open the list or library.
2. On the Library tab (or List tab for a list), click Library Settings ( or List Settings).
3. Under Permissions and Management, click Information Rights Management.
4. On the Information Rights Management Settings page, select the Restrict Permission
To Documents In This Library On Download option.
5. In the Create A Permission Policy Title box, type a descriptive name. For example,
you might use the name Team Confidential for a policy that applies to a list or
library that will contain documents that are confidential within your team.
6. In the Add A Permission Policy Description box, type a description that explains
to team members who use this list or library how they should handle protected
content. For example, use a description such as “Only discuss with members of the
team.”
7. To apply additional restrictions to the documents in this list or library, click Show
Options. You can then select exceptions such as allowing some team members to
print a document. You can also set an option that prevents team members from
uploading documents that don’t support rights management to the list or library.
Using a password
When you save a file in Word, Excel, or PowerPoint, you can assign a password that other
users need to enter to open or modify the document. In all three programs, open the
Tools menu in the Save As dialog box and then click General Options to open the dialog
box where you define the passwords.
Some additional options are included for each program:
■ In Excel, you can select an option to always create a backup of the workbook or an
option to prompt users to open the file as read-only.
■ In Word, you also have the Read-Only Recommended option. The Protect Document
button opens the Restrict Formatting And Editing pane, which you'll learn
about in detail in Chapter 8.
■ In PowerPoint, the General Options dialog box includes the Privacy Options area.
The option Remove Automatically Created Personal Information From This File On
Save controls whether PowerPoint removes or retains information such as the presentation
author and other properties. You'll learn more about document properties
later in this chapter.
The Info page also provides an option for applying a password that encrypts the contents
of the current file. To encrypt an Excel workbook with a password, follow these
steps (the steps in Word and PowerPoint are similar):
1. Click File, Info.
2. On the Info page, click Protect Workbook and then click Encrypt With
Password.
3. In the Encrypt Document dialog box, type the password you want to use and
then click OK.
68 Chapter 3 Managing access and preserving history
4. Reenter the password.
Be sure to take note of the warning in the dialog box about lost passwords: you
can’t recover them. Be sure to record the password in a safe place so that you can
provide it to other users or refer to it yourself in the event you forget the password.
5. Click OK, and then save the workbook.
PREPARING TO SHARE A FILE
The Inspect Workbook area on the Info page provides three commands on the
Check For Issues menu. The Check For Accessibility and Check For Compatibility
commands apply in specific situations—when you want to know which elements
of a document, workbook, or presentation could pose issues for people with
disabilities, and when you want to know whether any features in a file aren’t supported
in earlier versions of a program.
You should make regular use of the third command—Inspect Document—before
you distribute files to customers or partners, for example, or share a file with
colleagues who aren’t regular members of your team. You’ll see an example of
how you use the Document Inspector in PowerPoint in Chapter 10, “Preparing a
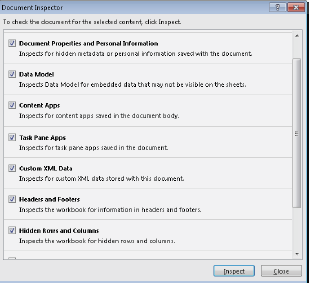
presentation as a group.” Figure 3-1 shows the Document Inspector for Excel.
In general, you can use the Document Inspector to detect elements in a file that
you might want to remove or revise before you share the file. As you can see,
one category for Excel is Hidden Rows And Columns. Imagine that you enter
worksheet formulas that calculate the markup on a set of products or services or
formulas related to performance bonuses or new salary ranges. If you hide these
cells to focus on the results of the formulas—which users of Excel often do—it’s
easy to overlook the fact that you hid them later, or someone else getting ready
to post the file might not realize that the formulas are contained in a hidden column
or row. Inspecting a document will indicate that the workbook has hidden
rows or columns. If you don’t want to share the formulas with other users, you
can return to the worksheet and convert the calculated values to static values, for
example, or you might decide to keep the rows or columns hidden and save the
workbook as a PDF file. For more details about saving a workbook as a PDF file,
see “Creating a PDF/XPS document” in Chapter 9, “Collaborating in Excel.”
FIGURE 3-1 The Document Inspector can find content and properties
you don’t necessarily want to share.
Protecting workbooks and worksheets
In this section, I’ll cover some specific steps you can take to protect the data and structure
of Excel workbooks and worksheets. Because teams use Excel to compile and analyze
financial data, these procedures are often applicable. These protections serve several
purposes: they can retain the structure of a workbook, for example, or restrict which
operations some users can perform. You can also specify editable cell ranges and protect
the rest of a worksheet so that it is read-only. The intent of applying these restrictions
has as much to do with preserving the work that team members did to construct specific
financial scenarios or complex formulas as it does with limiting what other team members
can do.