New book: Windows Server 2012 Pocket Consultant
We are happy to announce the availability of the Windows Server 2012 Pocket Consultant (ISBN 9780735666337) by William R. Stanek. William has done it again! Here is a concise and practical guide to the latest release of Windows Server. He covers the bases, including how Windows Server 2012 works with the new touch UI-capable computers. This books covers what you need to know to customized you server installations, master Windows Server 2012 configurations, and maintain you Windows Server 2012 servers.
You can purchase your copy here or here.
Here’s a preview:
CHAPTER 3
Monitoring Processes, Services, and Events
As an administrator, you need to keep an eye on network systems. The status and usage of system resources can change dramatically over time. Services might stop running. File systems might run out of space. Applications might throw exceptions that, in turn, can cause system problems. Unauthorized users might try to break into the system. The techniques discussed in this chapter can help you identify and resolve these and other system problems.
Managing Applications, Processes, and Performance
Any time you start an application or type a command at the command line, Microsoft Windows Server starts one or more processes to handle the related program. Generally, processes you start in this manner are called interactive processes—that is, you start the processes interactively with the keyboard or mouse. If the application or program is active and selected, the interactive process has control over the keyboard and mouse until you switch control by terminating the program or selecting a different one. When a process has control, it’s said to be running in the foreground.
Processes can also run in the background. For processes started by users, this means that programs that aren’t currently active can continue to operate, only they generally aren’t given the same priority as active processes. You can also configure background processes to run independently of the user logon session; the operating system usually starts such processes. An example of this type of background process is a scheduled task run by the operating system. The configuration settings for the task tell the system to execute a command at a specified time.
Task Manager
The key tool you use to manage system processes and applications is Task Manager. You can use any of the following techniques to display Task Manager:
■ Press Ctrl+Shift+Esc.
■ Press Ctrl+Alt+Del, and then tap or click Task Manager.
■ Press the Windows key, type taskmgr, and then press Enter.
■ Press and hold or right-click the taskbar, and then tap or click Task Manager on the shortcut menu.
NOTE When you press the Windows key and type taskmgr, you’ll see two matches. One match is the full name, Task Manager. The other match is the command name, taskmgr.
The following sections cover techniques you use to work with Task Manager.
Viewing and Working with Processes
Task Manager has two general views:
■ Summary Shows only applications running in the foreground, which lets you quickly select and work with foreground applications
■ Expanded Expands the view, providing additional tabs that you can use to get information about all running processes, system performance, connected users, and configured services
If you are in summary view, you can switch to expanded view by tapping or clicking More Details. If you are in the expanded view, you can switch to summary view by tapping or clicking Fewer Details. When you close and reopen Task Manager, the view that you last used is displayed.
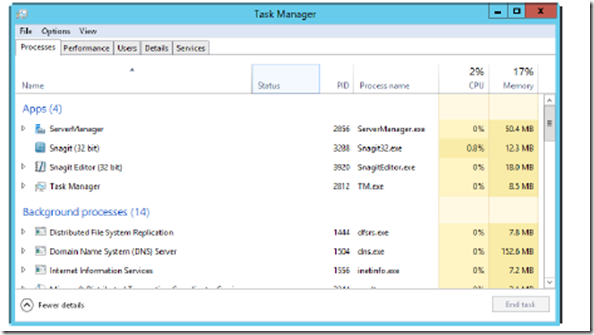
Generally, as an administrator, you’ll work with the expanded view. As shown in Figure 3-1, the expanded view has multiple tabs you can select to work with running processes, system performance, connected users, and configured services. The Processes tab, also shown in Figure 3-1, shows the general status of processes. Processes are grouped by type and listed alphabetically within each type by default. There are three general types:
■ Apps, which are programs running in the foreground
■ Background processes, which are programs running in the background
■ Windows processes, which are processes run by the operating system
NOTE The Group By Type option on the View menu controls whether grouping is used. If you clear this option, all processes are listed alphabetically without grouping by type. Note also that you can start a new program from within Task Manager by tapping or clicking Run New Task on the File menu and then entering a command to run the application. Options are included for running the task with Administrator privileges and for browsing to find the executable you want to work with.
FIGURE 3-1 View the status of processes currently running on the server.
REAL WORLD Many Windows processes also are grouped by the service host they are running under, which can include Local Service, Local System, and Network Service. The number of grouped processes is shown in parentheses, and you can expand the related node to view the actual processes. Select Expand All on the View menu to expand all process groups for easy viewing.
The Status column tells you whether an application is running normally or has stopped responding. A blank status is normal and indicates the process is running normally. Any other status indicates a problem, such as when an application might be frozen and you might want to end the task related to it. However, some applications might not respond to the operating system during certain process-intensive tasks. Because of this, you should be certain the application is really frozen before you end its related task.
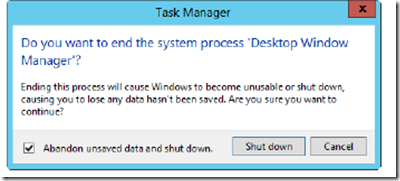
You can stop a process by selecting the process and then tapping or clicking End Task. You shouldn’t try to stop Windows processes using this technique. If you try to stop a Windows process or a group of Windows processes, Task Manager displays a warning prompt similar to the one shown in Figure 3-2. This warning states that ending this process will cause Windows to become unusable or to shut down. To proceed, you must select Abandon Unsaved Data And Shut Down and then tap or click Shut Down. Windows then displays a blue screen with an error code. After collecting error information, Windows will restart.
FIGURE 3-2 Stopping processes for essential Windows services causes Windows to become unusable or to shut down.
Other columns on the Processes tab provide a lot of information about running processes. You can use this information to determine which processes are over consuming system resources such as CPU time and memory. Although only CPU and Memory columns are displayed by default, others columns can be added by pressing and holding or right-clicking any column header and then selecting options for the additional columns to display. In addition to name and status, the other available columns include the following:
■ CPU The percentage of CPU utilization for the process (across all cores). The bold value in the column header represents the total CPU utilization for the server (across all cores).
■ Memory The total physical memory reserved for the process. The bold value in the column header represents the total physical memory utilization for the server.
■ Command Line The full file path to the executable running the process, as well as any command-line arguments passed in when the process was started.
■ PID The numeric identifier for the process.
■ Process Name The name of the process or executable running the process.
■ Publisher Lists the publisher of the process, such as Microsoft Corporation.
■ Type Displays the general process type as app, background process, or Windows process. This information is useful if you clear the Group By Type option on the View menu.
Pressing and holding or right-clicking an application’s listing in Task Manager displays a shortcut menu you can use to do the following:
■ End the application’s task
■ Create a dump file for debugging the process
■ Go to the related process on the Details tab
■ Open the file location for the related executable
■ Open the Properties dialog box for the related executable
NOTE The Go To Details option is very helpful when you’re trying to find the primary process for a particular application. Selecting this option highlights the related process on the Details tab.
Administering Processes
Task Manager’s Details tab is shown in Figure 3-3. This tab provides detailed information about the processes that are running. The columns displayed by default on the Details tab are similar to those provided on the Processes tab:
■ Name The name of the process or executable running the process
■ User Name The name of the user or system service running the process
■ CPU The percentage of CPU utilization for the process
■ Memory (Private Working Set) The amount of physical memory reserved by the process
■ Status The run status of the process
■ Description A description of the process
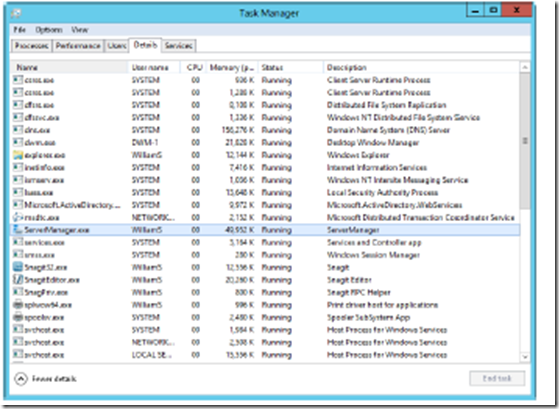
FIGURE 3-3 The Details tab provides detailed information about running processes.
Other columns can be added by pressing and holding or right-clicking any column header and then tapping or clicking Select Columns. When you’re trying to troubleshoot system problems using process information, you might want to add the following columns to the view:
■ Base Priority Priority determines how much of the system’s resources are allocated to a process. To set the priority for a process, press and hold or right-click the process, choose Set Priority, and then select the new priority
92 Chapter 3 Monitoring Processes, Services, and Events from these options: Low, Below Normal, Normal, Above Normal, High, and RealTime. Most processes have a normal priority by default. The highest priority is given to real-time processes.
■ CPU Time The total amount of CPU cycle time used by a process since it was started. To quickly see the processes that are using the most CPU time, display this column and then tap or click the column header to sort process entries by CPU time.
■ Data Execution Protection Specifies whether DEP is enabled or disabled for the process.
■ Elevated Specifies whether the process is running with elevated, administrator privileges.
■ Handles The total number of file handles maintained by the process. Use the handle count to gauge how dependent the process is on the file system. Some processes, such as those used by Microsoft Internet Information
Services (IIS), have thousands of open file handles. Each file handle requires system memory to be maintained.
■ I/O Reads, I/O Writes The total number of disk input/output (I/O) reads or writes since the process was started. Together, the number of I/O reads and writes tells you how much disk I/O activity has occurred. If the number
of I/O reads and writes is growing disproportionately to actual activity on the server, the process might not be caching files or file caching might not be properly configured. Ideally, file caching reduces the need for I/O reads and writes.
■ Page Faults A page fault occurs when a process requests a page in memory and the system can’t find it at the requested location. If the requested page is elsewhere in memory, the fault is called a soft page fault. If the
requested page must be retrieved from disk, the fault is called a hard page fault. Most processors can handle large numbers of soft faults. Hard faults, however, can cause significant delays.
■ Paged Pool, NP Pool Paged pool is an area of system memory for objects that can be written to disk when they aren’t used. NP pool, or nonpaged pool, is an area of system memory for objects that can’t be written to disk.
You should note processes that require a large amount of nonpaged pool memory. If there isn’t enough free memory on the server, these processes might be the reason for a high level of page faults.
■ Peak Working Set The highest amount of memory used by the process. The change, or delta, between current memory usage and peak memory usage is important to note as well. Applications that have a high delta between base memory usage and peak memory usage, such as Microsoft SQL Server, might need to be allocated more memory on startup so that they perform better.
■ Platform Specifies whether the process is running on the 64-bit or 32-bit platform. Windows 64-bit editions support both 64-bit and 32-bit applications using the Windows on Windows 64 (WoW64) x86 emulation layer. The
WoW64 subsystem isolates 32-bit applications from 64-bit applications. This prevents file-system and registry problems. The operating system provides interoperability across the 32-bit/64-bit boundary for the Component Object Model (COM) and for basic operations. However, 32-bit processes cannot load 64-bit dynamic-link libraries (DLLs), and 64-bit processes cannot load 32-bit DLLs.
■ Process ID (PID) The numeric identifier for the process.
■ Session ID The identifier for the session under which the process is running.
■ Threads The current number of threads the process is using. Most server applications are multithreaded. Multithreading allows concurrent execution of process requests. Some applications can dynamically control the number of concurrently executing threads to improve application performance. Too many threads, however, can actually reduce performance because the operating system has to switch thread contexts too frequently.
■ UAC Virtualization Indicates whether User Account Control (UAC) virtualization is enabled, disabled, or not allowed in the process. UAC virtualization is needed for legacy applications written for Windows XP, Windows Server 2003, and earlier releases of Windows. When UAC virtualization is enabled for these applications, error notifications and error logging related to virtualized files and registry values are written to the virtualized location rather than the actual location to which the process was trying to write. If virtualization is required but disabled or not allowed, the process will silently fail when trying to write to protected folders or protected areas of the registry.
If you examine processes running in Task Manager, you’ll notice a process called System Idle Process. You can’t set the priority of this process. Unlike processes that track resource usage, System Idle Process tracks the amount of system resources that aren’t used. Thus, a 99 in the CPU column of the System Idle Process means that 99 percent of system resources currently aren’t being used.
Processes that are waiting to use a resource that is locked by another process are in a wait state and can continue only when the locked resource is released. As part of normal operations, resources are locked for one process or another and then released to be used by another process. Sometimes, though, with poorly architected programs, a process can get stuck waiting for a resource that never gets released.
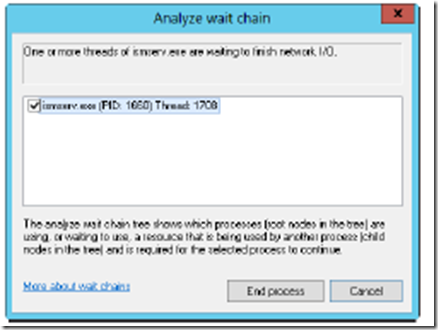
You can view the wait chain for processes by pressing and holding or right-clicking the process and then tapping or clicking Analyze Wait Chain. If the process is waiting for a resource to be released, you then see the wait chain for that process (as shown in Figure 3-4). The root node in the wait tree is the process using, or waiting to use, the required resource. A process waiting on another process for a resource might explain why a process doesn’t seem as responsive as you might expect.
If you suspect there’s a locking problem, you can select one or more processes in the wait chain and then tap or click End Process. Task Manager then stops the processes, which should free the locked resource. However, keep in mind that it is routine and normal for processes to lock resources while they are being used and free them when done. A problem occurs when a process fails to release a resource, as can happen with a poorly architected program.
FIGURE 3-4 Analyzing wait chains.
As you examine processes, keep in mind that a single application might start multiple processes. Generally, these processes are dependent on a central process. From this main process, a process tree containing dependent processes is formed. You can find the main process for an application by pressing and holding or right-clicking the application on the Processes tab and selecting Go To Details. When you terminate processes, you’ll usually want to target the main application process or the application itself rather than dependent processes. This ensures that the application is stopped cleanly.
To stop the main application process and dependent processes, you have several choices:
■ Press and hold or right-click the application on the Processes tab, and then tap or click End Task.
■ Press and hold or right-click the main application process on the Details tab, and then tap or click End Task.
■ Press and hold or right-click the main or a dependent process on the Processes tab, and then tap or click End Process Tree.
Viewing System Services
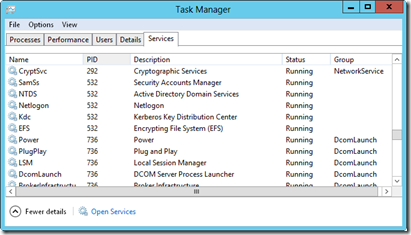
Task Manager’s Services tab provides an overview of system services. This tab displays services by name, process ID, description, status, and group. As shown in Figure 3-5, multiple services typically run under the same process ID. You can quickly sort services by their process ID by tapping or clicking the related column heading. You can tap or click the Status column heading to sort services according to their
status, Running or Stopped.
The Group column provides additional options about related identities or service host contexts under which a service runs:
■ Services running under an identity with a restriction have the restriction listed in the Group column. For example, a service running under the Local Service identity might be listed as LocalServiceNoNetwork to indicate that
the service has no network access, or a service might be listed as LocalSystemNetworkRestricted to indicate that the service has restricted access to the network.
■ Services that have Svchost.exe list their associated context for the –k parameter. For example, the RemoteRegistry service runs with the command line svchost.exe –k regsvc. You’ll see an entry of regsvc in the Group column for this service.
FIGURE 3-5 The Services tab provides a quick overview of the status of system services.
Pressing and holding or right-clicking a service’s listing in Task Manager displays a shortcut menu that allows you to do the following:
■ Start a stopped service
■ Stop a started service
■ Go to the related process on the Details tab
Viewing and Managing System Performance
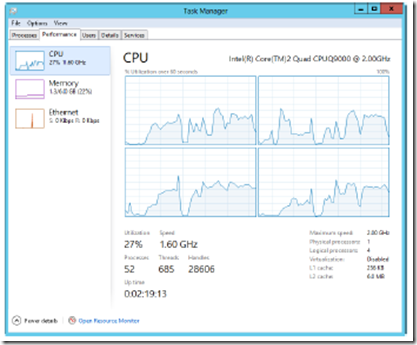
The Performance tab in Task Manager provides an overview of CPU and memory usage. As shown in Figure 3-6, the tab displays graphs and statistics. This information gives you a quick check of system resource usage. For more detailed information, use Performance Monitor, as explained later in this chapter.
The graphs on the Performance tab provide the following information:
■ CPU A graph of CPU usage plotted over time
■ Memory A graph of memory usage plotted over time
■ Ethernet A graph of network throughput plotted over time
Tap or click a summary graph in the left pane to view detailed information for that graph in the right pane. To view a close-up of any graph, double-tap or double-click the graph. Double-tapping or double-clicking again returns you to normal viewing mode.
The Update Speed option on the View menu allows you to change the speed of graph updating as well as to pause the graph. Updates occur once every 4 seconds for Low, once every 2 seconds for Normal, and twice per second for High.
FIGURE 3-6 The Performance tab provides a quick check of system resource usage.
CPU Usage: The Basics
When you select CPU, the % Utilization graph shows overall processor utilization for the last 60 seconds. If a system has multiple CPUs, you’ll see a graph for each CPU by default. You also can view logical processors or NUMA nodes by pressing and holding or right-clicking a CPU graph, selecting Change Graph To, and then selecting Logical Processors or NUMA Nodes as appropriate.
To view kernel times, press and hold or right-click a CPU graph and then select Show Kernel Times. Because usage by the kernel is plotted separately, you can more easily track the amount of CPU time used by the operating system kernel.
TIP Tracking the kernel usage can be handy for troubleshooting. For example, if you are using IIS with output caching in kernel mode, you can get a better understanding of how kernel caching might be affecting CPU usage and overall performance by showing kernel times. Kernel usage tracking isn’t enabled by default because it adds to the overhead of monitoring a server in Task Manager.
You can use the CPU information provided to quickly determine the up time for the server, the number of physical processors, the number of logical processors, whether hardware virtualization is enabled, and the amount of on-processor cache for each available register (L1, L2, L3). Keep the following in mind:
■ Handles shows the number of I/O handles in use; I/O handles act as tokens that let programs access resources. I/O throughput and disk performance affect a system more than a consistently high number of I/O handles.
■ Threads shows the number of threads in use; threads are the basic units of execution within processes.
■ Processes shows the number of processes in use; processes are running instances of applications or executable files.
■ Up Time shows how long the system has been up since it was last started.
If CPU usage is consistently high, even under average usage conditions, you might want to perform more detailed performance monitoring to determine the cause of the problem. Memory is often a source of performance problems, and you should rule it out before upgrading or adding CPUs. For more details, see “Tuning System Performance” later in this chapter.
Memory Usage: The Basics
When you select Memory, the Memory Usage graph shows overall usage of the private working set for the last 60 seconds. The Memory Composition histogram shows the following:
■ In-Use Memory The amount of memory being used by processes
■ Modified Memory The amount of memory whose contents must be written to disk before it can be used for another purpose
■ Standby Memory The amount of memory with cached data and code not actively being used
■ Free Memory The amount of memory that is not currently allocated for any purpose
NOTE You can use the memory information provided to quickly determine the speed of the memory, the number of memory slots used and available, and the memory form factor.
The total amount of physical RAM configured on the server is listed in the upper right corner when you are working with the memory graphs. Other memory statistics shown below the memory graphs provide the following information:
■ In Use Shows the amount of physical RAM that is in use on the server.
■ Available Shows the amount of physical RAM that is available for use (includes memory marked as standby and free). If a server has very little physical memory free, you might need to add memory to the system. In general, you want the free memory to be no less than 5 percent of the total physical memory on the server.
■ Committed Lists the virtual memory currently in use followed by the total amount of virtual memory available. If the current page file usage is consistently within 10 percent of the maximum value (meaning consistent usage of 90 percent or more), you might want to add physical memory, increase the amount of virtual memory, or take both steps.
■ Cached Shows the amount of memory used for system caching.
■ Paged Pool Provides information on noncritical kernel memory used by the operating system kernel.
■ Nonpaged Pool Provides information on critical kernel memory used by the operating system kernel.
Critical portions of kernel memory must operate in RAM and can’t be paged to virtual memory. Because of this, this type of kernel memory is listed as being in the nonpaged pool. The rest of kernel memory can be paged to virtual memory and is listed as being in the paged pool.
Network Usage: The Basics
When you select Ethernet, Task Manager provides an overview of the network adapters used by the system. You can use the information provided to quickly determine the percent utilization, link speed, and operational status usage of each network adapter configured on a system.
The name of the active network adapter in the Network Connections folder is shown in the upper right corner. If a system has one network adapter, the summary graph shows details of the network traffic on this adapter over time. If a system has multiple network adapters, the graph displays a composite index of all network connections, which represents all network traffic.
You can view detailed information on link speed, link state, bytes sent, bytes received, and more by pressing and holding or right-clicking the Network Throughput graph and selecting View Network Details. When working with network details, keep the following in mind:
■ Network Utilization Percentage of network usage based on the initial connection speed for the interface or the combined speed of teamed interfaces. For example, an adapter with an initial link speed of 10 gigabits
per second (Gbps) and current traffic of 100 megabits per second (Mbps) is utilized at 1 percent.
■Link Speed Connection speed of the interface as determined by the initial connection speed, such as 1 Gbps or 10 Gbps.
■ State Operational status of network adapters, such as Connected or Disconnected.
■ Bytes Sent Throughput Percentage of current connection bandwidth used by traffic sent from the system.
■ Bytes Received Throughput Percentage of current connection bandwidth used by traffic received by the system.
■ Bytes Throughput Percentage of current connection bandwidth used for all traffic on the network adapter.
■ Bytes Sent Cumulative total bytes sent on the connection to date.
■ Bytes Received Cumulative total bytes received on the connection to date.
■ Bytes Cumulative total bytes on the connection to date.
REAL WORLD Any time you see usage consistently approaching or exceeding 50 percent of total capacity, you should start monitoring the server more closely, and you might want to consider adding network adapters. Plan any upgrade carefully; a lot more planning is required than you might think. Consider the implications not only for that server but also for the network as a whole. You might also have connectivity problems if you exceed the allotted bandwidth of your service provider—it can often take months to obtain additional bandwidth for external connections.
Viewing and Managing Remote User Sessions
Remote users can use Remote Desktop to connect to remote systems. Remote Desktop allows you to administer systems remotely, as if you were sitting at the console. Windows Server 2012 allows up to two active console sessions at a time.
One way to view and manage remote desktop connections is to use Task Manager. To do this, start Task Manager and then tap or click the Users tab, shown in Figure 3-7. The Users tab shows interactive user sessions for both local and remote users.
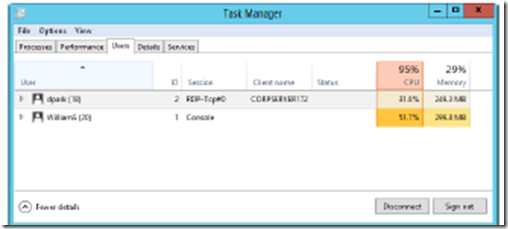
FIGURE 3-7 The Users tab allows you to view and manage user sessions.
Each user connection is listed with user name, status, CPU utilization, and memory usage by default. Other columns can be added by pressing and holding or right-clicking any column header and then tapping or clicking the columns to add. Available columns include
■ ID The session ID. The first logon has a session ID of 1. The second logon has an ID of 2.
■ Session The session type. A user logged on to the local system is listed with Console as the session type. Other users have a session type that indicates the connection type and protocol being used, such as RDP-TCP
for a connection using the Remote Desktop Protocol (RDP) with TCP as the transport protocol.
■ Client name For remote connections, lists the name of the originating client computer.
CPU and memory utilization details are new for Windows Server 2012 and really come in handy for troubleshooting performance issues related to logged-on users. The combined utilization value is listed above the column heading, and individual utilization values for each logged-on user are listed below it.
In the example shown in Figure 3-7, the server’s CPU is 95% utilized by the logged-on users. This high usage level could affect the overall performance of the server, and the server might not be as responsive when performing other tasks. If you press and hold or right-click a user session, you have the following options:
■ Connect Allows you to connect a remote user session if it’s inactive.
■ Disconnect Allows you to disconnect a local or remote user session, halting all user-started applications without saving application data.
■ Sign Off Allows you to log off a user using the normal logoff process. Application data and system state information are saved just as they are during a normal logoff.
■ Send Message Allows you to send a console message to a logged-on user.
Also new for Windows Server 2012, the user’s name is followed by the number of processes she is running. If you double-tap or double-click the user’s name, you see an entry for each running process. Processes are listed by name, CPU usage, and memory usage.