Windows Vista, ASLR, DEP and OEMs
As I mentioned in a previous series of posts, we recently had all the major OEMs on campus to discuss SDL and how we can work together. My big ask of the OEMs (actually, I grovelled, it was pathetic) was to enable DEP/NX in the BIOS by default on all their shipping PCs in time for Windows Vista.
The reason for this ask is pretty simple, for ASLR to be effective, DEP/NX must be enabled by default too.
Here's the good news, I found out yesterday that all the major OEMs (you know who they are!) have agreed to not disable DEP/NX in their BIOSs by default.
This is huge!
If you're an OEM reading this - THANKS!
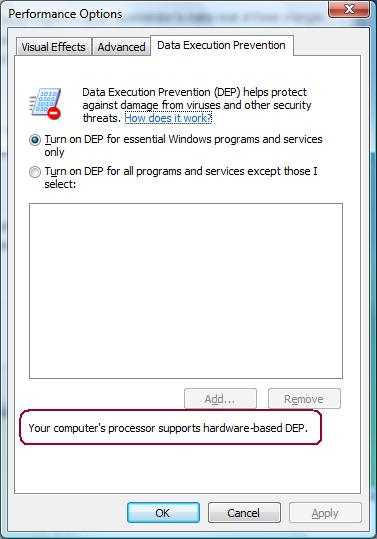
Note, you can verify if your PC has DEP enabled by following these steps.
- Open the Control Panel
- Select System & Maintenance
- Click System
- Click Advanced system Settings
- Click the Advanced tab
- Click Performance Settings
- Click the Data Execution Prevention tab
You should see the dialog box below. If not, check your BIOS and make sure your CPU is capable of DEP/NX, most CPUs these days support DEP/NX.