Exploring Dynamic Access Control Part 4 – Central Access Rules
In this series I have looked how we secure and classify resources (such as Files and Folders) with Dynamic Access Control with the claims of users and devices accessing them. In the previous post I looked at Resource Properties and User/Device Claims. In this post I will be bringing these concepts together with Central Access Rules.
Fitting everything together
As we have seen previously, the rules based on classifications also do not need to be configured for each resource individually, like the classification rules, we can create Central Access Rules which map the Resource's Properties and the User/Device Claims to determine access.
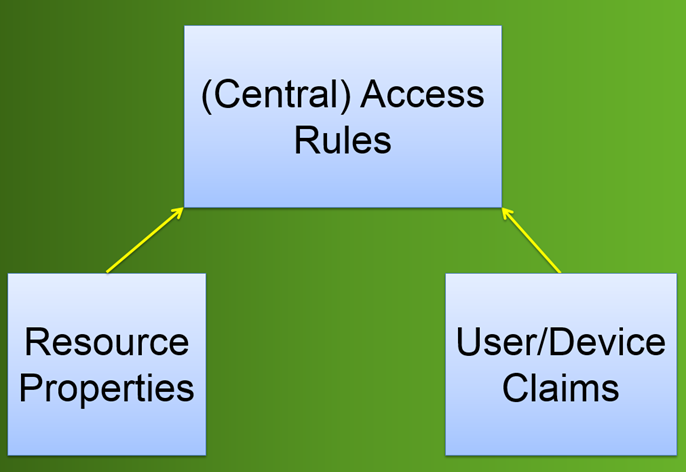
Central Access Rules
Now to tie the Resource Properties and Claims together. We are going to create a Central Access Rule, which looks a lot like the rule we saw in the basic example with a folder.
Again in the Active Directory Administrative Console, this time in Central Access Rules:
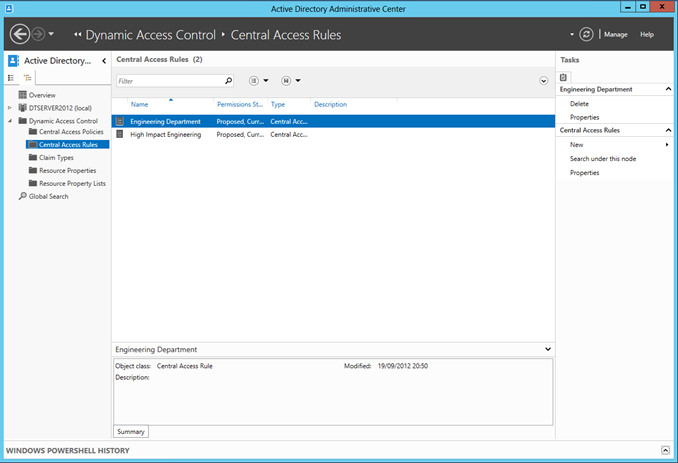
We can create a new rule, which again secures the Resources classified with Engineering as their Department Resource Property to the Users who's Department Claim is Engineering:
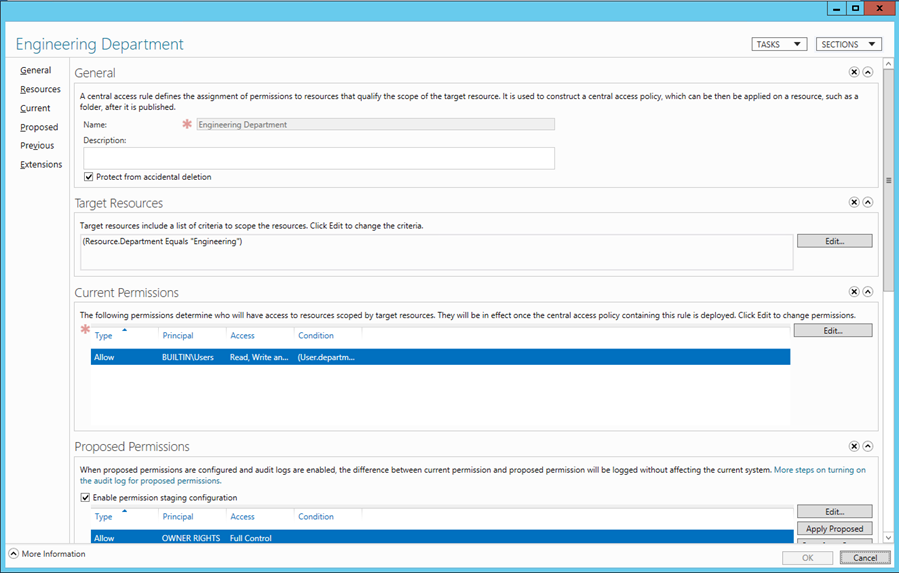
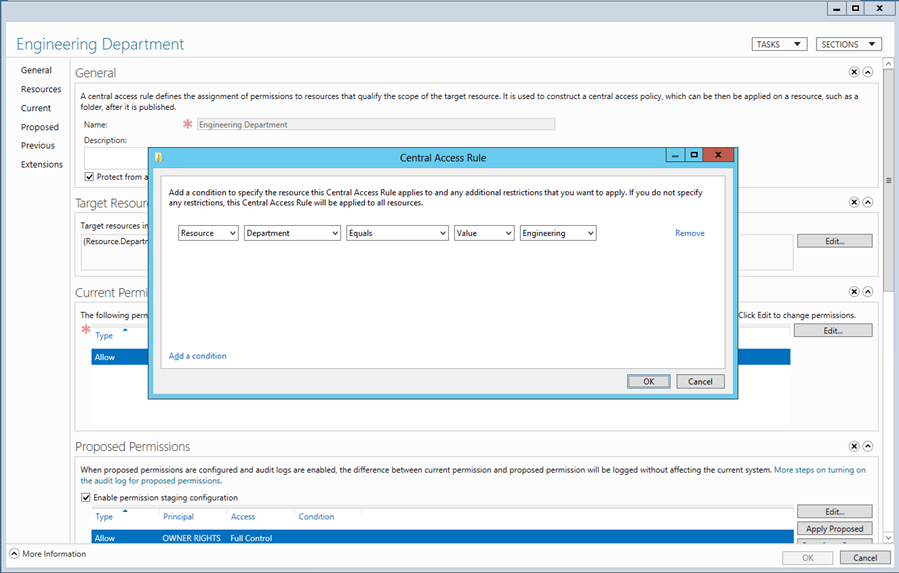
Breaking this down further. Our Target Resources is the Resource Property we are interested in looking over (in this case we want all resources where the Department is Engineering):
And our Current Permissions are going to be based on the Users principal, to ensure that the Users Department Claim is Engineering:
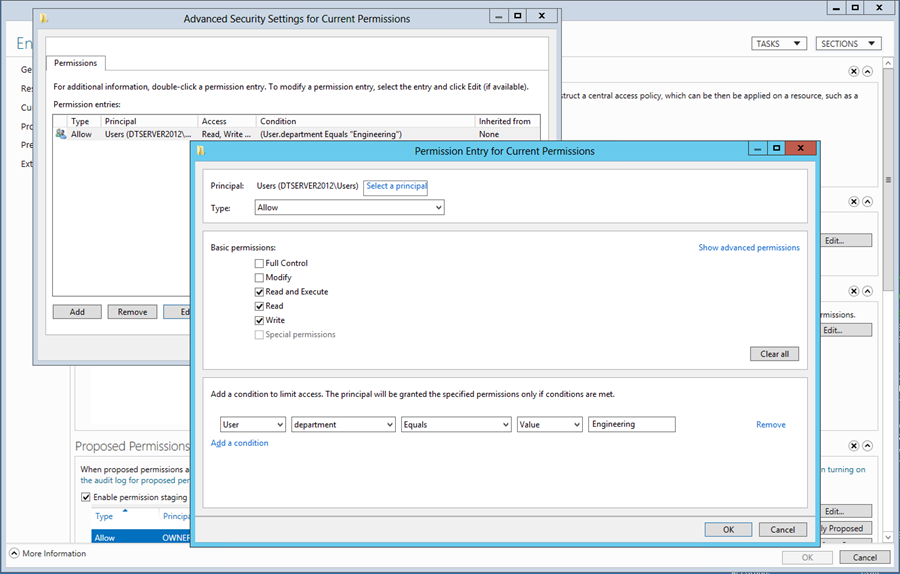
Note that this looks the same as the view we saw in the folder in our first example, making it very powerful and customizable in terms of the rules we want to set up and permissions we want to give.
Further to this, we have a set of Proposed Permissions, so that we can create a new policy and see who it affects via audit logging without the new permissions actually being enforced. And we have the previous set of permissions available in case we need to roll back any new policy after it has been applied:
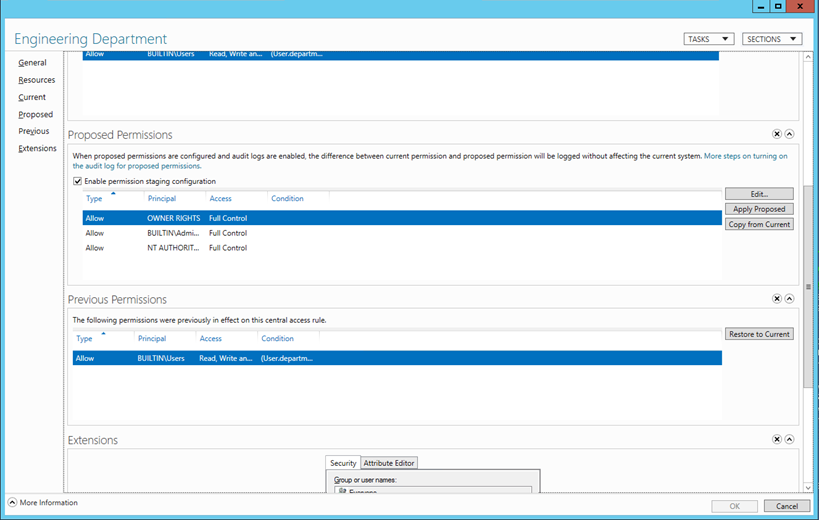
Again configuring these are the same as configuring the Current Permissions.
Automatically Configuring Your Rules
You may have noticed that at the bottom of the Active Directory Administrative Center we have a collapsible section called Windows PowerShell History (shown expanded here):
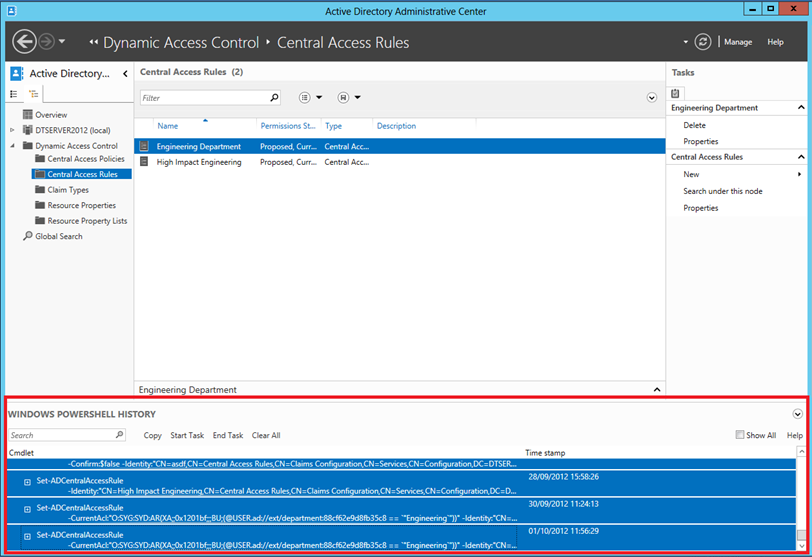
Everything you do in configuring these rules can be performed via PowerShell, and therefore developed and automated. Using the commands you can copy from the Administrative Center as a baseline it makes it much faster than developing these from scratch.
The PowerShell equivalent are documented here: https://technet.microsoft.com/en-us/library/hh846167.aspx
This makes it easy to roll out customized environments automatically and add programmatic logic to the setup of your Claim Types, Resource Properties and Rules.
For further information, Mathias Wollnik (File Server Management Team) has an excellent talk on the features in Dynamic Access Control which is available on Channel 9: https://channel9.msdn.com/Events/TechEd/Europe/2012/SIA207
Posts in this series:
Part 3 - Properties And Claims
Part 4 - Central Access Rules