Exploring Dynamic Access Control Part 3 – Properties and Claims
In the previous post I looked at Classifying resources. In this post I will be looking at setting up custom Properties to use on those resources and claims for users and devices.
Resource Properties
Now we will go a little deeper into the Resource Properties (i.e. the items we can classify resources with).
Inside Active Directory Administrative Center, there is a section for Dynamic Access Control (on the tree navigation to the left), which has Resource Properties under it:
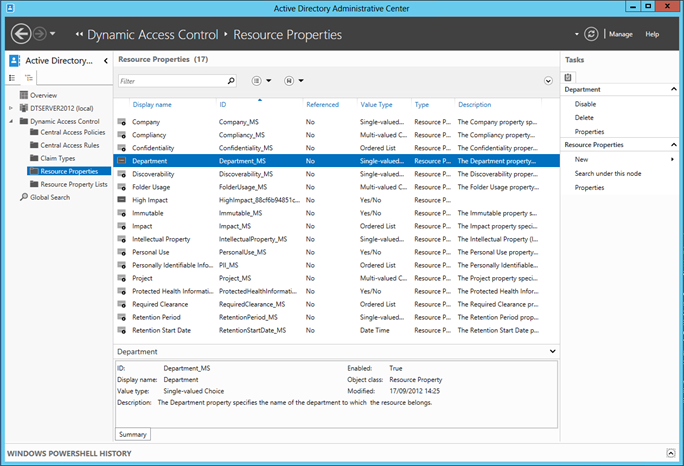
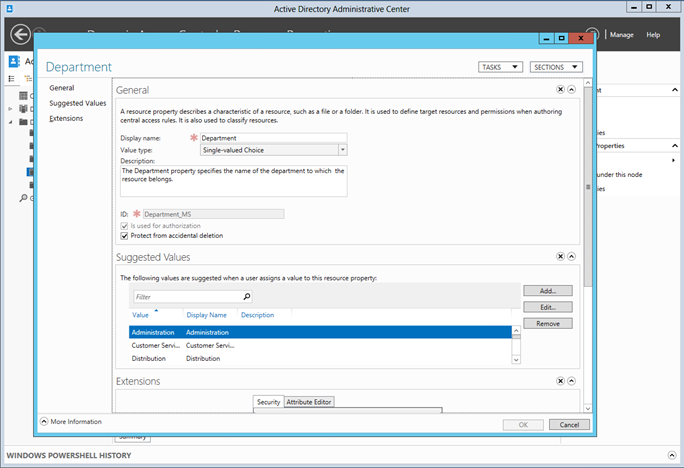
Here are a list of pre-defined resource properties which you get out of the box, and just need enabling, depending on what properties you want to be able to use to classify your resources. This is not an extensive list, and you can easily create, modify or delete new Resource Properties as you see fit.
Claim Types
The other side is setting up the claim types which users and devices have when they log in. There is a section in Active Directory Administrative Center for Claim Types via the navigation on the left:
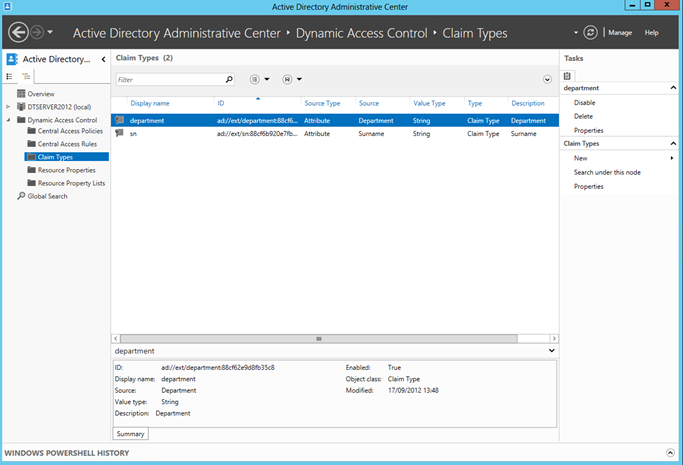
These, unlike the Resource Properties, have to come from an Identity Provider (Active Directory in our case). So these Claim Types have a mapping to an Active Directory property associated with a User or a Device. In the picture above I have configured both the users department and their surname.
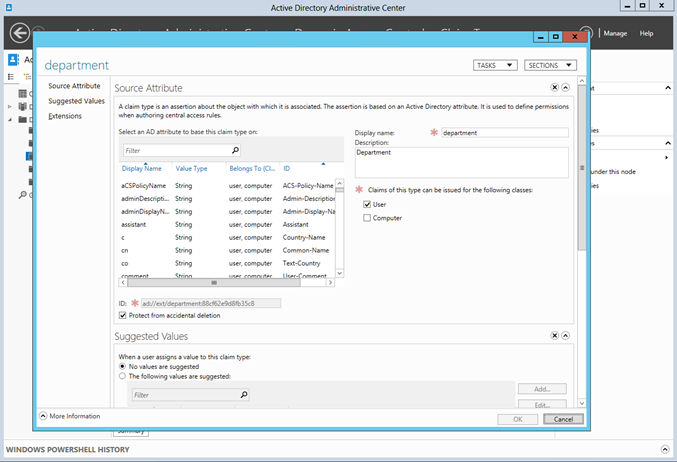
Again these can easily be configured, added and deleted, but must ultimately be provided by Active Directory when the user logs in.
In the final post of this series, we will bring the Resources and Claims we have been looking at here together in Central Access Rules.
Posts in this series:
Part 3 - Properties And Claims