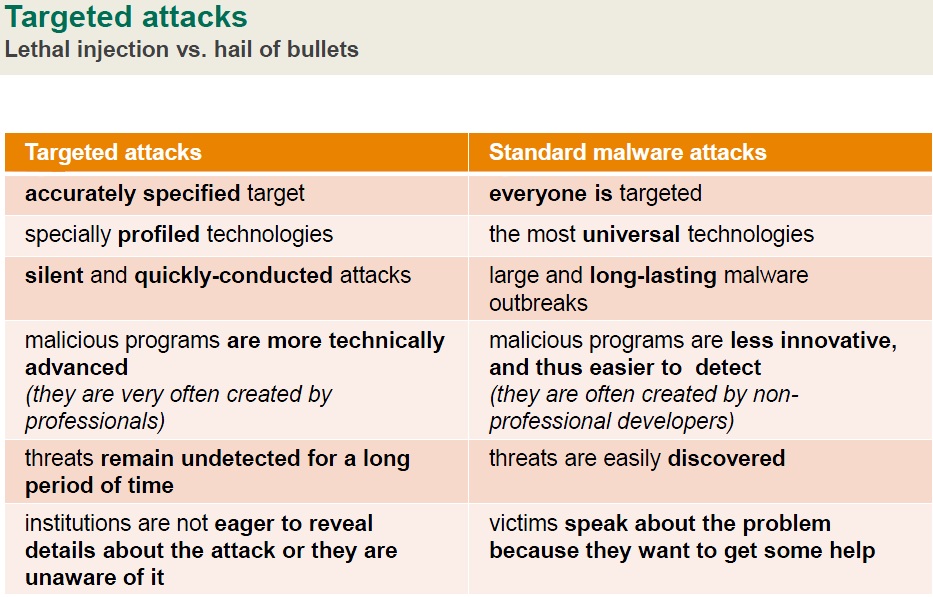
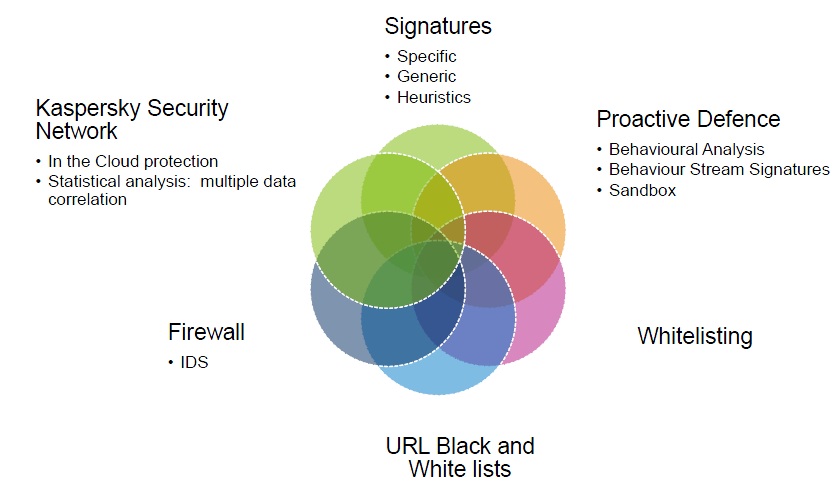
Targetted attacks and Signcryption
How we protect now: signatures +
Signcryption
Signcryption is the primitive that combines public key encryption and digital signature in a single logical step for obtaining less computational and communicational cost.
Data confidentiality and data integrity are two of the most important functions of modern cryptography. Confidentiality can be achieved using encryption algorithms or ciphers, whereas integrity can be provided by the use of authentication techniques. Encryption algorithms fall into one of two broad groups: private key encryption and public key encryption. Likewise, authentication techniques can be categorized by private key authentication algorithms and public key digital signatures.
Signcryption is the primitive that has been proposed by Youliang Zheng in 1997 and combines public key encryption with digital signature in a single logical step, obtaining a less cost for both communication and computation.
Signcryption has the intention that the primitive should satisfy the condition “Cost(Signature & Encryption)<< Cost(Signature) +Cost(Encryption).”
This inequality can be interpreted in a number of ways:
• A signcryption scheme should be more computationally efficient than a native combination of public-key encryption and digital signatures.
• A signcryption scheme should produce a signcryption “ciphertext” which is shorter than a naive combination of a public-key encryption ciphertext and a digital signature.
• A signcryption scheme should provide greater security guarantees and/or greater functionality than a native combination of public-key encryption and digital signatures.
A signcryption scheme typically consists of five algorithms, Setup, KeyGenS, KeyGenR, Signcrypt, Unsigncrypt:
1) Setup - takes as input a security parameter 1^ k and outputs any common parameters param required by the signcryption schemes. This may include the security parameter 1^ k , the description of a group G and a generator g for that group, choices for hash functions or symmetric encryption schemes, etc.
2) Key Generation S(Gen) - generates a pair of keys for the sender
3) KeyGeneration R(Gen) - generates a pair of keys for the receiver
4) Signcryption (SC) - is a probabilistic algorithm
5) Unsigncryption (USC) - is a deterministic algorithm.
A public key encryption scheme consists of three polynomial-time algorithms (EncKeyGen, Encrypt, Decrypt).
EncKeyGen - Key generation is a probabilistic algorithm that takes as input a security parameter 1^ k and outputs a key pair (skenc, pkenc), written (skenc, pkenc)R←EncKeyGen(1^k ). The public encryption key pkenc is widely distributed, while the private decryption key skenc should be kept secret. The public key defines a message m ∈ M and a ciphertext ∈ C.
Encrypt - Encryption is a probabilistic algorithm that takes a message m ∈ M and the public key pkenc as input and outputs a ciphertext C ∈ C, written C ←Encrypt(pkenc,m)
Decrypt - Decryption is a deterministic algorithm that takes a ciphertext C ∈ C and the private key skenc as input and outputs either a message m ∈M or the failure symbol ⊥, written m ← Decrypt(skenc,C).
A signcryption scheme is a combination between a public key encryption algorithm and a digital signature scheme.