Microsoft’s Battle Against Conficker includes Bounty of $250K
Many folks have asked me about Microsoft’s reward program to find the authors of the Conficker/Downadup worm. So, I did a little checking into this and here’s the scoop. Back in the fall (2008), Microsoft was made aware of the Conficker virus and provided a patch for servers in October. (I’ll never understand infrastructure people who don’t keep their servers patched, but that’s a blog post that I won’t do because I won’t have nice words.) InformationWeek reports that almost 2 million machines are impacted a day with this worm, and infected 9 million machines in January. Bottom line: follow the standard security practices: keep your machine current on patches, have a real antivirus package, use strong passwords, etc.
A group of companies are partnering to fight this that includes ICANN, VeriSign, AOL, Symantec, and more. It is true that Microsoft will reward someone $250K for identifying the authors. Individuals with information about the Conficker worm are encouraged to contact their international law enforcement agencies. Additionally, Microsoft has implemented an Antivirus Reward Hotline, +1-425-706-1111, and an Antivirus Reward Mailbox, avreward@microsoft.com , where tips can be shared.
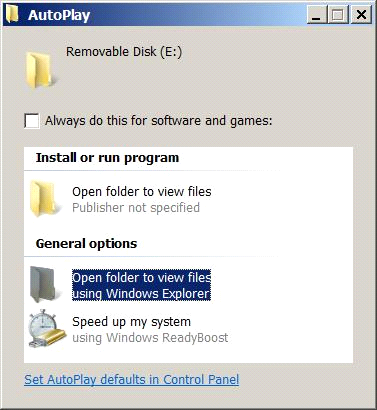
This worm does a variety of hacks to a computer. It looks to infect local computers through a couple of means. It also can copy itself to “removable media” like USB drives. In this effort, it will add an option to the AutoPlay dialog (see below, not the top Open option), which fools a user into starting the virus – just perfect when someone with the infected machine gives you a file from the USB drive. This one is bad because it would execute as the user, and include the full worm payload on the device, plus the bad option is at the top in place of the normal position.
[From the MMPC] Conficker also makes several configuration changes so that it runs every time Windows starts. Specifically it adds itself as a service and also adds a registry value under HKCU\Software\Microsoft\Windows\CurrentVersion\Run. It also terminates various services which should be re-enabled and more information is available here . Similarly, Worm:Win32/Conficker.B attempts to terminate any process which has a name which seems to indicate that it is an antivirus program or other security software. It also blocks access to the web sites of many antivirus and security vendors and to Windows Update. This worm takes some additional steps and our encyclopedia entry includes more details.
TURN ON WINDOWS UPDATE ALL THE TIME, and HAVE A ANTIVIRUS PROGRAM.
MSRT Released Today Addressing Conficket and Banload (JAN. 13 blog post from MMPC)
Centralized Information About The Conficker Worm (JAN. 22 blog post from MMPC)
Protecting your Windows machine from Conficker
Protect yourself from the Conficker computer worm (for consumers)