Storage card wipe and encryption - What's the deal?
In Windows Mobile 6 we added the ability to encrypt the storage card of a Windows Mobile device as well as wipe it remotely.
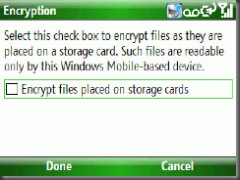
The encryption can either be enabled by the user or enforced through an Exchange 2007 policy.
The encryption of the storage card uses AES 128.
So let me explain more...
Storage Card Encryption
Firstly the encryption does tie the Storage card to the device. The encryption is tied to a unique ID created upon Hard Reset of the device. You cannot move the encrypted card to another device without first decrypting the card.
When the card is encrypted a key is placed on the device itself and the data on the card is encrypted.
This is important as many existing solutions (particularly on other platforms) store the key and data in the same place... so if you have the device you have everything you need to decrypt the data (all you need is time :) )
Storage Card Remote Wipe
Now if you do initiate a remote wipe what happens is that the card is erased and the key removed from the device.
This gets over two major concerns/hurdles.
1) What if someone pulls the storage card quickly from the device stopping it being erased. Well it doesn't matter as the key is removed.
2) What happens if the storage card has the HW write lock disable enabled.. well again the key from the device is removed so the data is useless.
How many times do you overwrite the data on the Storage card?
One question I sometimes get from security teams is how many times we overwrite the data. This is mainly a confusion from PC Hard Drive encryption. There is no need for multiple writes of data on flash drives. The need for multiple writes on hard disks is due to the fact that traditional hard disk heads can skip, and thus jump over sectors, and not wipe them...so multiple overwrites can ensure each sector is hit.
Why don't you encrypt the device?
The #1 followup question I always get is why we don't encrypt the data on the device itself...
Well once the mobile device is accessed via the device-lock or power-on password, all the data on the device is accessible to the user whether it is encrypted at rest or not.
The weakest link is the SD card external memory which, if not encrypted, can be accessed by any device or computer that can read SD cards.
By encrypting the SD card, the weak link is made strong and the data on that card can only be accessed by the paired device after the device-lock PIN or password has been correctly entered.