Apache Stonehenge new M2 release adds claims-based authentication scenarios
Web Services protocols have been around for ten years now. The specifications around these protocols have moved through major standards bodies and most vendors and open source projects have implementations of these web services protocols in their products. That being said, connecting heterogeneous platforms in an interoperable manner hasn’t always been easy. That’s why Microsoft and other vendors initiated the Apache Stonehenge incubator project, a little more than a year ago, “to develop a set of sample applications to demonstrate seamless interoperability across multiple underlying platform technologies by using currently defined W3C and OASIS standard protocols. By having a set of sample applications, with multiple language and framework implementations will become a useful and important part of the SOA landscape” (quote from the Why Apache Stonehenge? page).
Our goal was to show that you can run an application across different platforms using different technologies purely on the foundation of the Web Services protocols and standards.
Launched in January 2009, Stonehenge is designed to provide a public forum to test the interoperability of WS-* protocols on different technical stacks and to build open source sample applications that could provide best practices and coding guidelines for better interoperability.
It is helpful for customers and the industry to have multiple implementations of these standards and have the ability to choose the best ones for their scenarios and requirements. Customers get working code on multiple platforms and vendors catch bugs and test interoperability issues in an open manner.
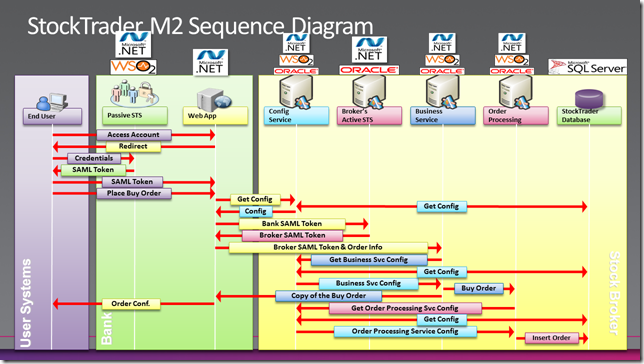
The first version “M1” of the Stock Trader sample application showcased the main Web Services standards, including WS-Security.
Today, we are glad to announce the availability of Stonehenge “M2”, the second iteration, now including WS-Trust 1.4 and WS-FED 1.1 protocols for claims-based authentication scenarios.
This allows the end-users’ to be authenticated through an independent Security Token Service (STS) that is trusted by the bank and to pass that token to the broker to process the transaction.
Watch the video with Kent Brown (Product Manager, Microsoft) and I where we introduce Stonehenge and Kent presents an actual demo.
People can download the M1 and M2 releases of Apache Stonehenge from http://www.apache.org/dist/incubator/stonehenge and the documentation is up on the wiki: https://cwiki.apache.org/confluence/display/STONEHENGE/Index
We are looking forward to working with the community to shape out the next steps. As always, if you have feedback, questions, or wishes, please join us on the Stonehenge project site!
Kamaljit Bath, Principal Program Manager
Additional links:
- Blog: Stonehenge: showcasing Web Services interoperability
- Blog: Apache Stonehenge, interoperability at work
- Sun Joins Microsoft on JavaOne Stage in support of Apache Stonehenge Incubator Project
- Blog: Apache Stonehenge Interoperability Presentation at the NYC .NET Dev User Group
- Blog: Apache Stonehenge demoed at PDC09