Windows Server as a Workstation
Back in the Windows 2003 timeframe, Microsoft had a problem. The security press of the time liked to put out charts showing which operating systems had the most vulnerabilities. Windows 2000 wasn’t looking so hot, owing to the fact that Windows 2000 Server had a full web browser built-in, “out of the box.” Even if a server administrator followed best-practices and never booted the browser, Windows still looked bad in the charts because all browsers, including IE5 and IE6, had an endless stream of security patches.
Windows cobbled together a small task force to address this problem by introducing the Enhanced Security Configuration feature for Internet Explorer when run on Windows Server.
ESC: Enhanced Security Configuration
ESC makes myriad small changes across the browser, but the primary change is that it kicks the security level of the Internet Zone up to High:
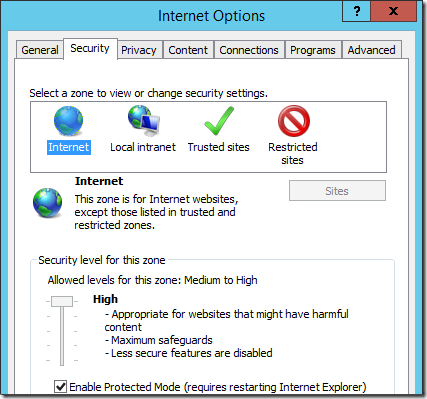
By setting the Internet Zone to use the High Template, ActiveX and script execution are blocked and a huge number of features are disabled by default. This simple change alone would have been sufficient to make the charts look dramatically better (because virtually all browser exploits require one or more of the disabled features).
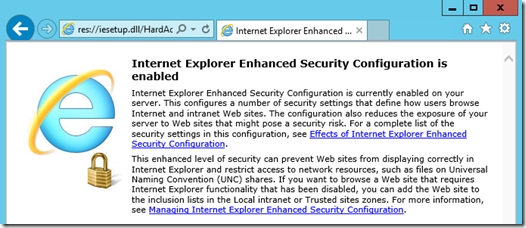
To help the user understand that this configuration is enabled, the default homepage is changed to a very wordy explanation:
This could be summarized as: “This is a server. Don’t browse from your server. That’s what workstations are for!”
However, the notifications don’t stop there. As you browse around, you’ll see many ancient notifications that were long ago hidden by the default security level template, like this prompt from the 1990s that attempted to explain what HTTPS was all about:
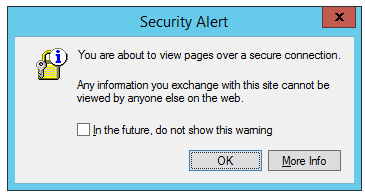
Any time you visit a website that wants to run script or perform another action that is not permitted due to the changes made by ESC, a prompt is shown:
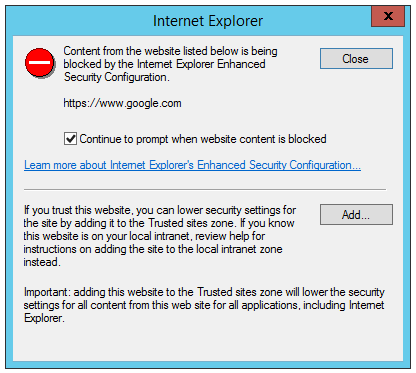
What this prompt really means is: “Hey, we noticed that you’re browsing from your server. We really don’t want you to do that, but we’ll let you. If you’re really really committed to browsing securely from your server, you can load the page in this mode which will probably break it. Or you can manually add this site to the list of sites you trust to run with regular permissions.”
Some … hyper-vigilant …users find these prompts useful and don’t seem to mind them. Some administrators feel they have a genuine need to use a browser on the server itself and they don’t feel they can accomplish their goals by browsing from a workstation.
However, if you’re simply a developer who’s running a Windows Server as a workstation (e.g. your dev box) so you have a full IIS / SQL instance, etc, and you’re not really using it as a production server, it is likely that these prompts will quickly get intensely irritating.
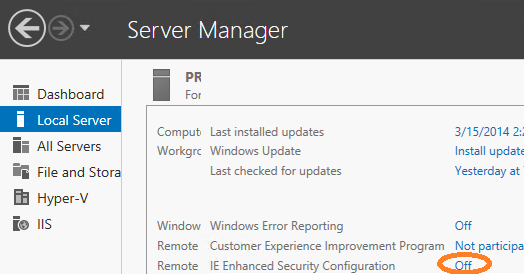
Fortunately, you can very easily instruct the Server to knock it off. From the Local Server tab of the Server Manager, click the link next to the IE Enhanced Security Configuration item:
A dialog will launch that allows you to control the ESC feature:
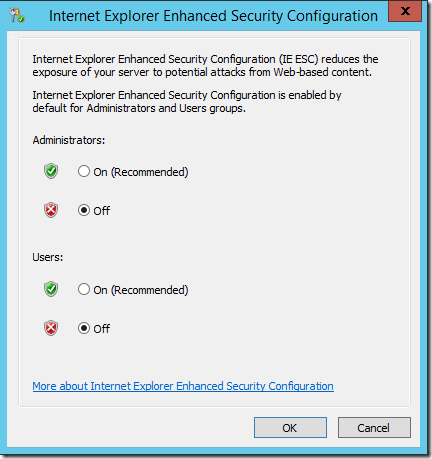
Changes take effect the next time Internet Explorer starts.
Note that clicking the “More about Internet Explorer Enhanced Security Configuration” link will launch a browser which prompts you with the ESC “Content Blocked” dialog for 9 different domains (including Facebook and about:blank) before rendering the generic Internet Explorer Help page.
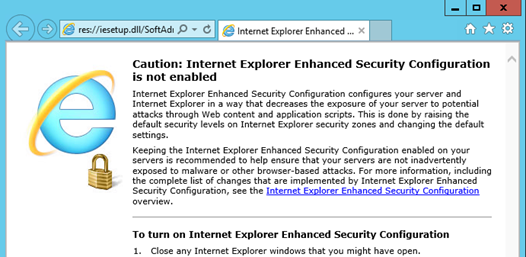
After you disable ESC, the browser’s default homepage will change to a warning to remind you that you’ve done so:
The ESC feature has received only minimal attention from the IE development team over the last decade. By default, the recommended “Windows Server Core” configuration doesn’t include a GUI at all, which means that servers that are acting as proper “servers” are in a very secure configuration automatically. Even when you enable the GUI for Server, Windows supports uninstalling the Internet Explorer browser if it isn’t needed.
In my opinion, the ESC feature should probably be yanked out—it’s irritating, unnecessary, and has an ongoing maintenance cost for the IE development team.
For now, however, disabling ESC isn’t the only change you need to make to make your server behave like a workstation.
HTML5 Video
If you’re using a PC running Windows Server 2012 R2, you might find that HTML5 video doesn’t play in Internet Explorer. For instance, when visiting a page like the FishBowl benchmark, it might stop loading at the “Initializing” stage, with the F12 Developer Tools’ Console tab showing an inscrutable error:
SCRIPT65535: Unexpected call to method or property access.
The problem is that, by default, Windows Server does not include the HTML5 video codecs, and thus they’re not available to Internet Explorer. To resolve this, simply boot a Windows PowerShell command prompt (e.g. by clicking the icon in the task bar):
and then enter the following two commands:
Import-Module ServerManager
Install-WindowsFeature Desktop-Experience
A reboot is required for the installation to complete.
-Eric Lawrence
MVP - Internet Explorer