Azure Active Directory B2C and Azure Functions
Hello everyone,
In the light of my recent post about B2C and ASP.NET Core web APIs, I thought I'd shed some light on how to make Azure Functions work with B2C, because it may not be immediately obvious from the portal's interface. Actually, all the information is already in this article, and it still applies: https://blogs.msdn.microsoft.com/appserviceteam/2016/06/22/app-service-auth-and-azure-ad-b2c/
Setting up B2C authentication for your Azure Functions App is actually really easy:
Create your Azure Functions App and write down the URL
- E.g. https://myazurefunctions.azurewebsites.net (make sure to make it a HTTPS URL)
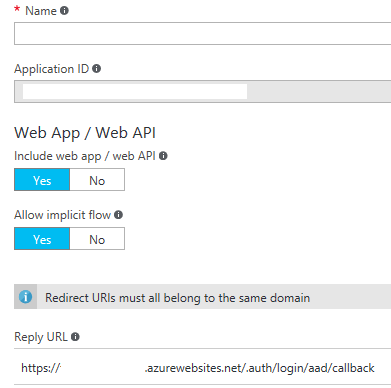
Configure your application in Azure Active Directory B2C:
- Write down the Application ID
- Add a reply URL for your Functions App, adding the suffix /.auth/login/aad/callback. E.g. https://myazurefunctions.azurewebsites.net/.auth/login/aad/callback
The configuration should look something like this:
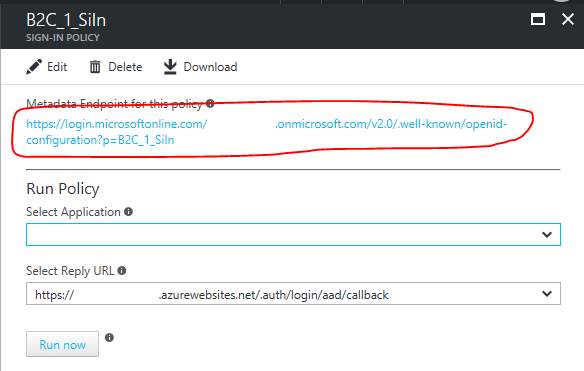
Get the Metadata Endpoint URL for your Sign-in policy
If you open the details of your sign-in policy, you'll find it right at the top. E.g.:
In your Functions App, on the bottom left select "Function app settings" and go to "Configure authentication":
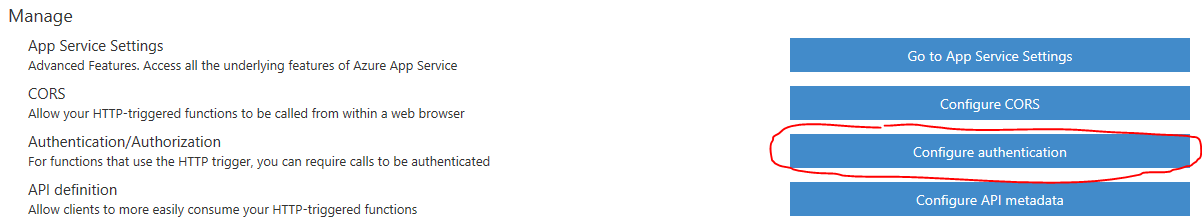
Turn on authentication and select Azure Active Directory:
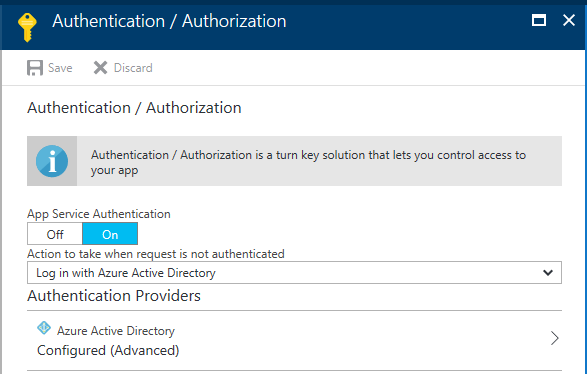
Select the advanced settings and enter the following values:
- Client ID: The Application ID which you copied in step 2. a.
- Issuer Url: The Metadata Endpoint URL from step 3.
Save your settings and you're done!
Once the changes have taken effect, if you try to test your Azure Function without an Authorization header, you'll get the following error – as expected:
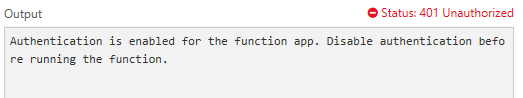
However, with a valid bearer token, you're up and running again:
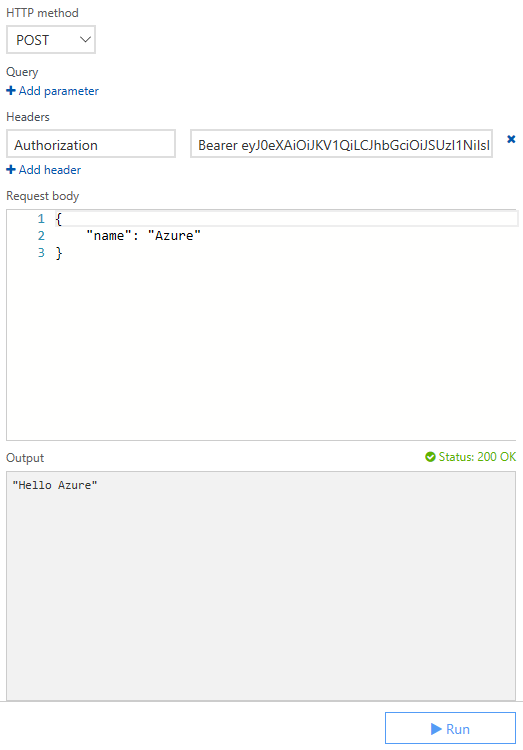
I hope this made your life a little bit easier.
Cheers,
Helge Mahrt