First Line of Defense for Web Applications – Part 1
Hi folks, I am Anmol Malhotra and I work with ACE Services Team as a security consultant.
There are lots of security principles which one should be aware of while developing software but at the heart of any secure application, there should be a first line of defense – and the mother of all defenses is: Input Validation!
There is so much buzz around for how hackers hack and what offensive techniques do they use to break in, but at the core it is the mitigation strategy which matters to me and many of my customers. Lack of input validation is one of the _core_ vulnerabilities for almost all web attacks. If we can get this thing right, we can save lot of $(s) down the road. This series of blogs will talk in detail about Input validation strategies for web applications. We will also take a look at some interesting top Validation bloopers.
Let’s start with some basics today on Input validation.
Why Bother?
Would you let a stranger in your home? Probably not, unless he’s been thoroughly vetted and screened. But developers often let strange users inject data into their application without any sort of checking.
Sometimes developers assume no strangers will try to enter their house –they think that only their client software will communicate with their server software. This problem is not limited to thin web applications; in fact, it becomes even more severe in thick client designs. Wherever you give the user the ability to provide some input for processing, you also give him the ability to inject malicious data. Input validation is an application’s screening and vetting process that attempts to block as much malicious data as possible. For example, the application may limit input by length, type, or character. Without proper validation, malicious input will be processed by the application and can result in any number of security breaches.
Web applications designed today are heavily data driven and they exist because of a specific business need. Much of this data is provided by the users of the web application. Failure to validate this data in the application is asking for trouble. Consider an example of SQL injection attack, one of the key vulnerability required to achieve a successful SQL injection exploit is poor or no validation controls in the application.
Name any known web application attack and you will find that one of the core vulnerability is lack of input validation in the application itself. For example:
· Buffer overrun conditions
· Cross site scripting
· SQL injection
· XML injection
· LDAP injection
· Canonicalization issues
· Integer Overflow/Underflow
· Response Splitting
· Data Tampering
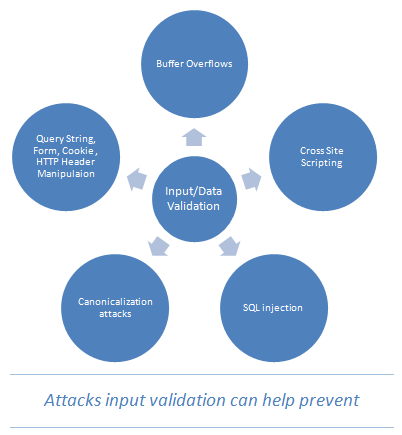
The list goes on and on. As it is clearly depicted from the list above many web application attacks exploit lack of input validation in the application. From an attackers prospective, this opens a huge door of opportunity to inject malicious data with the intent to make the application react in a way which is it is not supposed to be doing at all.
Cheers (stay tuned, more to come)
- Anmol Malhotra - https://blogs.msdn.com/anmolm