Claims based Identity & Access Control Guide – Early drafts available
We finally have a CodePlex site for sharing early content with you all. Check the downloads section for:
- A few intro chapters (some of the “theory”, technologies and protocols behind claims based identity)
- The first scenario (roughly described in my post here, but better and nicer, and written in English :-))
- The sample code for this first chapter
The first scenario is fairly basic. However, I think people with little previous experience with Claims will find this really useful. Those who are very experienced, will probably not find a lot of new content at this point.
Few things to highlight:
On the code:
We wanted to keep it very very simple. Right now the only pre-requisites are: IIS and Windows Identity Foundation (WIF). IIS is needed because some pieces of the samples require HTTPS. WIF is needed because, well…this is about claims right? All the rest is mocked or simulated.
We tried to minimize the amount of setup required, but there are a few steps that are needed (e.g. installing a certificate, enabling HTTPS). There’s a small script that explains what to do. But we added quite some checking and verification here and there to highlight if something is likely to fail due to a problem in the configuration.
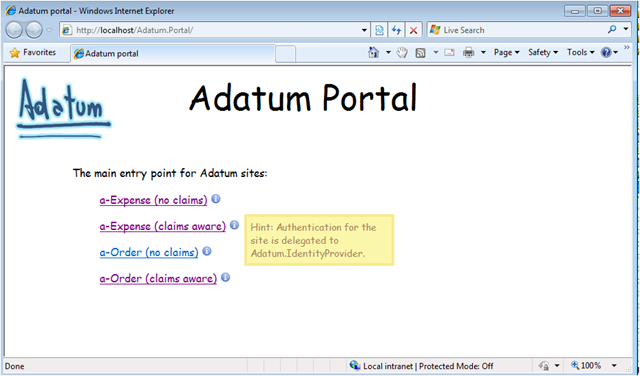
The IIS web sites are created the first time you open the solution in Visual Studio. Running the samples you should see:
Wherever you see the little blue “i” icon, there will be a tip with further explanations.
Many things in the samples are simulated. For example, a-Order in the chapter is described as a Windows Authentication enabled app. We don’t want to mess-up with your AD or with your machine accounts & groups. Also, when we claims-enable an app we don’t want to require you to necessarily deploy ADFS. Therefore we included in the solution a “fake” Issuer to create the required claims. The Guide explains the differences between the real scenario and the simulation though; and steps to configure a real scenario.
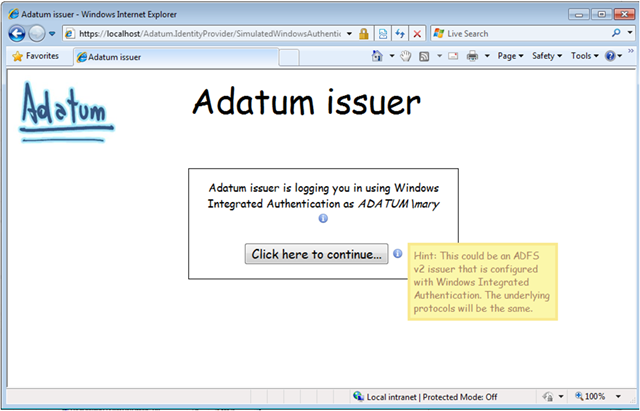
Following a-Expense (Claims Aware), for example leads you to:
Notice the extra explanation. Generally, you will not see anything automagically happening. The intent is that everything not obvious will have a tips like this or an in-line comment.
On the chapters:
The first three chapters are introductory and you will see a lot of TBDs and comments. All of this is, of course, work in progress; but we’d love your input.
The introduction chapters are mostly “theory”: background, context, terminology, etc. The fourth chapter is the first scenario: WebSSO. You will see callouts here and there from one of our four main characters in the book:
- Bharath, the Security Expert
- Jana, the Architect
- Poe, the Operations guy
- Markus, the Developer
The intent is to highlight specific points of views from each of these guys and enrich the guidance we want to provide.
Important note: these chapters are NOT formatted to the final layout. So, for example, the callouts will be on the margins in the final book. Please concentrate on the content and not on the format for now.
Hope you like it! Let us know what you think!