Using Fiddler to acquire a JWT ( JSON Web Token ) for use with the Graph API
One of the things that our developer support team has been trying to figure out over the past few weeks is just how we can play with the new Windows Azure Active Directory Graph API without the overhead of visual studio or a console application. We were already using Fiddler as a HTTP traffic sniffer and were able to take an existing successful Graph request, modify it in the Composer feature of fiddler, and test different Graph APIs. The drawback was that we needed an initial set of requests to work from. This lead us to investigate just how we could request a JSON Web Token ( JWT ) from the Windows Azure Access Control service.
There have been several blog posts discussing different ways to generate the packet. What we think we have found is a very straight forward method for obtaining the authentication token from the ACS service using just the Fiddler Composer feature.
To complete this exercise, you will need the following:
- Download the freeware Fiddler HTTP traffic capture tool from <www.fiddlertool.com>
- A Service Principal application ID or client ID for your tenant
- The Service Principal secret or password
- A valid tenant domain name that the Service Principal described in 2/3 can be used to read/write data using the graph.
Once you have all 4 items, you can follow these simple steps and retrieve a JWT from the ACS service.
You will need a valid tenant that has a valid service principal associated with it that has permissions to read data from the tenant’s AAD instance.
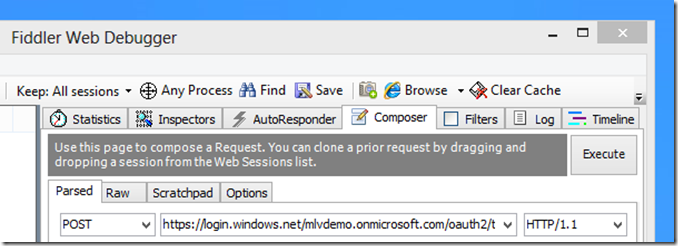
1. Start Fiddler
2. Click Composer Tab.
3. Click the “Parsed” tab.
4. Select “Post” from the command drop down.
5. In the URI edit control next to the “Post” command dropdown, type:
https://login.windows.net/[your_tenant_name]/oauth2/token?api-version=1.0
Replacing [your_tenant_name] with a valid tenant, like mlvdemo.onmicrosoft.com. The display will look similar to the following:
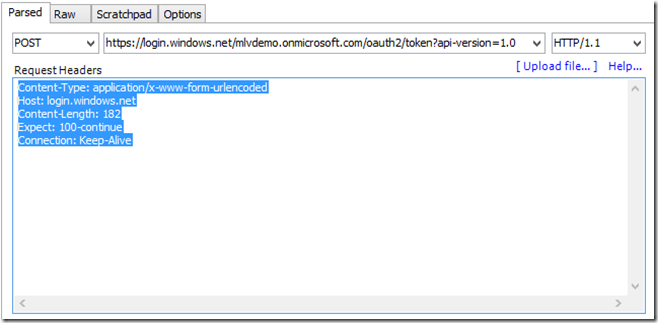
6. In the “Request Headers” cut and paste the following:
Content-Type: application/x-www-form-urlencoded
Host: login.windows.net
Content-Length: 178
Expect: 100-continue
Connection: Keep-Alive
The display will look similar to the following:
7. In the request body add the following:
grant_type=client_credentials&resource=https%3a%2f%2fgraph.windows.net&client_id=[Client_ID]&client_secret=[Service principal secret]
Replacing [Client_ID] with a valid GUID for a client ID similar to:
7a8fd334-fc76-4585-b77a-1b7bc7dd1376
Replacing [Service principal secret] with the secret for the service principal replacing reserve characters with their corresponding hexadecimal encoded value. A nifty tool for doing the same can be found here. For example:
glYO5dRztXLYyA+S7nxYclOzDBlmfh/F4KacfkIXgH8=
Would be:
glYO5dRztXLYyA%2BS7nxYclOzDBlmfh%2FF4KacfkIXgH8%3D
Replacing the +, / and = with the appropriate hexadecimal values. The full string for the above provided client ID and Secret would be:
grant_type=client_credentials&resource=https%3a%2f%2fgraph.windows.net&client_id=7a8fd334-fc76-4585-b77a-1b7bc7dd1376&client_secret=glYO5dRztXLYyA%2BS7nxYclOzDBlmfh%2FF4KacfkIXgH8%3D
8. Click the “Execute” button. If you have supplied a valid tenant along with the valid service principal client ID and secret, you should get back a valid JWT bearer token for accessing the AAD using the Graph API.
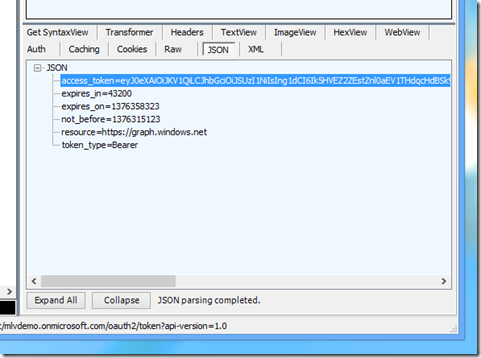
The value returned in the access_token property needs to be added as the “Authorization” property in the header of all REST requests made to the AAD for this service principal.
If you select the “Raw” tab in the lower window of Fiddler where the response data for a request is displayed, you will see something similar to the following: ( NOTE: the access_token return values has been truncated to reduce clutter)
HTTP/1.1 200 OK
Cache-Control: no-cache, no-store
Pragma: no-cache
Content-Length: 1103
Content-Type: application/json; charset=utf-8
Expires: -1
Server: Microsoft-IIS/7.5
Request-id: 8d44e415-caa7-4a67-90f6-1f20a679285b
X-Content-Type-Options: nosniff
X-Powered-By: ARR/2.5
X-Powered-By: ASP.NET
Date: Thu, 08 Aug 2013 17:42:18 GMT
{"token_type":"Bearer","access_token":"eyJ…--w","expires_in":"43200","not_before":"1375983748","expires_on":"1376026948","resource":"https://graph.windows.net"}
The JWT is returned in the access_token property of the response:
Once we have the authentication token, it is very easy to create REST API calls against the AAD. I will continue to explore some of these API calls over the next few blog posts.