[Windbg Script] Get Portable Executable Headers
There are several tools you can use to read the image headers, like Dumpbin.exe and Link.exe, for instance. You can, however, also use Windbg for doing that! In other words, during your debugging session you can see the header from an image file without executing any other tool except this script.
This is a very simple script that lists all loaded modules and gives you two options:
- Visualize a summarized view of the header for a specific image.
- Visualize a detailed view of the header for a specific image.
Actually, there is one more option: run the script and provide the module as an argument. J
Hot trick! I just learned how to use arguments when running scripts! It’s very cool! (and undocumented L) I hope the next Windbg version includes it, anyway, you can learn it from this script that I just changed to accept parameters.
Basically you need to run the script as:
$$>a<scriptname.txt arg1 arg2 arg3 … ß Notice the >a<
Then you get the arguments from the script source code using alias, like:
${$arg1} ß Alias, not pseudo registers.
It starts in $arg1 until $arg<n>.
In my script I came up with a test to check if the script was called using arguments or not. You may want to reuse this idea.
If you get a syntax error, just run it once more and it should run. This is a problem related to alias. I already mentioned something about it here.
These are some screenshots:

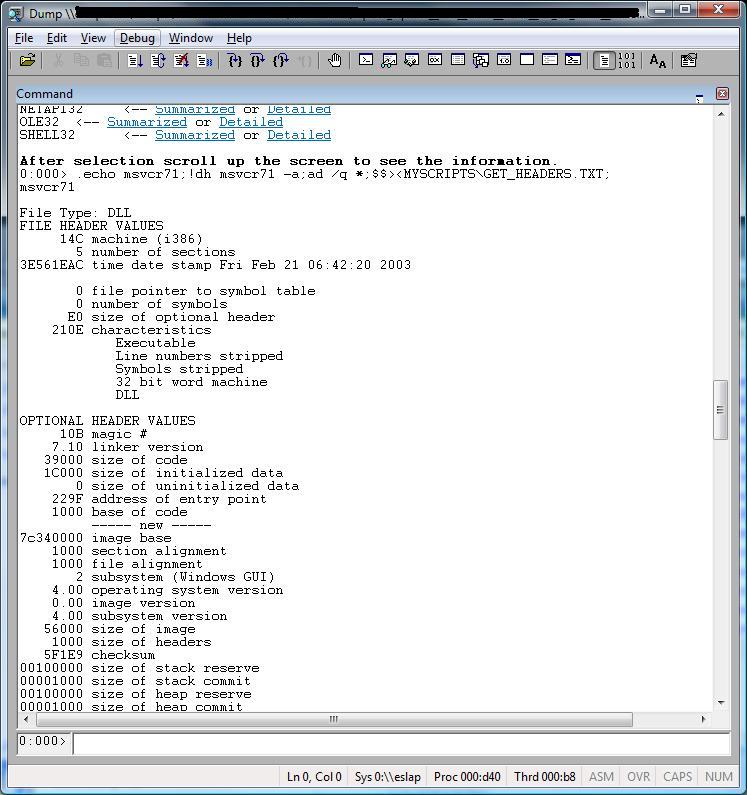
Now using a module name when calling the script:
Source code for GET_HEADERS.TXT:
$$
$$ =============================================================================
$$ Get headers from images.
$$
$$ Compatibility: Win32.
$$
$$ Usage: $$>< to run the program without arguments.
$$ $$>a<scriptfile dllname to run the program using arguments.
$$
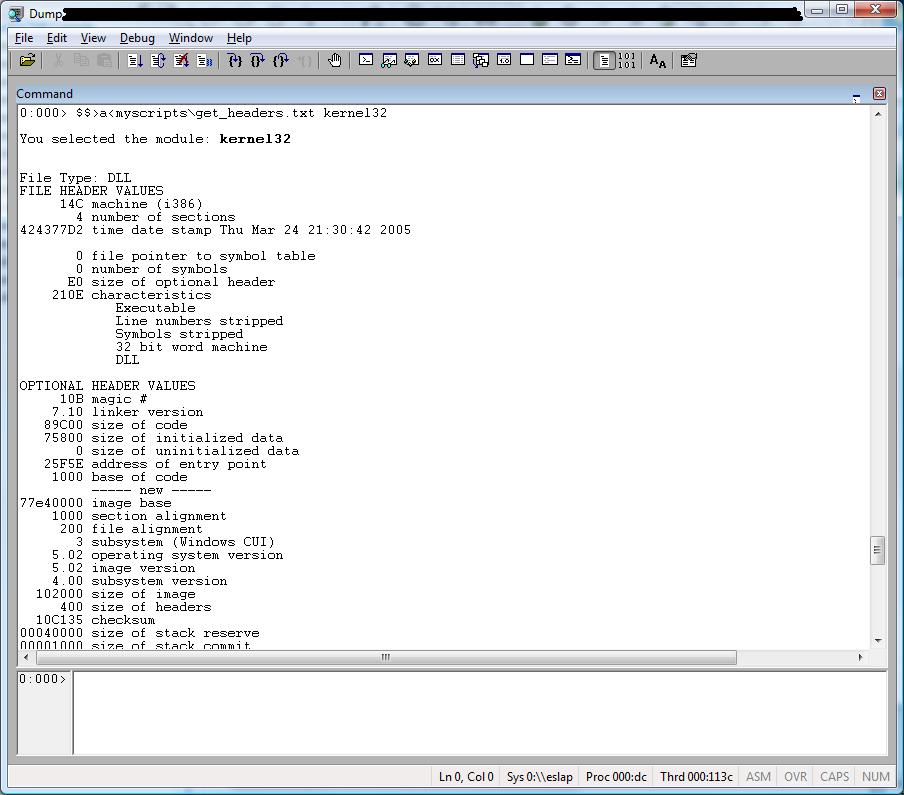
$$ Example: $$>a<myscripts\get_headers.txt kernel32
$$
$$ If necessary change the filename below to include your path and filename.
$$ Default file name and path should be changed below if necessary.
$$
$$ Roberto Alexis Farah
$$ Blog: https://blogs.msdn.com/debuggingtoolbox/
$$
$$ All my scripts are provided "AS IS" with no warranties, and confer no rights.
$$ =============================================================================
$$
.block
{
as ${/v:ScriptName} MYSCRIPTS\\GET_HEADERS.TXT
}
r @$t0 = 0
.if(${/d:$arg1})
{
.printf /D "\nYou selected the module: <b>${$arg1}</b>\n\n"
!dh ${$arg1} -a
}
.else
{
.printf /D "\n\n<b>Select option below for loaded modules:</b>\n\n"
.foreach(obj {lm1mo})
{
.block
{
.printf "${obj}\t <-- "
.printf /D "<link cmd=\".echo ${obj};!lmi ${obj};ad ${/v:ScriptName};$$><${ScriptName}\">Summarized</link> or "
.printf /D "<link cmd=\".echo ${obj};!dh ${obj} -a;ad ${/v:ScriptName} *;$$><${ScriptName}\">Detailed</link>\n"
}
}
.printf /D "<b>\nAfter selection scroll up the screen to see the information.</b>\n"
}