Ask Learn
Preview
Ask Learn is an AI assistant that can answer questions, clarify concepts, and define terms using trusted Microsoft documentation.
Please sign in to use Ask Learn.
Sign inThis browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
The following Example is an illustration of how the PowerShell Workflow Activity could be used, some may argue that the PowerShell MA would be better suited for this type of activity and in a scenario where Bulk creations would be necessary i would agree, but this blog posting is to demonstrate that how to use the PowerShell Workflow Activity which is part of the Workflow Activity Library.
The below example is a modified version of the previously documented Post which was Documented using a Server 2008 Target Domain Controller . The below example can be used with Server 2012 R2 or earlier.
Additionally its important to note that this workflow should be triggered after the Synchronization Service updates the users resourceSid (objectSid) in the FIM Portal, this would be a good indication that the user object has been created in AD.
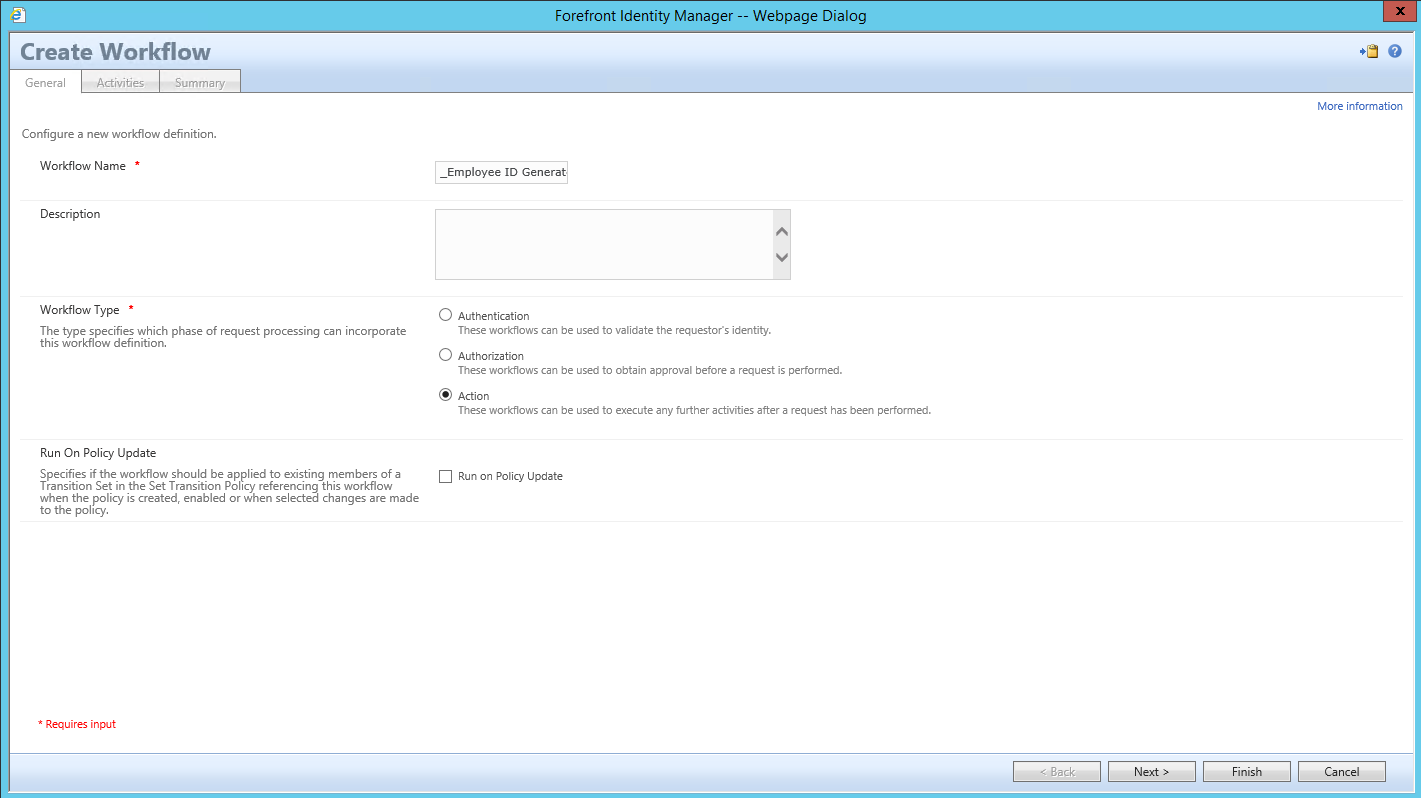
Configure the 1st Workflow Activity
Param($SamName,$HomePath,$DriveLet,$Domian)
## Create Remote Session (verify that the FIM Service account has permission to run Remote Powershell on the target DC)
$Server = "DC1"
$dc1 = New-PSSession -ComputerName $Server
# Any errors during execution of the script or the script block are bubbled up automatically.
# Comment out -ComputerName parameter when running interactively
## Uncomment for Manual Testing
# $SamName = "orangejuice"
# $homepath = "\\Svr2\e"
# $DriveLet= "H"
# $Domain = "Contoso"
##Set Variables
$Spacer= " "
$HomeDir = $homepath + "\" + $SamName
###
#Create Home Directory
mkdir $homedir
#Assign Access Rights
$account=$Domain+"\"+$SamName
$rights=[System.Security.AccessControl.FileSystemRights]::FullControl
$inheritance=[System.Security.AccessControl.InheritanceFlags]"ContainerInherit,ObjectInherit"
$propagation=[System.Security.AccessControl.PropagationFlags]::None
$allowdeny=[System.Security.AccessControl.AccessControlType]::Allow
$dirACE=New-Object System.Security.AccessControl.FileSystemAccessRule ($account,$rights,$inheritance,$propagation,$allowdeny)
$dirACL=Get-Acl $homedir
$dirACL.AddAccessRule($dirACE)
Set-Acl $homedir $dirACL
#Assign AD Attributes
#Enter-PSSession $dc1
Invoke-Command -ComputerName $Server -Script {param($SamName, $HomeDir, $DriveLet) Set-ADUser -Identity $SamName -Replace @{homeDirectory=$homedir;homeDrive=$DriveLet} -Confirm:$false} -Args $SamName, $HomeDir, $DriveLet
Click on Save
Ask Learn is an AI assistant that can answer questions, clarify concepts, and define terms using trusted Microsoft documentation.
Please sign in to use Ask Learn.
Sign in