Microsoft Azure Cloud Services scheduled maintenance - Disable SSL V3.0 - Start on 19th Jan 2015 : How will I know if I am affected? How can I prevent it ? How should I plan for updates?
Everything in here is for PaaS Cloud Service and may not necessarily apply to IaaS VMs.
The January security update, scheduled to begin on January 19, 2015, will disable SSL 3.0 by default for Azure Cloud Services customers who have Automatic Updates enabled. Most of you would have received the following via email
https://click.email.microsoftemail.com/?qs=f170955b29fc90637ea3eb24dbcfda780fc1cdce07e15d07127f4df34ef0dbedf6a798b7acb3a382
First Question – Can I prevent it?
Can I prevent the update? Yes
Is it good to prevent the update? No
The Guest OS is updated at periodic intervals and has two setting Automatic and Manual. If you choose manual then the Guest OS will not be updated.
Existing Cloud Service - Full details on how to do it from the Portal can be found here https://msdn.microsoft.com/en-us/library/azure/ff729420.aspx
New Cloud Service Deployed after 19th Jan 2015 – By default the new Cloud Service will go against the latest updated OS. You can explicitly set it to get deployed to a previous OS version as below.
There is an entry in the config file
<ServiceConfiguration serviceName="<service-name>" osFamily="<osfamily-number>" osVersion="<os-version>" schemaVersion="<schema-version>">
By default it’s * if you look into a new project. You can select the specific OS family that you want as below.
<ServiceConfiguration serviceName="TargetCloudService" xmlns="https://schemas.microsoft.com/ServiceHosting/2008/10/ServiceConfiguration" osFamily="4" osVersion="WA-GUEST-OS-4.10_201407-01" schemaVersion="2014-01.2.3">
The full list can be found at https://msdn.microsoft.com/en-us/library/azure/ee924680.aspx . But please ensure you periodically upgrade the OS as older versions after a certain version are automatically upgraded when that OS version goes out of support.
For a detailed understanding of OS Upgrades I would highly recommend Kevin’s blog. It covers the workflow and almost all the FAQs that you may have around it. https://blogs.msdn.com/b/kwill/archive/2012/09/19/role-instance-restarts-due-to-os-upgrades.aspx
Second Question - How will I know if I am affected
There are several ways and this is not an exhaustive list but will cover a lot of scenarios.
1. After disabling SSL V30, applications will have a compatibility issue only if server/client side application code explicitly set the protocol to 'SSL V3', such as leveraging 'SecurityProtocolType Enumeration'. In general by default .Net Framework will leverage TLS protocol, which is not effected by SSLV3 protocol disabling in Guest VM.
2. Use this site - https://www.ssllabs.com/ssltest/index.html
Provide the name of the cloud service. It will test using various TLS/SSL protocols. The result will show what protocols the Cloud Service is currently capable of and may flag the SSL V3.0 as well. After the latest OS update is rolled out if do the test again you will not see the SSL V3.0 showing up provided you are on the latest update. Please note it’s a two week period and will be rolled in a phased manner.
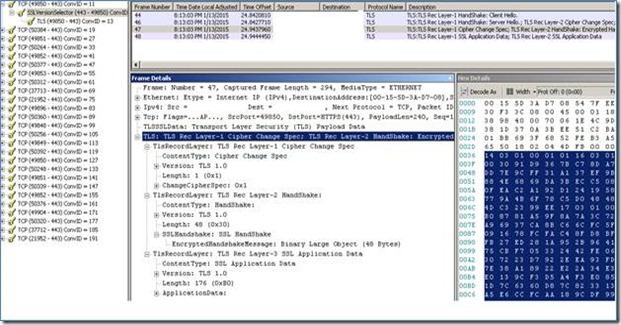
3. . We can quickly verify whether the application is leveraging SSL 3.0 by reviewing a Netmon trace. So look at the communication to the Cloud Service Application from a client and check if it’s using SSL V3.0.
You should expect to see the following and if you see TLS you are just fine.
4. You also test how the Cloud Service is behaving with different clients/browsers as below.
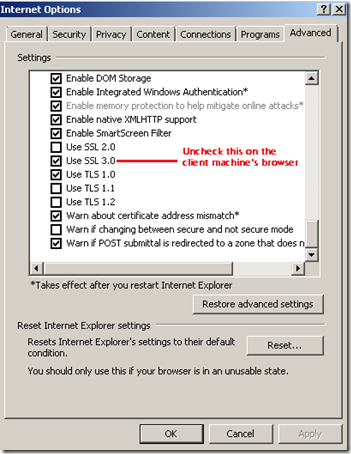
From the client machine where the URL will be accessed do the following.
Internet Options -> Advanced -> Security -> Disable SSL 3.0 and anything lower like SSL 2.0 (which should be any disabled in most browsers unless it’s very old) – This will only leave TLS 1.0 enabled so you browser chooses to uses only TLS. 99% the Cloud Service application should work and you don’t have to worry at all.
5 . If you have a mission critical application, I would suggest you to deploy the same application to the staging environment or a new test cloud service with single instance, and validate whether there is an application compatibility impact when SSL 3.0 is disabled by following the below steps once you have done an RDP into the VM. This script will proactively disable SSL 3.0 support.
How to Disable SSL 3.0 in Azure Websites, Roles, and Virtual Machines
https://azure.microsoft.com/blog/2014/10/19/how-to-disable-ssl-3-0-in-azure-websites-roles-and-virtual-machines/
Test application against staging environment or the new test cloud service.
Third Question How should I plan for updates?
We recommend customers and this is in general (not specific to this update) is to have their cloud services in automatic updates mode to ensure the latest security updates and patches are installed in a timely manner. But if you extremely concerned about breaking changes from security updates then have the production cloud service in manual mode and staging (or a separate extra small cloud service with same code in auto-update mode). Once a new roll out happens and the test cloud service holds fine you can manually update the Production Site from the portal to the newer build. The second advantage is that you can now time the update on your own, like when you have the least users logged in which may be mid-night or a weekend.
Hope this blog has helped you with the questions you might have had around the SSL V3.0 change coming with the new OS update.
Following engineers from the Cloud Integration Engineering team at Microsoft have contributed in getting this blog out.
Angshuman Nayak
Ashish Singh
Om Prakash Gupta
Pradeep Kumar C
Todd Foust
![clip_image002[4] clip_image002[4]](https://msdntnarchive.blob.core.windows.net/media/MSDNBlogsFS/prod.evol.blogs.msdn.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/01/57/80/metablogapi/5280.clip_image0024_thumb_7B94A0DB.jpg)