Azure Power Shell: Azure Virtual Network for the Command Line Junkie – Part 4.2
Web UI looks good and pretty but if you really want to get work done at scale, manage, automate and administer: command line is your way. As a command line junkie from the UNIX world I thought of exploring what Azure PowerShell had to offer. And boy, I was quite blown by the ease of use, functionality and flexibility it comes with. Through this tutorial series, I will take you through various scenarios and functionality on Azure that is made easy using Azure Power Shell
Till now, I have covered the following services in Azure and how we use Power Shell to manage those:
Azure Powerhell: Azure Websites for the command line junkies! – Part 1
Azure Power Shell: Azure Virtual Machines for the command line junkie! - Part 2
Azure Power Shell: Azure Cloud Services for the Command Line Junkie -Part 3
Azure Power Shell: Azure Virtual Network for the Command Line Junkie – Part 4.1
In the last part about Azure Virtual Networks, I had only touched upon how to create a virtual network and how to deploy a virtual machine or a cloud service in the virtual network and ended with adding an internal load balancer to your network. Today we will take a step further and discuss the various topologies of networks such as Hybrid and Multisite networks and how Azure Virtual Network fits into this paradigm.
Point – to -Site Configuration
This option is primarily used when you want few client machines to connect to an existing virtual network, or connect your client from a remote location, or you don't have a vpn device and you want to connect to a virtual network and finally, if you don't have a ipv4 facing public IP to connect to. This is a relatively easy to implement. The idea is simple. All that is required is a gateway, then create certificates to authenticate clients that will be granted access to the virtual network.
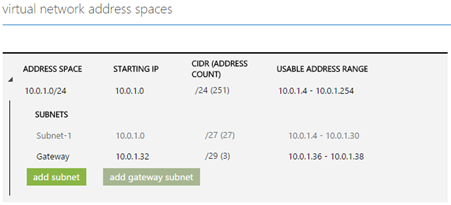
When you create a Virtual Network from the Management Portal itself and choose a Point-to-site network you enter details of the subnet as well as the gateway.
As described in the previous article about how you could create a virtual network and subnets, you can also add a gateway using the following cmdlet:
1: New-AzureVNetGateway -VNetName "Mars_VNET" -GatewayType DynamicRouting
Once this is done, you should create a certificate to be uploaded to the VNET and a client cert which the client will use to access the virtual network. Let us see how this is done.
Step 1: Create root certificate to be uploaded to the virtual network:
1: makecert -sky exchange -r -n "CN=P2SRootCert" -pe -a sha1 -len 2048 -ss My
2: .\P2SRootCert.cer
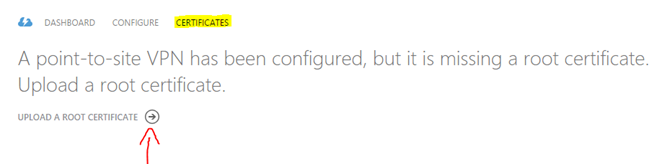
Now upload this directly to the Azure virtual network using the management portal as there is no cmdlet for this. Go the management portal, click on the point-to-site network that you created and click on the Certificates tab:
Step 2: Once the root certificate is uploaded, you need to create the client certificate and upload it on the client
1: makecert.exe -n "CN=P2SClient" -pe -sky exchange -m 96 -ss My -in "P2SRootCert" -is my -a sha1
Now this certificates needs to be installed on the client machine. This certificate will be stored in the personal certificate store. You can use certmgr.msc to export and install the certificate on your client device.
Site-to-Site
As the name suggest, this is connecting an on-prem network to a virtual network. The differentiation lies in the fact that you do not connect individual client machines to your existing virtual network. A VPN device is used to connect your on-prem network to a virtual network, after which all your machines on-prem can communicate with all your machines on site. This topology is perfectly suited when you want to create a branch office solution or create a hybrid solution between your on-prem network and your Azure Virtual network. There is very little that can be done using PowerShell to configure this and hence should be configured on the management portal directly. Configure a Virtual Network with a Site-Site VPN connection clearly explains the steps involved.
Express Route
When you want to connect collocated networks, or create a dedicated private connection between data centers, an Express Route does not go over the public internet but gives a dedicated reliable route with faster speeds and lower latencies to communicate with each other. This is done by a third party provider such as Internet Exchange Provider (IXP) or Network Service Provider (NSP). The Express Route Technical Overview discusses this implementation in detail. Again, there is little or no application of this from a PowerShell point of view.
Conclusion
Through this post I just tried to cover the basics of Virtual network and how it relates to PowerShell. By no means the purpose was to cover virtual networks. Azure Virtual Network can be an advanced topic and can be very flexible and customizable based on the implementation architecture. However, from a powershell point of view, there is not much functionality that can be exploited in virtual networks hence the limitations to these articles. I will delve deeper into Virtual networks with more scenario specific implementations in the future.
Stay tuned in for more such ‘snackable’ tutorials. Reach out to me @AdarshaDatta and let me know if there are any specific areas that you want to learn about and we can learn them together.
Technorati Tags: virtual Network,azure,cloud,infrastructure-as-a-service,iaas,powershell,commandLine,Devops