Information Card Issuance: a small step for "Geneva" Server, a big leap for Federated Identity
Imagine this: you have been following this blog and have decided to try “Geneva” Beta 2. You have gone to the connect site and downloaded the "Geneva" platform components, installed them, configured the server, used the framework to write a claims-aware uber cool application, and set up trust between your server and the application. Now your users can log in and use your application and you can manage access easily. But that uses only two out of the three "Geneva" products. What does it mean to incorporate CardSpace "Geneva" into this scenario? From the server perspective, it means configuring information card issuance.
Intro
The "Geneva" Server in this scenario is configured to use the active directory that contains all your users. We call this role an Identity Provider STS because it authenticates users and produces tokens about their identities. One of the powerful features that “Geneva” Server gives an STS is the ability to issue cards that CardSpace "Geneva" stores and allows you to use to authenticate. For more information on cards see: https://blogs.msdn.com/card/archive/2008/05/20/backing-a-managed-card-with-alternate-credentials.aspx
Each part of our scenario needs to be properly configured:
· Your users need to have CardSpace “Geneva” installed (or compatible Identity Selector)
· The Server needs to issue cards.
· The application needs to support card selector log in
"Geneva" Server Card Issuance
Configuring a card is simple: the initial configuration wizard sets all required parameters. You can update any and all of them at any time. List of the parameters you can set:
· Card name
· Card image (typically your organization's logo)
· Privacy Notice (optional)
· Authentication type (more in the next paragraph)
· Certificate to sign the card (this is located in the certificate settings)
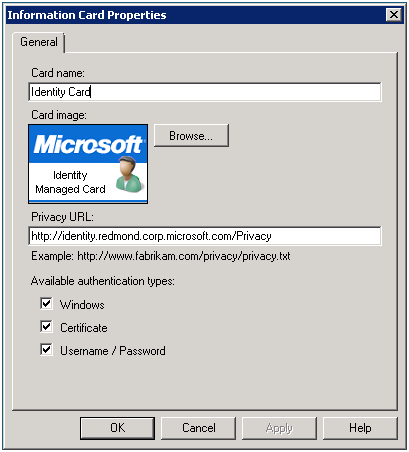
Choosing an authentication type depends on your deployment, and the strength of authentication you wish to enforce. “Geneva” Server Beta 2 supports three types of authentication:
· Windows – by selecting this type, CardSpace performs Windows Integrated Authentication, which only works when the user is connecting from the internal network.
· Certificate – by selecting this type, CardSpace authenticates with a user certificate located on the user’s machine. This type works well for smart cards, and is especially useful for authenticating users outside of the corporate network in a highly secure way.
· Username and password – by selecting this type, CardSpace prompts the user for their domain user name and password. This type also works for authentication outside the corporate network.
The order of the authentication types will always be first Windows if present, next Certificate if present and last Username Password if present. The implication of this is that if you can turn on two authentication types, for example Windows and Certificate. Then inside a corporate network, users would automatically get authenticated with Windows Integrated Authentication. Outside a corporate network where Integrated Authentication is not available, authentication falls down on the next authentication type and users will get authenticated by their user certificate.
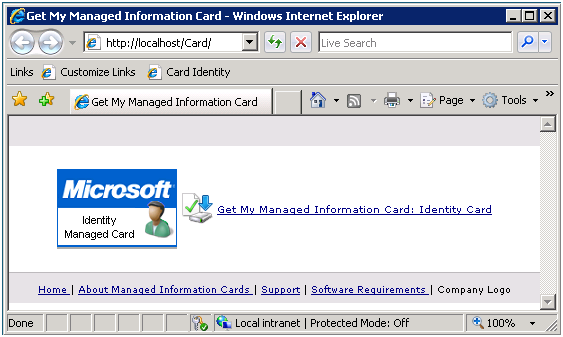
The initial configuration wizard does one more thing for you. It deploys a card issuance website from where users can download your spiffy new card. Note that by default access to the site is windows authentication based. Once the website is deployed you can customize it with your organization's name, logo, contact information, etc.
Tips
A subset of the settings that are part of the card file your users will download is derived directly from the STS settings. However to give the administrator more control over the process, changes to the STS that affect the card will not be applied to the card until the administrator chooses to do so and clicks the “Update Information Card” action.
The “Geneva” Server Beta 2 gives you a powerful new way to configure and maintain your configuration: PowerShell. I’d like to briefly note that there is a resource dedicated to configuring card issuance: GSInformationCard. There are five different cmdlets/verbs associated with this resource:
· Get-GSInformationCard,
· Set-GSInformationCard,
· Enable-GSInformationCard,
· Disable-GSInformationCard
· Update-GSInformationCard.
The GSInformationCard resource covers all UI capability and some additional parameters not visible in the UI, like explicitly adding claims and in depth management of certificate backed cards amongst others. Look to future posts for more details.
Conclusion
As you can see, “Geneva” Server provides quick access to the world of information cards:
· Simple, secure provisioning of cards to users
· Simple administration of the card
· Flexibility to provide/ensure specific authentication types
· Customizable site to provide users with familiar corporate site experience
A great reference for setting up information card issuance you can find here: https://technet.microsoft.com/en-us/library/dd807042(WS.10).aspx. And in the next post you are going to learn about a powerful feature build on top of card provisioning: silent card provisioning.
Veneta Tashev
Software Development Engineer in Test
“Geneva” Server Team