Windows Azure Access Control Service-Understanding the Security Buzzwords
Exercise 1: Overcoming Acronym Overload
This post is here because I got acronym overload. I am reading about the Windows Azure Access Control Service and there is support for all these industry standards, such as OAuth, ws-trust, ws-federation, and so on.
I’m doing the Windows Azure Cloud camp tomorrow, so this should help supplement my discussion of the ACS and what it means.
If you are in Redmond on 4/27, then come see me. https://msevents.microsoft.com/CUI/EventDetail.aspx?EventID=1032507378&Culture=en-US
What do these fancy terms really mean?
Exercise 1: Task 1 - First, what is the Windows Azure Access Control Service (ACS)?
Here is a quick outline that describes (at a high level) what is the ACS
- ACS makes it easy to authenticate and authorize users.
- You don't need to spend much time worrying about the vast landscape of changing security standards.
- ACS is a cloud-based service that provides an easy way of authenticating and authorizing users to gain access to your web applications and services while allowing the features of authentication and authorization to be factored out of your code.
- Because it is a service, all that security plumbing code is something you DO NOT NEED to worry about.
- ACS supports integrated Single Sign On and centralized authorization into your web applications
- Users hate having to log on mutliple times. If you want to retain your users, you need to allow them to just login once.
- ACS provides out-of-the-box support for Active Directory Federation Services (AD FS) 2.0
- Great integration story with on-premise corporate users.
- ACS relies on Standards-based identity providers
- Web identities include Windows Live ID, Google, Yahoo! and Facebook
- Integrates with Windows Identity Foundation and tooling
- The Windows Identity Foundation helps simplify user access for developers by externalizing user access from applications via claims and reducing development effort with pre-built security logic and integrated .NET tools.
- This is a powerful toolkit available from MS
- https://www.microsoft.com/download/en/details.aspx?displaylang=en&id=17331
- The modern way to manage security
- Claims-based access control
- Support for OAuth WRAP, WS-Trust, and WS-Federation protocols
- Details below. This is the point of this quick post.
Exercise 1: Task 2 - What is OAUTH WRAP?
- OAuth is an open standard for authorization.
- OAuth provides a method for clients to access server resources on behalf of a resource owner (such as a different client or an end- user).
- It allows end-users to authorize third- party access to their server resources without sharing their credentials
- Typically accomplished with, a username and password pair, using user- agent redirections.
- It started with Twitter during the OpenID implementation.
- It allows users to share their private resources (e.g. photos, videos, contact lists) stored on one site with another site without having to hand out their credentials, typically supplying username and password.
- Instead, tokens are used.
- Each token grants access to a specific site (e.g., a video editing site) for specific resources (e.g., just videos from a specific album) and for a defined duration (e.g., the next 2 hours).
- This allows a user to grant a third party site access to their information stored with another service provider, without sharing their access permissions or the full extent of their data.
- DeWitt Clinton from Google joined OAuth project, supporting the effort. In July 2007 the team drafted an initial specification.
- Facebook's new Graph API only supports OAuth 2.0 and is the largest implementation of the emerging standard
Exercise 1: Task 3 - What is OASIS?
It is more than a small fertile or green area in a desert region, usually having a spring or well. Actually it is a global consortium.
- OASIS stands for Organization for the Advancement of Structured Information Standards (OASIS)
- It was started in 1993
- OASIS is a global consortium that drives the development, convergence, and adoption of e-business and web service standards.
- Headquarters in the United States
- Members of the consortium decide how and what work is undertaken through an open, democratic process
- Focused on Web Services, e-Commerce, Security, Law & Government, Supply Chain, Computing Management, Application Focus, Document-Centric, XML Processing, Conformance/Interop, and Industry Domains
Exercise 1: Task 4 - What is WS-Trust?
WS-Trust is a WS-* specification and OASIS standard
- WS-Trust is a WS-* specification and OASIS standard
- It has defined some important industry terms
- WS-Trust spawned concept of a Security Token Service (STS)
- An STS web service that issues security tokens as defined in the WS-Security specification.
- WS-Trust spawned concept of a Security Token Service (STS)
- It provides extensions to WS-Security, specifically dealing with the issuing, renewing, and validating of security tokens
- It addresses the formats of the messages used to request security tokens
- It defines the responses from the server to such messages
- It also addresses mechanisms for key exchange
- WS-Trust also deals with ways to establish, assess the presence of, and broker trust relationships between participants in a secure message exchange
- WS-Trust is supported by Microsoft's Windows Communication Foundation (WCF) and Windows Identity Foundation (WIF), Sun's WSIT framework, Apache's Rampart (part of axis2), and others.
- WS-Trust is a specification developed by nal Corporation, BEA Systems, Inc., Computer Associates International, Inc., International Business Machines Corporation, Layer 7 Technologies, Microsoft Corporation, Oblix Inc., OpenNetwork Technologies Inc., Ping Identity Corporation, Reactivity Inc., RSA Security Inc., and VeriSign Inc.
Exercise 1: Task 5 - What is WS-Federation?
WS-Federation is a WS-* specification and OASIS standard
- Tries to tackle the security challenges in web applications and web services in a variety of trust relationships.
- WS-Federation supports SOAP clients and web services.
- REST is not supported.
- WS-Federation provides a common model for performing Federated Identity operations for both web services and browser-based applications.
- WS-Federation builds upon the Security Token Service model
- WS-Security, WS-Trust, and WS-SecurityPolicy provide a basic model for federation between Identity Providers and Relying Parties
- WS-Federation are claims-based.
- Claims are just dictionaries inside of a SAML token where key value pairs represent the attributes of a user
- Developers can iterate through dictionary to see attributes of a user’s identity to determine what kind of claims we want to authorize
- These claims are also called assertions.
- WS-Federation are claims-based.
- WS-Federation strives for richer trust relationships
- It wants to join together HTTP with STS and WS-Trust to allow resources in one realm get identities (and related attributes) that are managed and maintained in another realm.
- You can imagine scenarios where WS-Federation is needed, such as protecting patient records from unauthorized users when these patient records are traveling among multiple health providers. Federation makes sense in a supply chain scenario where a factory needs just-in-time inventory levels from distributors or retailers (and in reverse).
- You can read more here
Exercise 1: Task 6 - Key Value Proposition for ACS is Single Sign On
The diagram below illustrates how the ACS supports Single Sign On.
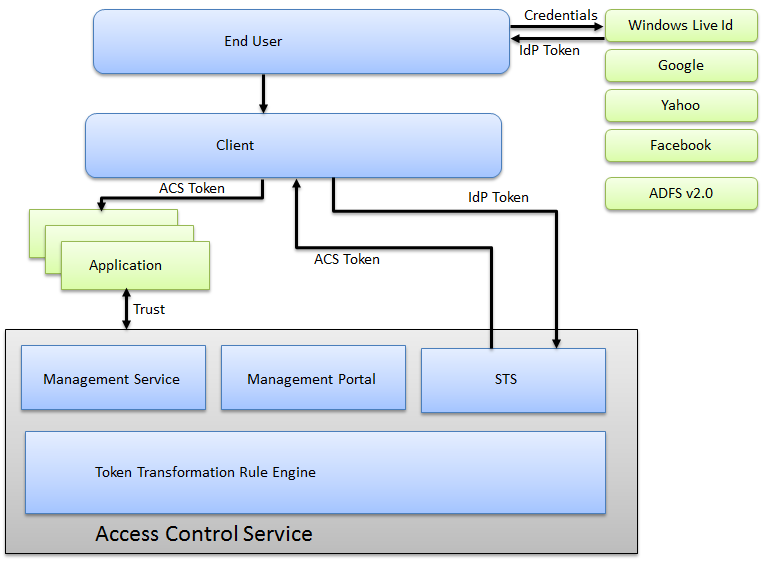
- Single Sign on is made possible by the STS (Security Token Service) in conjunction with other pieces.
- The goal is to create a token, an ACS token, which is a token that conforms to industry standards SAML based tokens.
- It starts with the end user starting an application or a browser instance.
- The user typically will get redirected to an identity provider, providing their credentials, getting back an identity provider token.
- This token, specific to an identity providers, gets forwarded automatically to ACS.
- The ACS will transform this token into a standard SAML token.
- It will use rules specified by a developer
- Claims will be embedded into the token
- These claims will allow client applications to authorize restricted operations
- Various applications can be forwarded this token, thus supporting the Single Sign On Scenario
- There are several challenges associated with the scenario that the ACS solves. This means, you, the developer, do not need to deal with these headaches.
- How to redirect unauthenticated requests to the required identity provider?
- How to validate the incoming token issued by the identity provider?
- How to parse the incoming token?
- How to implement authorization checks?
- How to transform tokens by adding, removing, or changing the claims types and values?
- How to do all of the above using configuration rather than coding?
- You can read more here:
Download for Azure SDK |