Azure Log Integration SIEM configuration steps
NOTE:
This blog post is outdated and some of the steps may not work correctly. If you have problems, please let us know at the Azure Log Integration forum
This document provides screen shots of audit logs and Azure Security Center alerts integrated with the following partner solutions:
- Splunk
- HP ArcSight
- IBM QRadar
The machine that Azure log integration services is installed on is called the Azlog Integrator. Your SIEM agent (the Splunk Universal Forwarder, HP ArcSight Windows Event Collector agent, or IBM QRadar WinCollect) is also installed on the Azlog Integrator. Azure log integration puts the Windows Event logs in the Forwarder Events channel.
Make sure that your standard SIEM connector installed on the machine is configured to pick events from the Forwarded Events folder and pipe them to your SIEM instance. Review the SIEM specific documentation for configuration details.
Splunk
For information on forwarding data from Microsoft Windows to Splunk, refer to Splunk’s documentation.
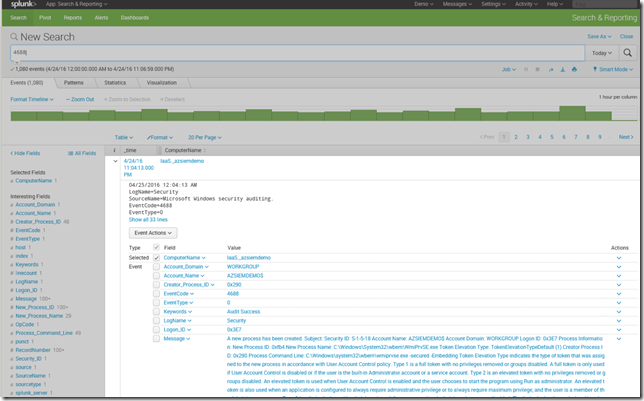
The following example shows events coming from ComputerName Iaas_azsiemdemo.
Integration of Azure Audit Logs in Splunk
Use Splunk Universal Forwarder to point to c:\Users\azlog\AzureResourceManagerJson as below
splunk add monitor C:\Users\azlog\AzureResourceManagerJson
splunk restart
The following screen shot shows logs in Splunk.
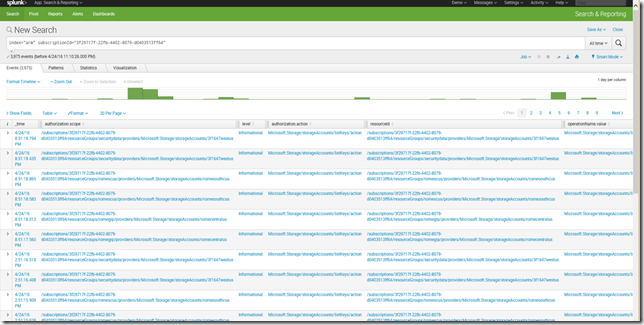
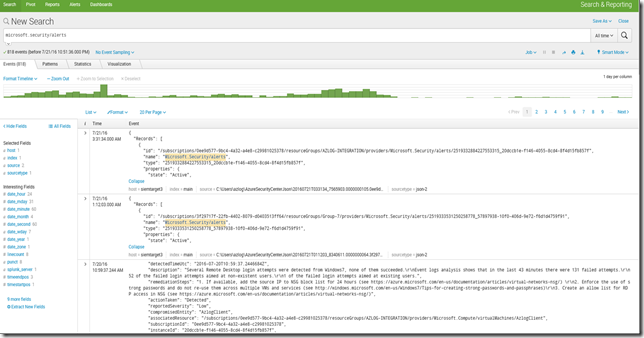
Integration of Security Center alerts in Splunk
Use Splunk Universal Forwarder to point to C:\Users\azlog\AzureSecurityCenterJson as below:
splunk add monitor C:\Users\azlog\AzureSecurityCenterJson
splunk restart
The following screen shot shows Security Center alerts in Splunk.
HP ArcSight
For information on forwarding data from Microsoft Windows to HP ArcSight, refer to ArcSight’s documentation.
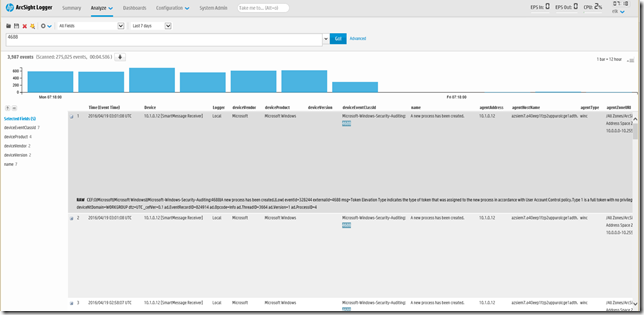
The following example shows Windows events coming from Azure VMs into ArcSight.
Integration of Azure Diagnostic Logs in ArcSight
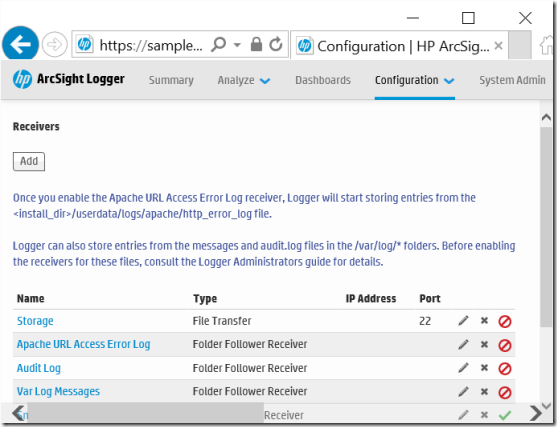
1. Create a SmartMessage Receiver.
If you do not have a SmartMessage Receiver, create one in ArcSight Logger selecting Configuration. Under Configuration, select Receivers.
2. Select Add.
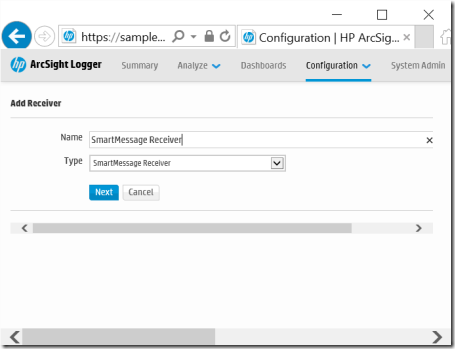
3. In this example, under Add Receiver, let’s use SmartMessage Receiver for the Name and Type. Select Next.
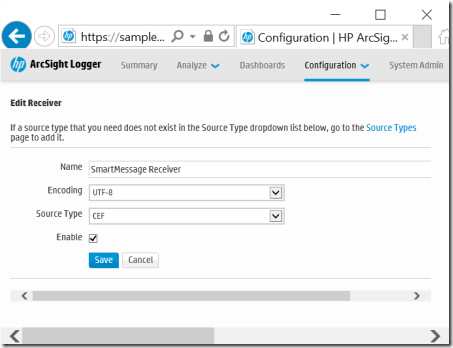
4. Under Edit Receiver, choose settings below and select Save.
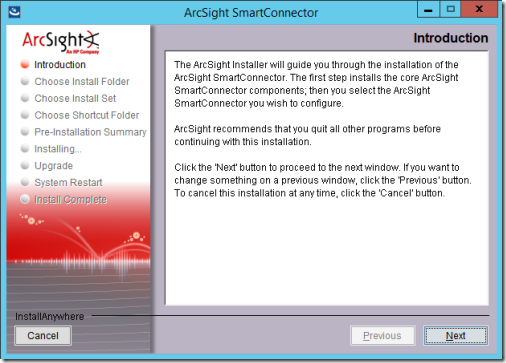
5. On the Windows machine with the Azure SIEM Integration Service, launch the ArcSight SmartConnector installation wizard and select Next.
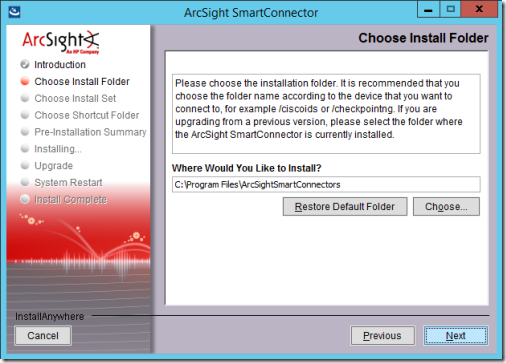
6. On the Choose Install Folder page, identify path to where you want to install and select Next.
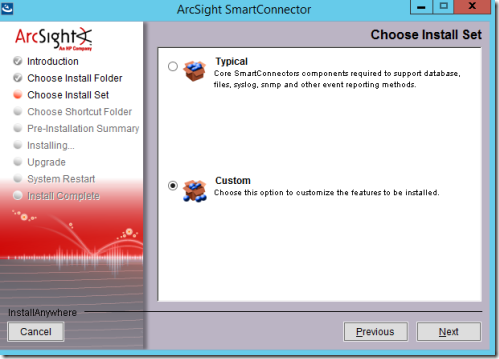
7. On the Choose Install Set page, select Custom and then Next.
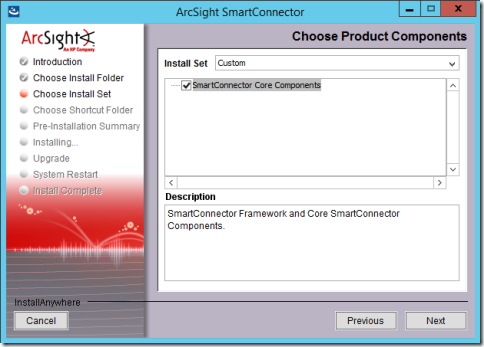
8. On the Choose Product Components page, choose settings below and select Next.
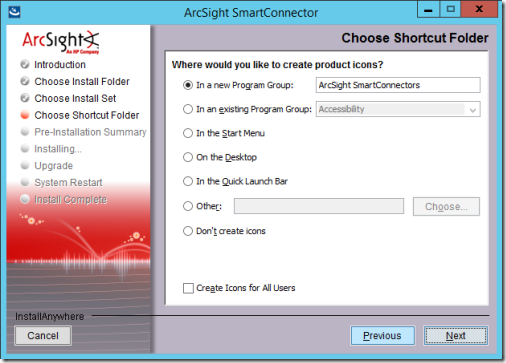
9. On the Choose Shortcut Folder page, choose settings below and select Next.
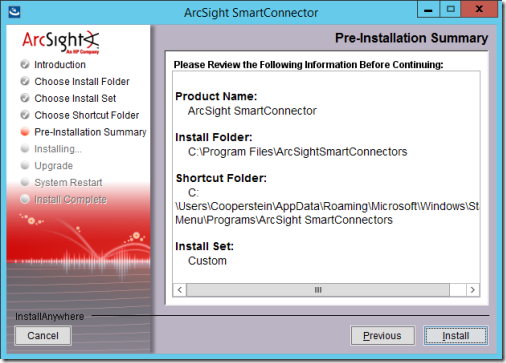
10. On the Pre-Installation Summary page, select Install.
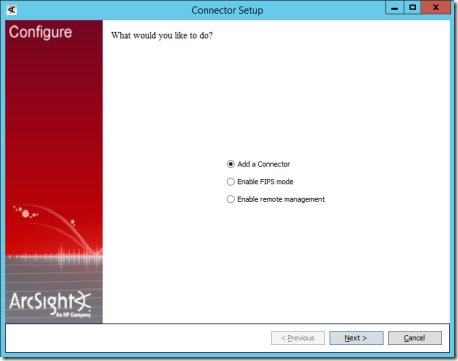
11. On the Connector Setup page, select Add a Connector and select Next.
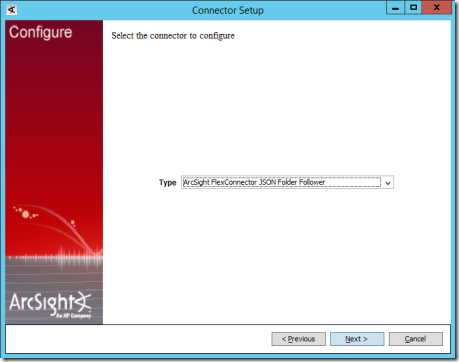
12. On the next Connector Setup page, choose ArcSight FlexConnector JSON Folder Follower and select Next.
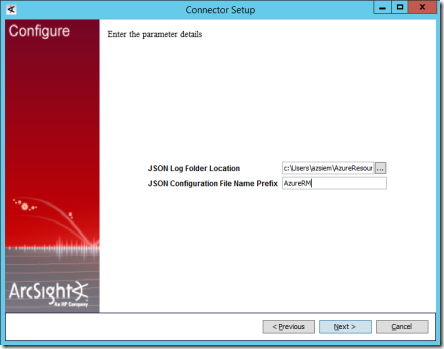
13. On the next Connector Setup page, set the Folder Location to the path where JSON logs are being written to (for example, c:\Users\azlog\AzureResourceManagerJson)and set the Configuration File Name Prefix to AzureRM. Select Next.
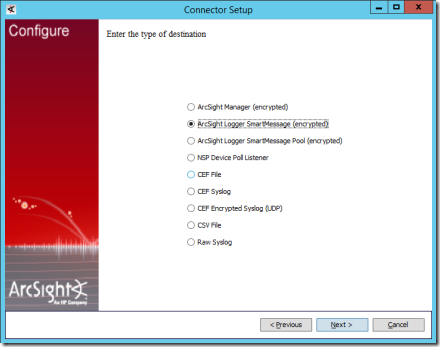
14. On the next page, select ArcSight Logger SmartMessage(encrypted) and select Next.
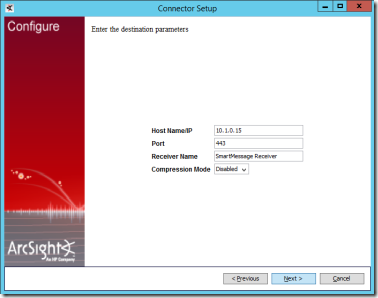
15. On the next page, enter the ArcSight Logger machine’s IP address, the Receiver Name of the SmartMessage receiver (for example, SmartMessage Receiver) and select Next.
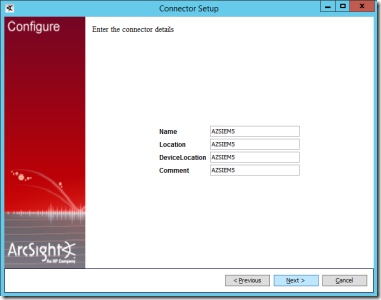
16. On the next page, fill in information about the connector machine (example information shown) and select Next.
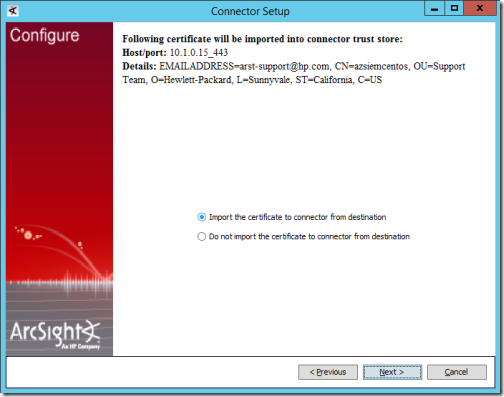
17. The next page may be shown to import the certificate from the ArcSight Logger machine. Select Next.
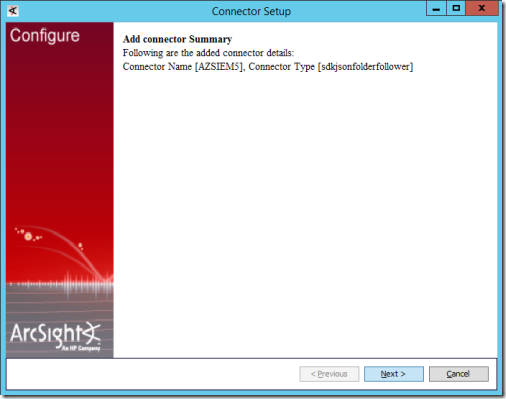
18. Review the summary on the next Connector Setup summary page and select Next.
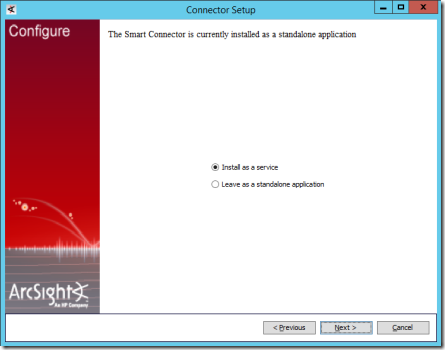
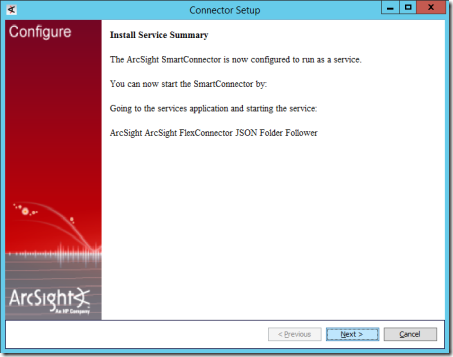
19. On the next page select Install as a serviceand select Next.
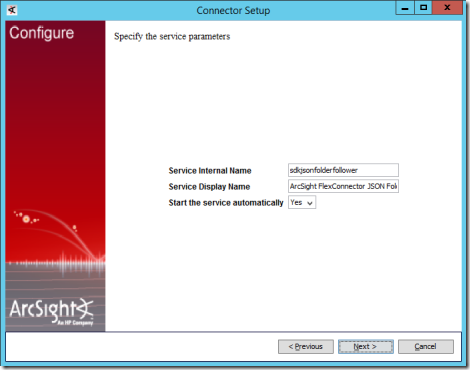
20. On the next page, leave the defaults as is and select Next.
21. Review the summary on the next page and select Next.
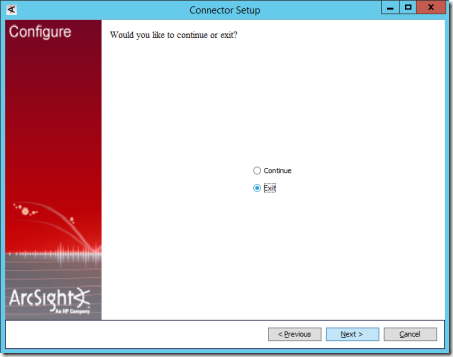
22. On the next page, select Exit and select Next.
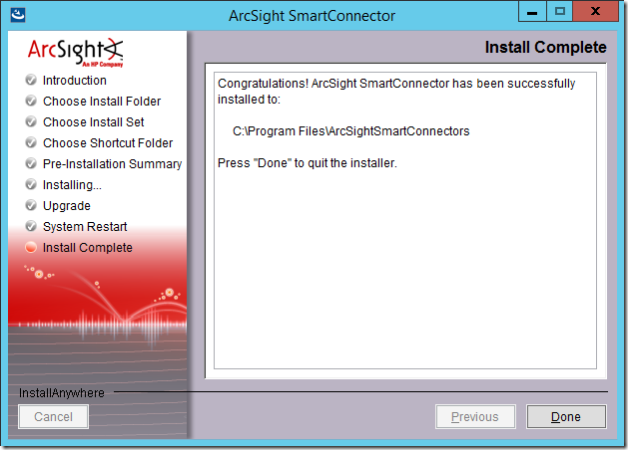
23. You should now see the Install Complete page. Select Done.
After the installation wizard is complete, copy the AzureRM.jsonparser.properties file (downloaded as part of Azure log integration) to \Program Files\ArcSightSmartConnectors\current\user\agent\flexagent\AzureRM.jsonparser.properties. The contents of AzureRM.jsonparser.properties can be modified as needed to change the mapping of Azure Resource Manager log entries to ArcSight events. See HP’s Flex Connector documentation for the format of this file.
At this point, the ArcSight ArcSight FlexConnector JSON Folder Follower service should be stopped. If not, stop it from the Services Control Panel application or from the command line using command :
net stop "ArcSight ArcSight FlexConnector JSON Folder Follower
Note:
The exact service name may be different if non-default options were chosen during setup.
Stopping the service should ensure that the AzureRM.jsonparser.properties file is picked up.
Now, start the service from the Services Control Panel or from the command line using this command:
net start "ArcSight ArcSight FlexConnector JSON Folder Follower
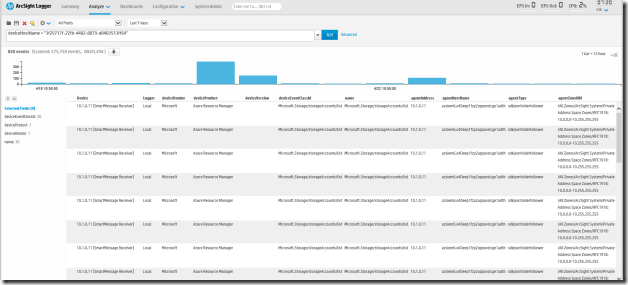
Events should now be flowing to the ArcSight logger. Following is a screenshot of Azure Audit logs in ArcSight:
IBM QRadar
Integrate Windows Event Logs into QRadar
Azure Log integration collects Windows VM logs into the Windows Forwarded Event Channel. This is documented in the topic Getting Started with Azure Log Integration. You will need to further install and configure the IBM QRadar Wincollect agent on the Azure Log Integration machine to integrate events from the Windows Forwarded Event channel into QRadar. To do this refer to the IBM QRadar Wincollect documentation at:
Integrate Azure Activity Logs and Azure Security Center Alerts into QRadar
To integrate Azure Activity logs and Azure Security Center Alerts over Syslog to QRadar, please visit this blog post.