Get More Out of Azure Security Center with Power BI
 Last week on the Azure Blog Sarah Fender announced a collection of very cool new capabilities for Azure Security Center. There's something for everyone there! One that caught my attention was the new ability to use Power BI to get even more visibility into the security state of your Azure deployments.
Last week on the Azure Blog Sarah Fender announced a collection of very cool new capabilities for Azure Security Center. There's something for everyone there! One that caught my attention was the new ability to use Power BI to get even more visibility into the security state of your Azure deployments.
If you're new to Azure (or even if you're not new), you might not have heard of Power BI. From a high level, Power BI is a collection of analytics tools that are able to dig into data from multiple sources to give you interesting and intuitive dashboards that make it easier for you to interpret the information. You can also create nice looking reports to make the data "pop" and get the right points across.
This is what makes Power BI so useful in the context of Azure Security Center. Power BI gives Azure Security Center even more flexibility and customization so that you can see the things that are important to you. You can also connect information from other data sources, such as Azure Audit Logs and Azure SQL database audit logs to create visual correlates. And if you're a friend of Excel, you can export all this information and import it into an Excel spreadsheet.
Azure Security is at RSA this this week!
If you’re at RSA, look up Sarah and learn more about Azure Security Center
Let's see what it looks like!
First, you need a Power BI account. If you already have one, then continue on in the Azure portal. If not, use the Get started free link on Power BI page to sign up.
When you go into Azure Security Center from within the Azure portal, you'll notice that there's a "button" in the console that says Explore in Power BI
When you click that button you'll be asked for what subscription you want to see in Power BI. You’re then given an opportunity to copy your subscription ID to the clipboard (which is a nice convenience). You then click the Go to Power BI link and log into Power BI.
When you get there, you'll see the following - click Connect.
You'll be asked to perform some authentication (make sure you use oAuth2) steps.
After you log in, the dashboard will be built and when complete, you'll see something like this:
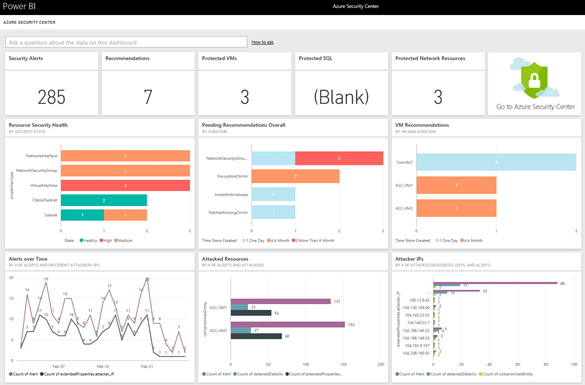
(click the picture to see it full size)
At the top you can see a summarized view of Security Alerts, Recommendations, Protected VMs, Protected SQL (shows "blank" because I don't have any Azure SQL instances in this subscription), and Protected Network Resources.
There are default tiles that provide you information on Resource Security Health, Pending Recommendations Overall, VM Recommendations, Alerts over Time, Attacked Resources, and Attacker IPs.
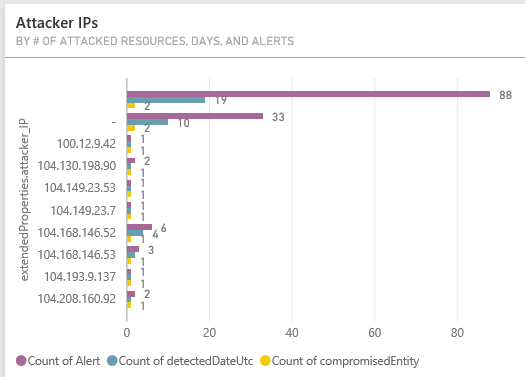
There's a lot of information here, and you can drill down by hovering over or clicking just about any element in the graphs. Let's take a closer look at the Attacker IPs.
Click on an empty space in the Attacker IPs tile.
(click on the graphic to see a full view)
Here you can see:
- Alerts over time by # of Alerts and Different Attackers IPs - this is great to see attack trends
- Attacker IP by # of Compromised Entities, # of Attacks Detected, and # Of Attack Days Detected - this is useful to see where the attacks are coming from and to get a visual impression on who might be the major offenders
- Attacked Resources - lets you easily see what resources are most impacted by the attacks
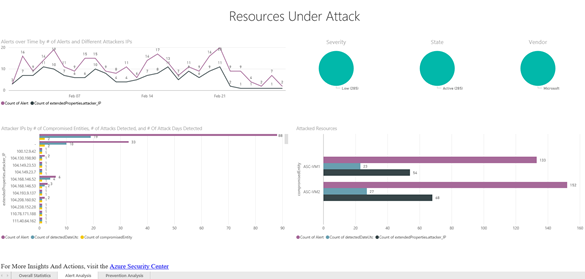
If you hover over any of the bars in the graph you will see more information about that bar, and if you click the bar, you will see drill-down information, such as seen in the figure below.
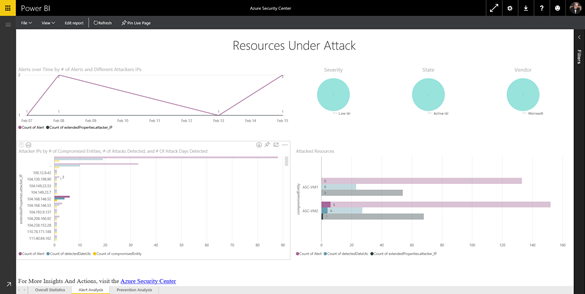
(click the graphic to see the full figure)
As you can see, there's a ton of information available in the Power BI presentation of your Azure Security Center data. I hope I was able to whet your appetite for more information on Azure Security Center integration with Azure Security Center!
To learn more about Power BI integration with Azure Security Center, check out the article Get insights from Azure Security Center data with Power BI.
Thanks!
Tom
Tom Shinder
Program Manager, Azure Security
@tshinder | Facebook | LinkedIn | Email | Web | Bing me! | GOOG me!