Application Compatibility - IE7 Protected Mode
Friday, April 20, 2007 4:44 AM
On Windows Vista, Internet Explorer 7 runs in Protected Mode, which can help protect users from attack by running the Internet Explorer process with greatly restricted privileges. Protected Mode significantly reduces the ability of an attack to write, alter, or destroy data on the user's machine or to install malicious code. It can help protect a user from malicious code installing itself without authorization. This is the default mode for Internet Explorer when Windows Vista is installed.
OK - so how exactly will this problem manifest itself?
- Applications that use Internet Explorer 7 will not be able to write directly to disk while in the Internet or Intranet zone.
- Applications may not know how to handle new prompts.
Protected Mode builds on the new integrity mechanism to restrict write access to securable objects like processes, files, and registry keys with higher integrity levels. When run in Protected Mode, Internet Explorer is a low-integrity process; it cannot gain write access to files and registry keys in a user's profile or system locations.
Low-integrity processes can only write to folders, files, and registry keys that have been assigned a low-integrity mandatory label. As a result, Internet Explorer and its extensions run in Protected Mode, which can only write to low-integrity locations, such as the new low-integrity Temporary Internet Files folder, the History folder, the Cookies folder, the Favorites folder, and the Windows Temporary Files folders.
Furthermore, the Protected Mode process runs with a low desktop integrity level, which will prevent it from sending specific window messages to higher integrity processes.
By preventing unauthorized access to sensitive areas of a user's system, Protected Mode limits the amount of damage that can be caused by a compromised Internet Explorer process or malware. An attacker cannot, for example, silently install a keystroke logger to the user's Startup folder. Likewise, a compromised process cannot manipulate applications on the desktop through window messages.
Of course, these defenses also limit legitimate changes to higher integrity locations. As a result, Protected Mode provides a compatibility architecture that reduces the impact on existing extensions, as shown in the following figure.
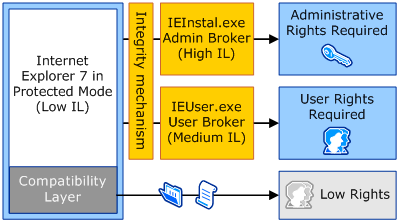
A compatibility layer handles the needs of many existing extensions. It intercepts attempts to write to medium integrity resources, such as the My Documents folder in the user profile and the HKEY_CURRENT_USER registry hive. The compatibility layer uses a generic Windows compatibility fix to automatically redirect these operations to the following low-integrity locations:
- %userprofile%\LocalSettings\Temporary Internet Files\Virtualized
- HKEY_CURRENT_USER\Software\Microsoft\InternetExplorer\InternetRegistry
Two higher privilege broker processes allow Internet Explorer and extensions to perform elevated operations given user consent. For example, the user privilege broker (IEUser.exe) process provides a set of functions that let the user saves files to areas outside of low-integrity areas. In addition, an administrator privilege broker (IEInstal.exe) process allows Internet Explorer to install ActiveX controls.
So what are some ways you might be able to resolve this issue? There are two Quick solutions - one of which is not recommended as your long-term solution!
- Add the site in question to the trusted sites list.
- Turn off Protected Mode (not recommended as a long term solution!).
In terms of Compatibility testing, you should add the site to the Trusted Sites list and ensure that the application can perform the dependent functions on a clean Windows XP SP2 machine with IE7 loaded. If the problem only occurs on Windows Vista, then you could be experiencing the issue due to the changes implemented with Protected Mode.
In the long-term, the best solution would be to modify the application to handle Protected Mode correctly, including any related prompts that may be displayed. However - many developers and IT Administrators will be tempted to simply turn off Protected Mode. We strongly urge you to not do this - especially as your long-term solution!
Additional Resources: