IE7 - Introducing the Phishing Filter
Friday, March 16, 2007 9:37 AM
Before looking at the new Phishing Filter for IE7 and what it does, it is important to understand what Phishing is, and some common Phishing techniques.
Phishing is a criminal activity. Using social engineering techniques, phishers attempt to fraudulently acquire sensitive information - such as usernames, passwords, credit card details and bank account information by pretending to be trustworthy entities in an electronic communication (such as an email or instant message). A common practice includes sending an email to a user that supposedly comes from a bank or online payment service. The email contains a link that appears to be legitimate to an unsuspecting user but is actually a malicious website. Phishing attacks have become more sophisticated in recent years - using techniques such as Link Manipulation, Website Forgery and even Phone phishing to carry out the attack. The Wikipedia link below contains more details about each of these techniques as well as some examples of common phishing attacks. The damage caused by phishing ranges from loss of email access to substantial financial loss. The Anti-Phishing Working Group (APWG) - an industry association focused on eliminating the identity theft and fraud that result from the growing problem of phishing and email spoofing, reported that they tracked over 37,000 phishing spoof sites in November 2006.
So what defenses do you have against these phishers? With the launch of IE7, Microsoft released an Anti-Phishing Filter. This filter is also available as an add-in for the MSN Search Toolbar. The Phishing Filter is a feature designed "... to help protect users from phishing websites, while maintaining user privacy and being transparent and flexible about how we do it. Protecting your privacy means we will not collect personally identifiable information, we will explain clearly how the feature works, we will give you the choice to use it only when you want to, we will provide a clear indication of how we will use any data, and we’ll use SSL encryption to help protect any queries you send to the anti-phishing server. " (Rob Franco - IE Blog Post)
OK - so enough with the marketing blurb - how does it work? In IE7, the first step is to opt-in to the feature to active the filter's dynamic protection. The Anti-Phishing Filter uses an online reputation service that is used to verify the websites. When you enter a web address in the browser, the Phishing Filter first checks the local browser .DAT file and the URL local cache for a match to a previously rated site. The URL checked does not include any personal information, only the domain and path (https://domain.com/path is what is checked as opposed to https://domain.com/path?username=username&password=password or something similar). If a match is found then the user is presented with one of the warnings below. If no match is found locally, then the Phishing Filter contacts the Microsoft URL Reputation Web Service (URS). If a URS match is identified, then the user either continues to the site, or is presented with one of the warnings below based on the URS site rating. If no match is identified, then the URS returns a rating of "Unknown" to the Phishing Filter. The URS database itself is populated from nine 3rd party sources including AusCERT, BrandProtect, MySpace.com, RSA and Netcraft.
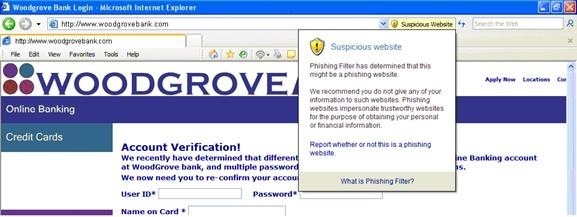
There are two levels of warning. The first (Suspected Phishing site, but not confirmed), is a "Yellow Alert" that indicates that the filter has detected that the site exhibits characteristics similar to a phishing site (see the image below).
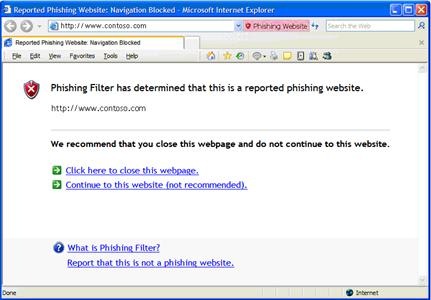
The second (and more severe) warning is the "Red Alert" warning that indicates that the Phishing Filter has detected a confirmed reported phishing website. At this point IE7 navigates the user away from the page and presents a warning such as the one below. Users are presented with the option to Close the Page, or Continue to the site at their own risk.
So where does the browser get its list of phishing sites and how do you know it's working? Let's answer the second question first. When you browse to a website using IE7, look down in the toolbar. The small icon in the toolbar (circled in red) indicates that the browser is checking the site against known phishing sites:
IE does maintain a downloaded list of "High Traffic" sites, however the browser performs a real-time check against an online list of known phishing sites that are updated several times an hour if the site is not part of the "High Traffic" list.
So why are we doing real-time lookups instead of downloading a list of phishing sites on a periodic basis similar to the High Traffic sites? The speed and sophistication of phishing attacks nowadays is such that even if we downloaded a list of sites once an hour, there still remains a one-hour period in between updates in which a user may be vulnerable to a new attack. Because the phishing filter checks are real-time lookups against a centralized location, the browser is always using the latest intelligence. In addition, consider the sheer volume of network traffic that would be generated by updating this list once an hour to every IE7 client connected to the Internet!
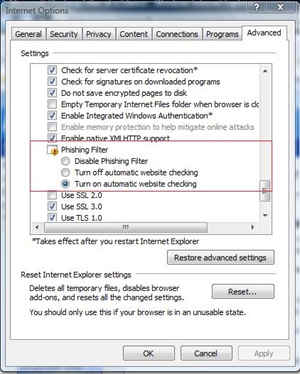
Remember, that the Phishing Filter is an "Opt-In" feature. That means that you can turn it off at your own discretion. The feature is enabled / disabled via the Advanced IE options or via the Tools menu as shown below - you can choose to completely disable the feature, or only turn off the automatic website checking feature. By turning off the automatic checking feature, you still maintain the ability to check individual sites via a manual process using the Tools --> Phishing Filter options on the menu.
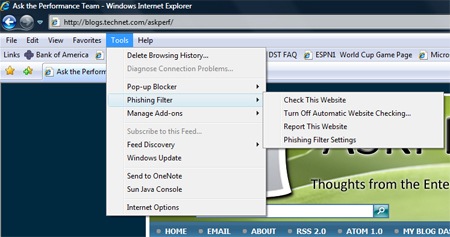
It is important to note that the Phishing Filter is "living" technology - if a user encounters a site that they believe should be flagged, then they can report it to Microsoft using the Tools --> Phishing Filter --> Report this website option in the IE Menus. Conversely, if a user believes that a site should not be marked as a phishing site, they can report this as well. Owners / Site Administrators can also request that their site is removed from the list of known phishing sites. In each of these instances, the site is reviewed on an individual basis.
At the recent RSA conference in San Francisco, we reported that since the launch of IE7 in October, the Phishing Filter has blocked more than 10 million attempts to visit known phishing websites, and is currently experiencing a rate of over 1 million blocks a week. Between IE7 users and the data providers used by the Phishing Filter services, nearly 10,000 Phishing sites are added every week(IE7 at RSA San Francisco).
And that's an overview of the Phishing Filter. Hopefully this will help you understand a bit more about phishing, and how to safeguard against phishing attacks, as well as introduce you to some of the tools at your disposal to combat would-be phishers.
Additional resources:
- Microsoft Anti-Phishing Technology Overview
- Microsoft Anti-Phishing Whitepaper
- Anti-Phishing Guidance for Small Businesses
- Principles behind the IE7 Phishing Filter
- User Privacy and the Phishing Filter
- Jefferson Wells Audit of the Phishing Filter and User Privacy
- Carnegie-Mellon independent study of the Phishing Filter Accuracy
- 3Sharp LLC's study of the Accuracy of the Phishing Filter
- Phishing (Wikipedia page)
- Anti-Phishing Working Group
