Validate user in a trusted domain using ActiveDirectoryMembershipProvider
In web applications, you may come across the situation to validate the users from a trusted domain. This article talks about using Active Directory membership provider in a trusted domain scenario.
Environment
==================
Domain1: lab.com - forest root domain
DC account: lab\Administrator (ADDC2008R2)
Web server account: lab\webserver (Application host server)
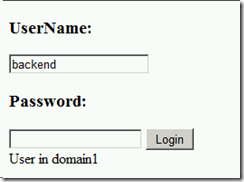
User account: lab\backend
Domain2: yinshi.net - forest root domain
DC account: yinshi\Administrator (AD2DC2008R2)
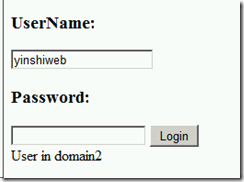
User account: yinshi\yinshiweb
Establish AD domain forest trust
====================
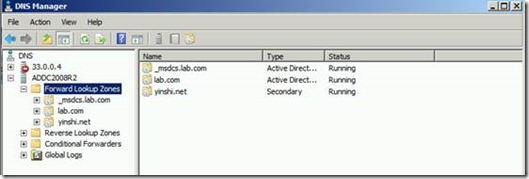
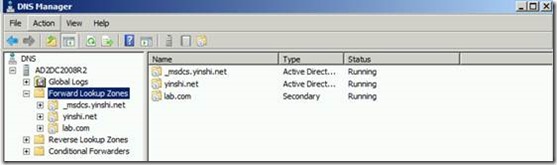
1. Set DNS on two domains’ DC to resolve domain name. DNS secondary zones are configured in each DNS namespace to route queries for names in the other namespace.
lab.com
yinshi.net
2. Create a forest trust
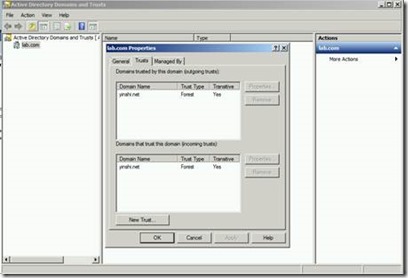
1) Open Active Directory Domains and Trusts on ADDC2008R2 (lab.com)
2) In the console tree, right-click the domain node for the forest root domain, and then click Properties.
3) On the Trust tab, click New Trust, and then click Next.
4) On the Trust Name page, type the DNS name (or NetBIOS name) of another forest, and then click Next.
5) On the Trust Type page, click Forest trust, and then click Next.
6) On the Direction of Trust page, create a two-way, forest trust. Users in this forest and users in the specified forest can access resources in either forest.
7) Continue to follow the wizard. A trust has been established as below.
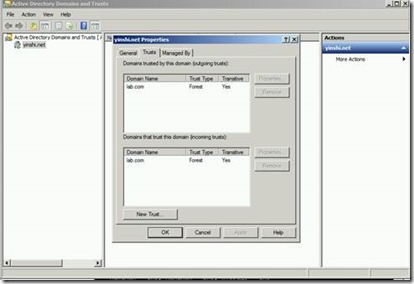
Meanwhile, open Active Directory Domains and Trusts on AD2DC2008R2 (yinshi.net). In the console tree, right-click the domain node for the forest root domain, and then click Properties. On the Trust tab, the trust has also been added as below.
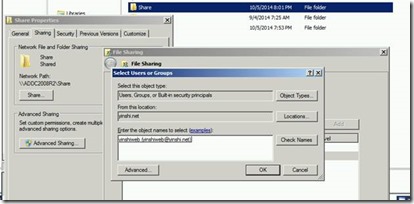
Now we can access the share folder hosted on Domain2 (yinshi.net) from Domain1 (lab.com). We can get domain2 (yinshi.net) user information.
Access to application from different trusted domain
====================
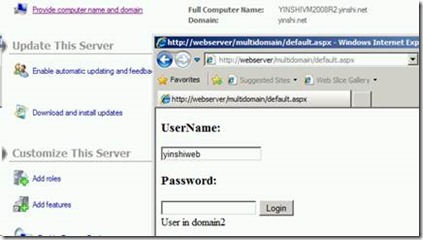
Here I created a simple test web application using ActiveDirectoryMembership Provider. The application is hosted in a web server in Domain1 (lab.com).After entering the username (without domain name) and password, a message will show the user domain.
1. In the Web.config file, add connection strings point to your Active Directory user database for each domain.
2. In the Web.config file, configure the <membership> element with ActiveDirectoryMembershipProvider instances pointing to each domain.
//web.config
<?xml version="1.0"?>
<configuration>
<appSettings />
<connectionStrings >
<add name="ADConnectionString" connectionString="LDAP://lab.com/CN=Users,DC=lab,DC=com" />
<add name="AD2ConnectionString" connectionString="LDAP://yinshi.net/CN=Users,DC=yinshi,DC=net" />
</connectionStrings>
<system.web>
<compilation debug="true">
</compilation>
<!--
The <authentication> section enables configuration
of the security authentication mode used by
ASP.NET to identify an incoming user.
-->
<authentication mode="Windows" />
<!--
The <customErrors> section enables configuration
of what to do if/when an unhandled error occurs
during the execution of a request. Specifically,
it enables developers to configure html error pages
to be displayed in place of a error stack trace.
<customErrors mode="RemoteOnly" defaultRedirect="GenericErrorPage.htm">
<error statusCode="403" redirect="NoAccess.htm" />
<error statusCode="404" redirect="FileNotFound.htm" />
</customErrors>
-->
<membership>
<providers>
<add name="MyADMembershipProvider" type="System.Web.Security.ActiveDirectoryMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" connectionStringName="ADConnectionString" attributeMapUsername="SAMAccountName" connectionUsername="lab.com\Administrator" connectionPassword="<password1> "/>
<add name="MyAD2MembershipProvider" type="System.Web.Security.ActiveDirectoryMembershipProvider, System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" connectionStringName="AD2ConnectionString" attributeMapUsername="SAMAccountName" connectionUsername="yinshi.net\Administrator" connectionPassword="<password2>"/>
</providers>
</membership>
</system.web>
</configuration>
3. Validate the user with the membership system.
//default.aspx
strUsername = UserName.Text;
strPassword = Password.Text;
if (Membership.Providers["MyADMembershipProvider"].ValidateUser(strUsername, strPassword))
{
msg.Text = "User in domain1";
}
else if (Membership.Providers["MyAD2MembershipProvider"].ValidateUser(strUsername, strPassword))
{
msg.Text = "User in domain2";
}
else
{
msg.Text = "No user";
}
Deploy the application to IIS on the webserver in Domain1 (lab.com) and access it from a user in Domain2 (yinshi\yinshiweb). We can also ValidateUser successfully.
Note:
Using an Active Directory membership provider should be necessary to configure connection string and provider for each domain.
https://technet.microsoft.com/en-us/library/cc262069(v=office.12).aspx#section2
Best Regards
Yingjie Shi from APAC DSI Team