Azure AppFabric Access Control Service (ACS) v 2.0 High Level Architecture – Web Application Scenario
Azure AppFabric Access Control Service (ACS) is one of the core components for Windows Azure platform. ACS’s main purpose is help outsourcing authentication and identity management functionality to third parties. Currently supported 3rd party identity providers are:
As a developer you can utilize available, familiar to end user, authentication mechanism by configuring (no coding required) your web application and ACS to work together.
End User Experience
End user experience can be described as follows:
- End user tries to navigate to your application, for example, https://yourapp.com.
- End user redirected to https://login.live.com/ and sees familiar to him user interface.
- End user signs in using his Live ID (the one he uses to sign in to his Hotmail account or other Windows Live services).
- End user redirected back to your application, https://yourapp.com, which recognizes him as authenticated user.
High Level Architecture of Azure AppFabric Access Control Service (ACS) v 2.0
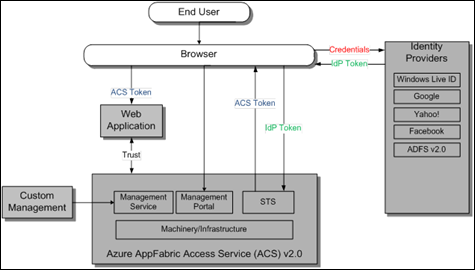
The following diagram outlines the high level architecture of the Azure AppFabric Access Control Service (ACS) v 2.0, its main components and the information exchanged between them. Notice that end user’s credentials never given away to third party.
The sequence of steps, including visual diagram, required to perform the authentication outlined in details here - Introduction (skip to Web Site Scenario).
Notice that the token that is issued by the Identity Provider (green IdP Token on the diagram) is different from the token that the Web Application receives in the end (blue ACS Token on the diagram). Azure AppFabric Access Control Service (ACS) offers claims rules capability that can transform claims. More information on rules here - Rule Groups and Rule Editor.
Summary
- Azure AppFabric Access Control Service (ACS) helps eliminating the burden of creating, maintaining, and managing identity management mechanism.
- By outsourcing authentication developers able to utilize industry strength identity management systems.
- End user is not introduced to new authentication experience – it adds more credibility and confidence and improves user experience.
- End user’s credentials are never given away to third party dramatically reducing the chance of identity theft attacks.
More Info
- Windows Identity Foundation (WIF) Explained – Web Browser Sign-In Flow (WS-Federation Passive Requestor Profile)
- Protocols Supported By Windows Identity Foundation (WIF)
- Windows Identity Foundation (WIF) By Example Part I – How To Get Started.
- Windows Identity Foundation (WIF) By Example Part II – How To Migrate Existing ASP.NET Web Application To Claims Aware
- Windows Identity Foundation (WIF) By Example Part III – How To Implement Claims Based Authorization For ASP.NET Application
- Identity Developer Training Kit
- A Guide to Claims-Based Identity and Access Control – Code Samples
- A Guide to Claims-Based Identity and Access Control — Book Download