Solution Architecture For The Masses. Step 4: Design Your Presentation Layer – Part I
| | Quick Resource Box
| ||||||
| In this post I will be structuring my ASP.NET Web Project following the principles outlined in the Web Application frame:
Authentication & AuthorizationIIdentity and IPrincipal interfaces are the heart of .Net authentication and authorization. All authentication and authorization implementations implement these interfaces. Concrete classes that implement the IPrincipal interface populated with concrete classes that implement IIdentity and stored in HttpContenxt.Current.User where authorization frameworks such RoleManager will look for it. I have not decided where my application will be deployed – Internet, Intranet, or Azure. So the best bet for me in regards to Authentication and Authorization would be to assume this:
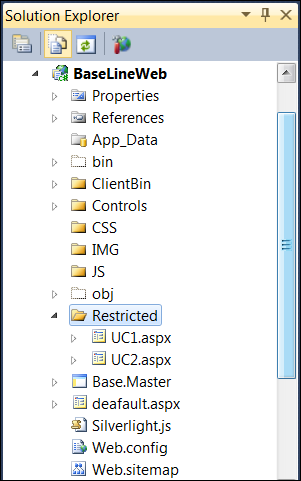
Main decision to make at this point is to structure the project’s folders the way that there is clean separation between restricted pages and resources that do not require authentication and authorization. Following is how my web application is structure in terms of folders: The following folders I have created manually:
Minimum Authorization configuration in Web.Config: <location path="Restricted"> <system.web> <authorization> <deny users="?"/> </authorization> </system.web> </location> From p&p’s ASP.NET 2.0 Internet Security Reference Implementation
There is more to partitioning than SSL [BTW, I’d argue SSL has “a significant overhead” – it does, but less than significant Partitioning to folders fosters authorizing users based on folder names vs. particular pages. Authorizing users to particular pages is bug prone and less secure practice – imagine if someone just copy and pastes SuperSecurePage.aspx to ‘Copy of SuperSecurePage.aspx’ while you authorization configuration was as follows [very bad practice]: <location path="SuperSecurePage.aspx"> <system.web> <authorization> <allow roles="SuperAdmin"/> </authorization> </system.web> </location>Suddenly an attacker has free access to sensitive logic at ‘Copy of SuperSecurePage.aspx’ without being authorized. Concentrate restricted pages into folders and authorized on per folder basis, not per page basis. Another aspect of partitioning the application in separate folders relates to caching, which is next. The summary of my authentication and authorization strategy is:
CachingWhen it comes to caching in distributed web application there are four different types of caching come to mind:
The summary of my decisions regarding Browser caching was made:
More info here ASP.NET Performance: Get Rid of HTTP 401 and HTTP 304. Exception ManagementGeneral guidelines from Chapter 15: Web Application Archetype:
As per How To: Design Exception Management the key considerations of detecting [catching] exceptions are:
The strategy for handling such unhandled exceptions is:
The summary of the my exception handling strategy:
For now this is what I have in my Visual Studio project regarding exception handling: Global.asax: protected void Application_Error(object sender, EventArgs e) { Exception ex = Server.GetLastError().GetBaseException(); string message = ex.ToString(); Tracing.TraceMessage(message); EventsServices.PublishException("GLOBAL ERROR HANDER: " + message); Server.ClearError(); Response.Redirect("GenericErrorPage.htm"); } Notice EvenstServices and Tracing classes I use – I utilize previously implemented logging mechanism. Web.Config [make sure you have created GenericErrorPage.htm]: <customErrors mode="RemoteOnly" defaultRedirect="GenericErrorPage.htm"> </customErrors> Logging & InstrumentationLogging is implemented in previous step. In previous section I have used it to publish and log an exception caught in global error handler. Since it is based on built-in ASP.NET health monitoring the following section needed to be added to Web.Config: <healthMonitoring> <eventMappings> <add name="Exception Event" type="WebEvents.ExceptionEvent"/> </eventMappings> <rules> <add name="Exception" eventName="Exception Event" provider="EventLogProvider" minInterval="00:00:01"/> </rules> </healthMonitoring>
It reads as follows:
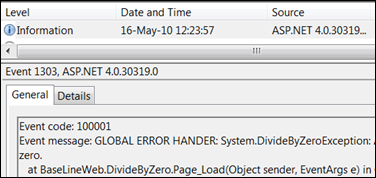
Anytime a code similar to the following code runs: EventsServices.PublishException(“Some Message”);I should observe it in Event Log. Here an example for division by zero caught by global error handler:
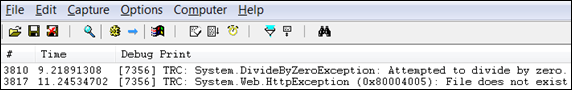
Instrumentation is performed by Tracing.TraceMessage(message). I have already used it in global error handler [look in the example above]. The results it produces observed using DebugView:
Other categories of Web Application frame will be discussed in the next part. Stay tuned. Related Books | |||||||