Identity Flow Through Physical Tiers - Delegation
If these articles:
- How To: Implement Kerberos Delegation for Windows 2000
- How To: Use Impersonation and Delegation in ASP.NET 2.0
- Credentials and Delegation
are your friends then do not waste your time on this post, please.
I have still the same scenario - user sits behind her machine A and access simple ASPX page on box B that access file on share on box C
In previous posts:
- Identity Flow Through Physical Tiers - Impersonation - access failed.
- Identity Flow Through Physical Tiers - the network resource was accessed under App process account.
This time I really want to access the file on share (box C) under end user's account, e.g. flow end user's identity 2 hops - from end user's machine A to web server B and then to the file share - box C.
That is Delegation.
To enable delegation there is a need to accomplish the following:
1. Everything that was needed for impersonation (configure IIS and web.config for windows authentication).
2. Mess a bit with Active directory using Active Directory Users and Computers MMC:
-
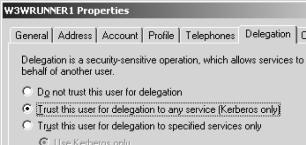
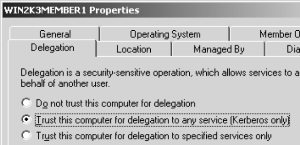
- Configure both App pool account and the Web Server to support delegation:
-
- Since I run my App pool under custom domain account I need to create SPN for it. Keith Brown explains it perfectly in his Credentials and Delegation
iisreset can help sometimes :)
kerbtray (Win2k, Win2k3) can help too to purge Kerberos tickets instead logging off and on.
Also AuthDiag tool is handy too to diagnose Kerberos issues, for example to make sure that my app pool account has SPN defined in AD.
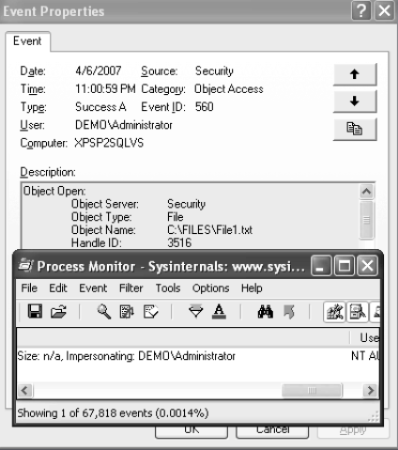
After accessing the page again here is what I have (meaning impersonation works fine):
And the file on the share (box C) is accessed by end user's identity - DEMO\Administrator:
I think it is cool.
How to analyze who access my files - see:
Next post is even cooler - I will walk through Protocol Transition - very similar to Delegation but the end user's security context is created out of thin air without authentication against Active Directory
Huh? Sounds absurd? It did to me when I first discovered it...
Enjoy