Good Chance For Canonicalization Attack When Using Path.Combine()
In my previous post, .Net Assembly Spoof Attack, I've described potential DLL hijacking/spoof attack when using reflection for dynamically loaded assemblies.
Today I was reviewing some project where I stumbled on exactly such case. One thing that caught my eyes was that path to reflected DLL, the one to be loaded dynamically was built like this:
static void Main(string[] args)
{
string dllName = Console.ReadLine();
while (!dllName.Equals("exit"))
{
string path = @"C:\DLLS\"
//BUILD FULL PATH TO ASSEMBLY TO LOAD DYNAMICALLY USING Assembly.LoadFrom
string fullDllPath = Path.Combine(path, dllName);
Console.WriteLine("FULL PATH IS: " + fullDllPath);
dllName = Console.ReadLine();
}
}
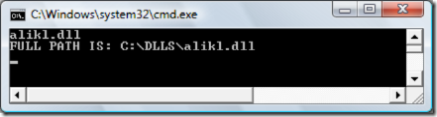
Let me run it and see what happens if I provide expected DLL name say, alikl.dll:
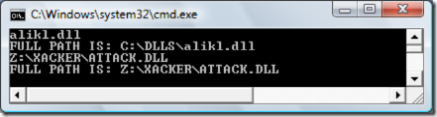
And now let's provide something less expected like Z:\XACKER\ATTACK.DLL:
It means that if we supply full path as second parameter to Combine method it will ignore the first parameter.
How to validate?
1. Check the path for goodness using Path.GetFullPath() comparing result to "C:\DLLS" in our case
2. Sign your assembly and explicitly check it's evidence - example is here .Net Assembly Spoof Attack
More resources:
Canonicalization Lab (includes code and video by Keith Brown)
How To: Protect From Injection Attacks in ASP.NET
Enjoy