Adding/removing members from another forest or domain to groups in Active Directory
Adding/removing members belonging to the same domain from a group is very simple using AD Powershell cmdlets. All you have to do is pass an identifier (either samAccountName, distinguishedName, securityIdentifier or GUID) of the member and group to one of the membership cmdlets:
· Add-ADGroupMember
· Remove-ADGroupMember
· Add-ADPrincipalGroupMembership
· Remove-ADPrincipalGroupMembership
Example:
C:\PS> Add-ADGroupMember SvcAccPSOGroup -Member SQL01, SQL02 ## Adds the user accounts with SamAccountNames SQL01,SQL02 to the group SvcAccPSOGroup.
C:\PS> Remove-ADPrincipalGroupMembership -Identity "Wilson Pais" -MemberOf "Administrators" ## Remove the user 'Wilson Pais' from the administrators group.
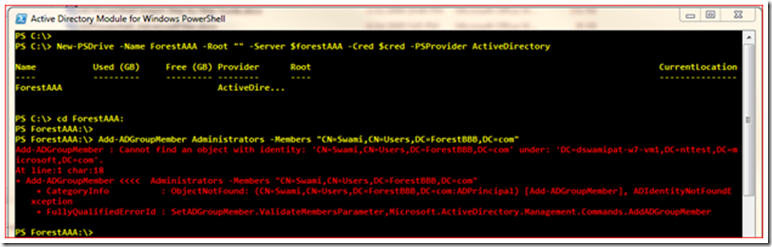
However, when it comes to adding and removing cross-forest or cross-domain members from a group, things become a little difficult. Here is an example of the error message that you would see while trying to do cross-forest/domain operations the regular way:
The issue here is that Add-ADGroupMember cmdlet tries to resolve the identity supplied in its -MemberOf parameter first and then update the group membership. Since the identity supplied in –MemberOf parameter is from ForestBBB the cmdlet fails while trying to resolve the identity against ForestAAA and throws an identity not found exception (ADIdentityNotFoundException).
The correct way to update cross-forest/domain membership is to first fetch the cross-forest/domain object using any of the ADPowershell cmdlets and then supply the fetched object as input to –Members or –MemberOf parameter of the cmdlets.
Example:
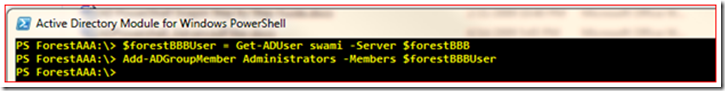
If you want to use Add-ADPrincipalGroupMembership cmdlet then first fetch the group object and save it in a variable and then execute Add-ADPrincipalGroupMembership cmdlet targeting ForestBBB.
Here are the commands that are executed in the screenshots above.
PS ForestAAA:\> $forestBBBUser = Get-ADUser swami -Server $forestBBB
PS ForestAAA:\> Add-ADGroupMember Administrators -Members $forestBBBUser
PS ForestAAA:\>
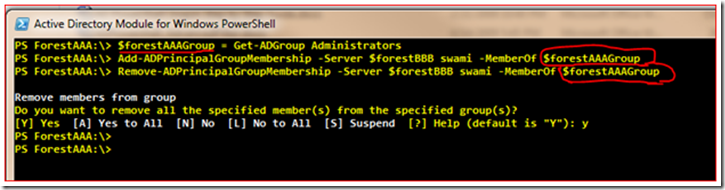
PS ForestAAA:\> $forestAAAGroup = Get-ADGroup Administrators
PS ForestAAA:\> Add-ADPrincipalGroupMembership -Server $forestBBB swami -MemberOf $forestAAAGroup
PS ForestAAA:\> Remove-ADPrincipalGroupMembership -Server $forestBBB swami -MemberOf $forestAAAGroup
Remove members from group
Do you want to remove all the specified member(s) from the specified group(s)?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): y
PS ForestAAA:\>
PS ForestAAA:\>
The reason why the above commands work is that ADPowershell cmdlets stores session information in the objects returned.
The variable $forestBBBUser in the above example contains “server = $forestBBB” in its session information, which is stored internally and is not visible/accessible via command line.
This session information is used by Add-ADGroupMember (and other membership cmdlets) to resolve the identity and add it to the group in $forestAAA.
NOTE: In the above examples I have connected to the forest where the group resides.
Hope this post helps you in managing your group membership via ADPowershell.
Cheers,
Swami
--
Swaminathan Pattabiraman
Developer – Active Directory Powershell Team