XSSDetect Public Beta now Available!
One of the biggest, constant problems we've seen our enterprise customers deal with and we here at Microsoft have to also contend with is that of the XSS (Cross Site Scripting) bug. It's very common and unfortunately, still an issue we have to deal with in many web applications. Internally, the ACE Team has been working on several projects to help mitigate and fix these issues, as well as detect them in the code bases that we review so that they can be fixed before going live.
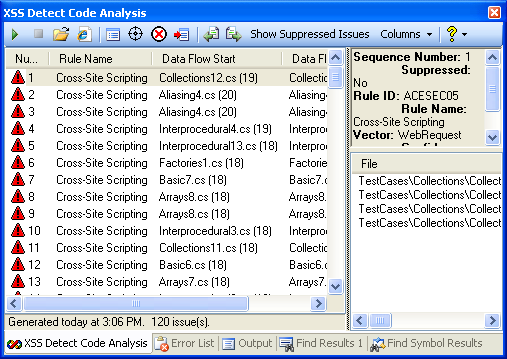
XSSDetect runs as a Visual Studio plug-in and can detect potential XSS issues in managed code.
Here's a screenshot:
While the functionality may seem straight forward, many years of research and hard work have gone into making XSSDetect a reality. XSSDetect is a stripped down version of our enterprise ready Code Analysis Tool for .NET code bases (CAT.NET for short). CAT.NET adds such features as VSTF integration, centralized reporting using web services, customized rulesets and filters, integration with FXCop and MSBUILD as well as the ability to run from the command line to integrate with your build processes (or if you're just old school and rock it like that ;)
XSSDetect is currently in beta so we welcome your feedback! This current version of the beta will expire after 60 days. To send us your feedback, we encourage you to leave comments below or contact us via the 'Email' link above.