Integrating Azure Function with Azure Security Center Playbook
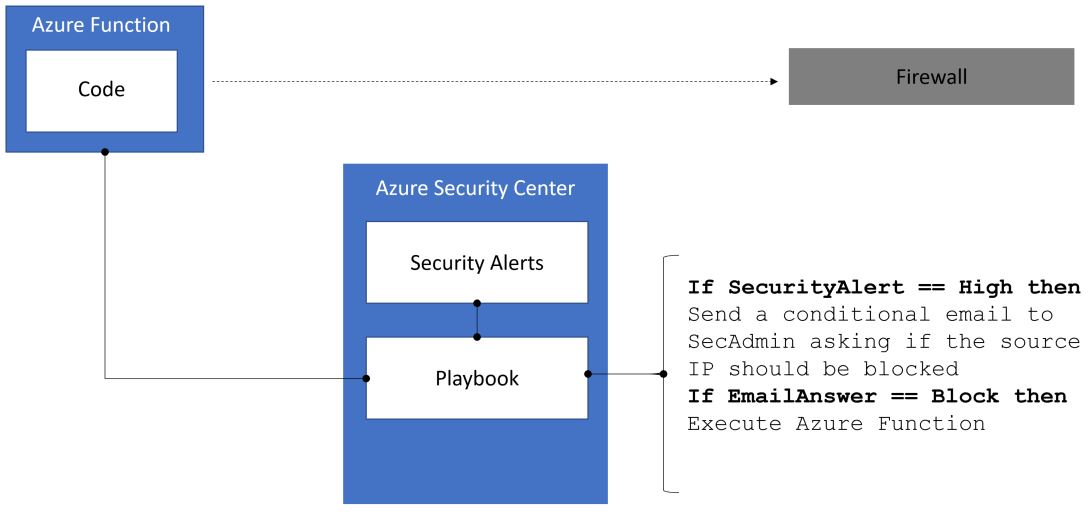
The Playbook feature in Azure Security Center leverages Azure Logic Apps to create a comprehensive workflow that can be used to aggregate a set of procedures to be executed when a certain condition takes place. The demo that I presented at Ignite 2007 shows the integration with Slack, and how the Security Center alert can be easily added to a Slack channel. This is just one example, there are many more, and when you integrate with Azure Functions, the possibilities are gigantic. Let's imagine a scenario where an alert is generated in Security Center, this alert has he attacker's source IP, now you want to quickly create a firewall rule in your edge firewall to block that IP. Is it possible to do that? You bet it is! In this scenario we have the following components:
Part 1 - Creating an Azure Function
Before creating an Azure Function that will be used to add a rule to your firewall, make sure that your firewall support this type of integration. For example, in a Palo Alto Firewall, you can use API Browser (https://<firewall>/api) to change its configuration. The steps below assume that your firewall does support that and it uses C# language.
1. In Azure Portal, click New, and type Function.
2. Click Function App.

3. In the Function App page, click Create.
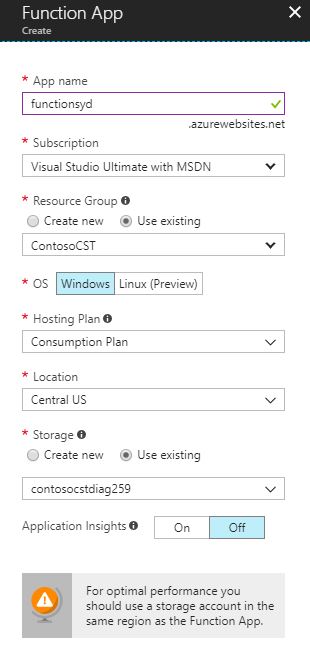
4. Type the required information as shown in the sample below:
5. After finishing creating it, click More services, and type function. Select Function App.
6. Expand your function and click in the plus sign as shown below:
7. In the quick start page, click custom function in the bottom.
8. Click HTTP Trigger option.
9. In the HTTP trigger page, select the language (in this case C#), type the name of the function, change the authorization level to the one appropriated for your deployment, and click Create.
10. Type your code ( dude, aren't you going to give me a sample code? Yes, read this post )
11. Click Save.
Part 2 - Creating a Playbook in Azure Security Center
Use the steps below to create a new playbook in Security Center:
1. Open Security Center dashboard.
2. Under AUTOMATION & ORCHESTRATION, click Playbooks.
3. Click Add Playbook button, and type the requested information about your new playbook, as shown in the example below:
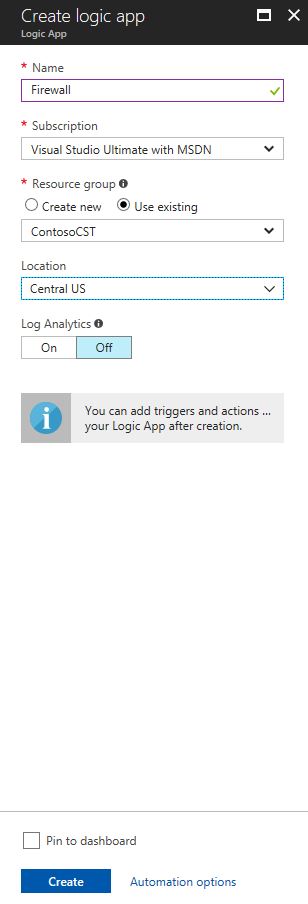
4. Click Create.
5. In the Logic App Templates page, click Blank Logic App.
6. Type Security Center and select the Request trigger.
7. Click New Step and click Add a condition.
8. In the first field select Alert Severity, in the second field select is equal to, and in the third field type High.
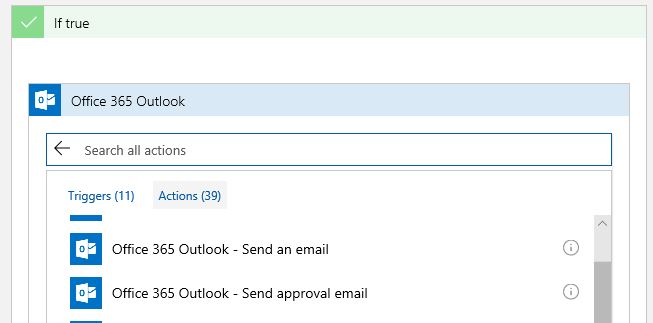
9. In the if true condition, click add Action.
10. Click Office 365 Outlook, and in the actions select Office 365 Outlook - Send an email.
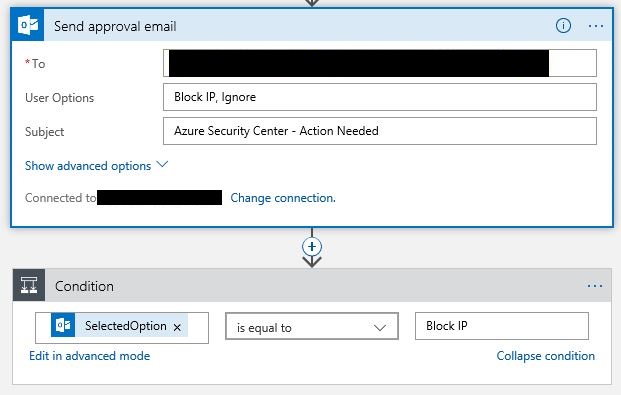
11. Sign in with your Office 365 account, and configure the options as shown below:
12. Notice that are two User Options in this approval email, one is called Block IP and the other is Ignore. Which means that the Security Adminstrator will receive an email with two voting buttons, where he needs to select only one. After that you will need to add the condition, which uses the field SelectOption, and compares with the value that you will type (in this case Block IP).
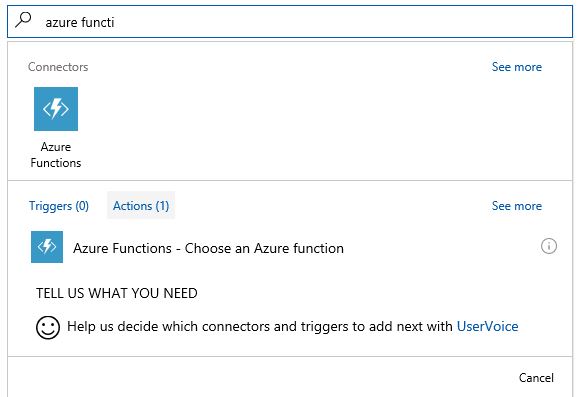
13. Click Add an action under If true, type Azure Function and select Azure Functions.
14. Now that you seleted Azure Functions, you need to select the action, which in this case is the function app that you created previous. For this example is called functionsyd.
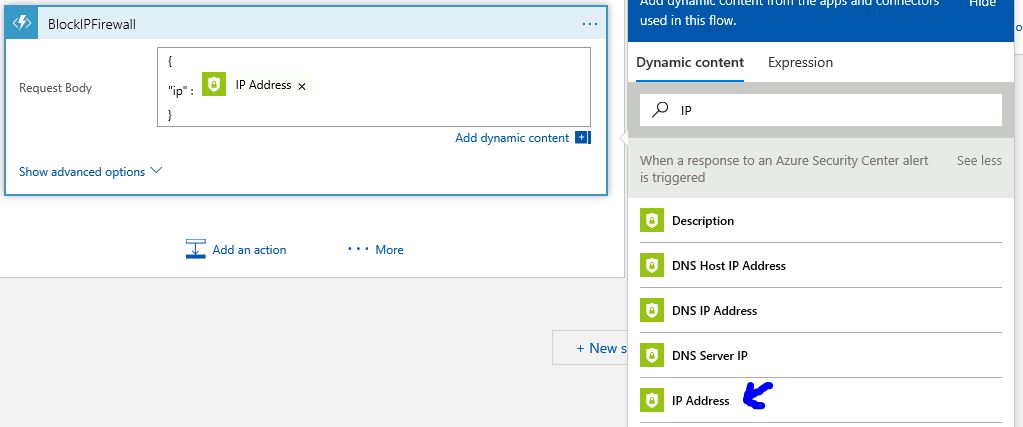
15. Now select the function itself (where the code reside), in this case is called BlockIPFirewall.
16. In the Request Body field, you will type this. Notice that this is very peculiar to the firewall itself, for this example the firewall is expecting the field "ip" as part of the blocking rule creation, and we are passing as parameter the source IP of the attack from Azure Security Center (hence the Security Center icon).
17. Click Save.
Part 3 - Executing the Playbook
To execute the playbook you need to go to Security Alerts in Security Center, select the Alert that has the attack that you want to block the source IP, click on it and click Run Playbook.
General Observations
- Consult your Firewall's documentation to see how to programmatically create rules, the firewall you have may not support this capability.
- Test this procedure in a lab environment.
- Make yourself familiar with Azure Function, because is a very powerful platform that will help you to automate many tasks.
Have fun!