Detecting Persistence in Azure Security Center
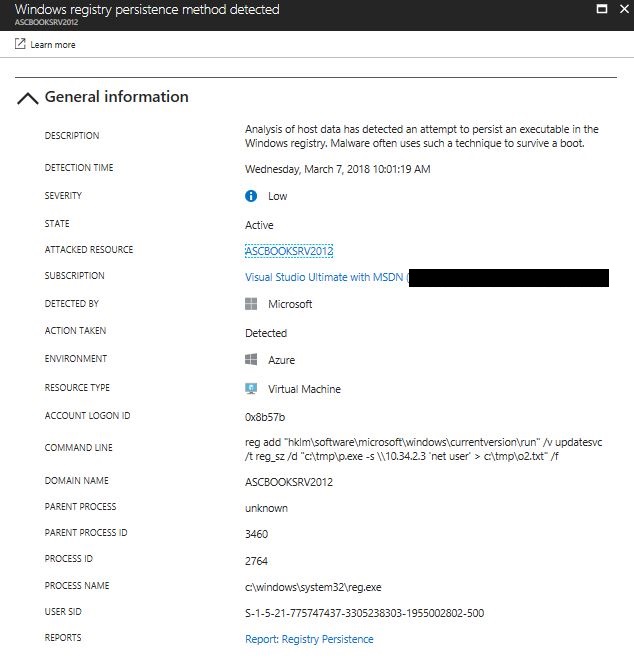
According to Mitre Adversarial Tactics, Techniques & Common Knowledge (ATT&CK), Persistence is "any access, action, or configuration change to a system that gives an adversary a persistent presence on that system", which is a common technique used by adversaries to keep a communication channel open with the attacked resource. The use of Run and RunOnce registry keys to survive a boot is one of those persistence techniques that is widely used for adversaries. For example, Bronze Butler used both keys to estabilish malware persistance. The good news is that Azure Security Center can detect this type of registry change and trigger an alert as shown in the example below:
Read Azure Security Center detection capabilities for more information about how Security Center is able to detect new threats.